- NetWitness Community
- Discussions
- You Need This Hourly Executable Report
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
You Need This Hourly Executable Report
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-03-06 10:19 AM
In all my experience in the field, this report has come in most handy when I arrive to a customer's site and they don't have a Spectrum appliance, and I need to find find malware on the network. The hourly output of this report is manageable by a staff of analysts and it only takes a few minutes to detect the likely malicious EXEs or to add a false positive to the built-in filter.
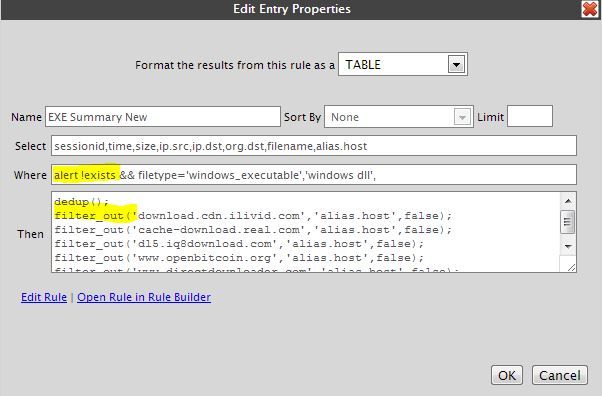
Open Informer and create the following rule:
You need to ensure that the sessionid is included and be sure the sort-by is NONE. My where clause begins where an alert does not exist. I put all of my known intelligence alerts and known threats into this alert key to be processed separately. For this use case I'm only interested in brand new stuff, and this is why I'm ignoring this key. The RSA CSIRC uses a similar method, alerting known intelligence into their own custom key called "monitors." You could do the same, but it involves modifying the index keys on the decoders, concentrators and brokers. The rest of my where clause is pretty straightforward.
The Then statement must begin with the dedup command. Below this are all of the false-positives or known bad sites that I'm tired of looking at on an hourly basis. And remember, you can filter by any of the keys you have in your select statement, but I stick with ip.dst, org.dst and alias.host most often. The filter_out commands are very quick, and can be an exact match, or a contains statement. For instance, if I wanted to filter out 'www.windowsupdate.com' I can use the entire name or just use 'windowsupdate' and the results will be the same. You can likewise filter out all of microsoft by using the org.dst key.
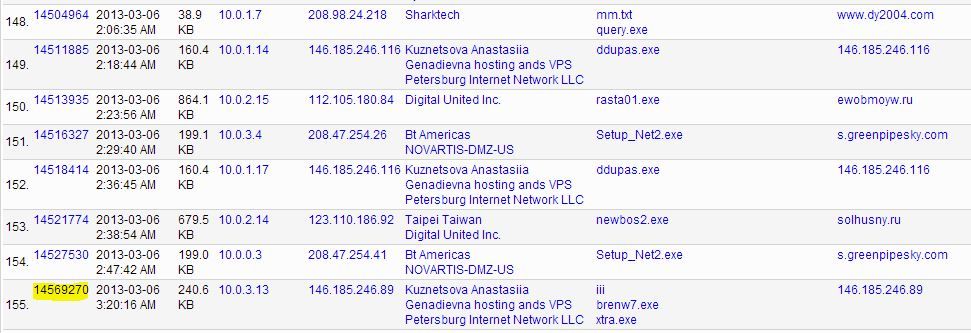
The report output ideally should produce no more than 50 results per hour. Add additional filters as needed to reduce the output to something your analyst can process. This is what the output looks like:
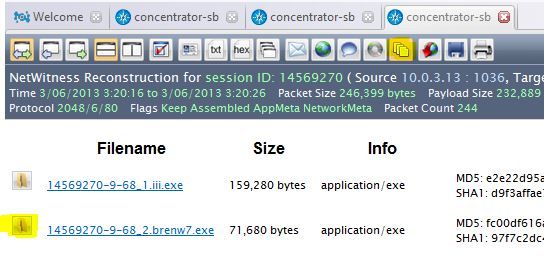
In this example, all of these results are malicious, but I'm interested in the highlighted sessionid. Clicking that will take you directly to the session in Investigator. And then you can click on the file location icon to take you to the location of that file in your local system cache. One quick warning- with malicious files, your local AV may automatically quarantine this file or deny you access to your cache. I disable my AV when investigating malware.
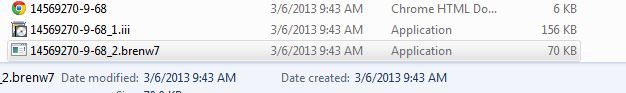
Here is a screenshot of the file in your local cache.
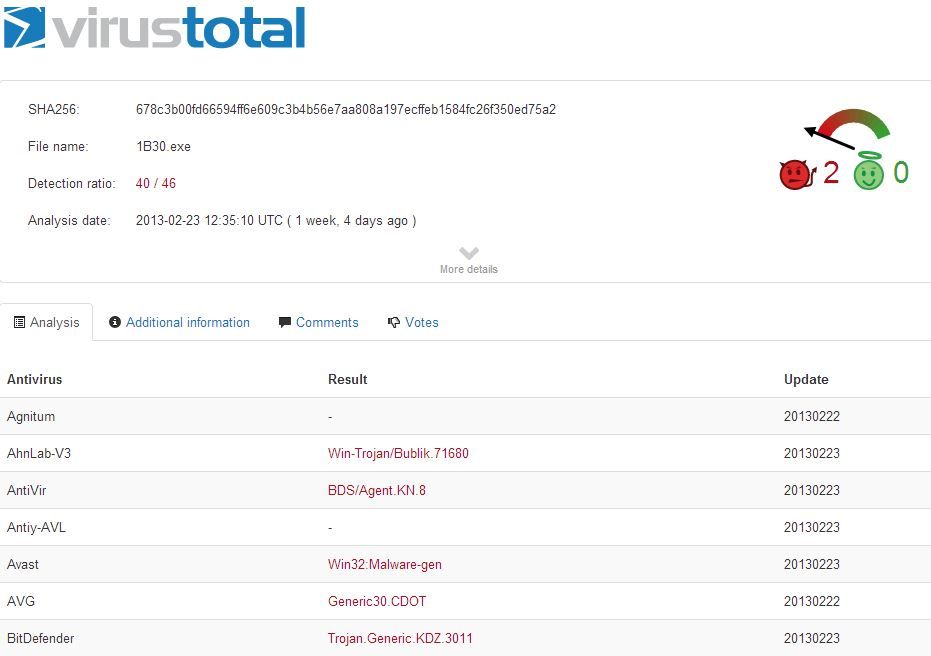
This 70 KB file can now be easily uploaded to VirusTotal or put into your own sandbox for analysis. Below is the VirusTotal results of what turns out to be a new Zeus Variant that also employs a reverse proxy shell into the affected system-
So by using your combination of automating your analysis, filtering out false positives, and reviewing an hourly report, you can keep a pretty tight lookout for emerging malware threats in your environment. It is no substitution for the Spectrum appliance, but it is a good workable solution in a pinch.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-08-25 05:14 PM
Hi Fielder -
In this post you stated, "The RSA CSIRC uses a similar method, alerting known intelligence into their own custom key called "monitors." You could do the same, but it involves modifying the index keys on the decoders, concentrators and brokers."
Can you outline (at least at a high level), the necessary steps to create a custom key like this? Thanks in advance, Tom
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-08-28 11:57 AM
We are actually going to highlight this methodology quite a bit at the SA Summit.
Modifying the index is pretty easy. If you are using SA or the most recent version of 10.x, all changes to the index need to go into index-custom.xml on the decoder, concentrator and broker.
If you want to make a custom key to alert values into, whether it is for normalization, targeted alerts, etc, you simply paste the following to the bottom of your index-custom.xml file before the closing /language key:
<key description="My Soc Monitors" level="IndexValues" name="soc.monitor" valueMax="100000" defaultAction="Open"/>
The description should be any human readable term, and this is what will show up in Investigator as the key name. The real key name is the soc.monitor and that should be used to run queries against this key. Be sure to use a unique key name.
Hope this helps.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-08-28 07:05 PM
Thanks Fielder -
Any insights if I'm using 9.8.5.5? Our environment is small enough that we don't have a broker, so all I need is how to tackle this on the decoder and the concentrator. I don't see an index-custom.xml file... can I just make the changes in the index-concentrator.xml and/or the index-decoder.xml? Again, any/all insights are greatly appreciated. Tnx, Tom
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-08-29 05:17 AM
On NextGen the files are called "index-concentrator.xml" and "index-decoder.xml" respectively. The key name needs to be 16 characters or less. You need to restart the services when making changes to index files.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-08-29 06:53 PM
Thanks for the insights Johannes! Between yours and Fielder's advice, here is what I came up with on NextGen...
In index-decoder.xml I added the following line:
<key description="My Soc Monitors" format="Text" level="IndexNone" name="soc.monitor" valueMax="100000" />
In index-concentrator.xml I added the following line:
<key description="My Soc Monitors" format="Text" level="IndexValues" name="soc.monitor" valueMax="100000" defaultAction="Open" />
Note especially that (a) I had to add the format directive to each, and (b) for the index-decoder.xml I had to switch the level to "IndexNone".
Once I restarted the nwdecoder and nwconcentrator services, I was able to create app rules to alert to the soc.monitor key, and after testing the rule, the indexed meta showed up in Investigator as expected.
So one last question on this topic... in Investigator, although the indexed key did show up, I was hoping it would show up first/on top (i.e. before the Alerts meta); I tried to accomplish this by adding the index-concentrator.xml line near the top of file. That said, the custom key showed up pretty far down the screen (so the analyst has to scroll down to see it)... just wondering if there is a way to specify that this key should be the first meta field within Investigator?
Any/all insights are greatly appreciated. Tnx, Tom
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-08-30 03:39 AM
Investigator has it's own index file - aptly named index-investigator.xml. It's in the ProgramData folder. If you copy your custom lines to this file too, the keys appear at the respective position. This also allows you to move the position under Edit -> Options -> Reports.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-08-30 04:18 PM
Awesome, thanks Johannes... that did the trick!
Best, Tom