- NetWitness Community
- Blog
- Health & Wellness uses an old IP for connecting to a device - How to Resolve
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Health and Wellness leverages RabbitMQ to be able to collect the actual status of any components of the RSA Netwitness platform. After changing an IP on a component the Health and Wellness keep communicating with the previous IP. To be able to resolve this issue you need to do the following:
Open your browser and log in to the RabbiMQ Management interface: https://IP_of_your_head_unit:15671
Log in using the deploy_admin account
When logged in, go to the Admin Tab
And in the Admin Tab, Select the Federation Upstreams on the right
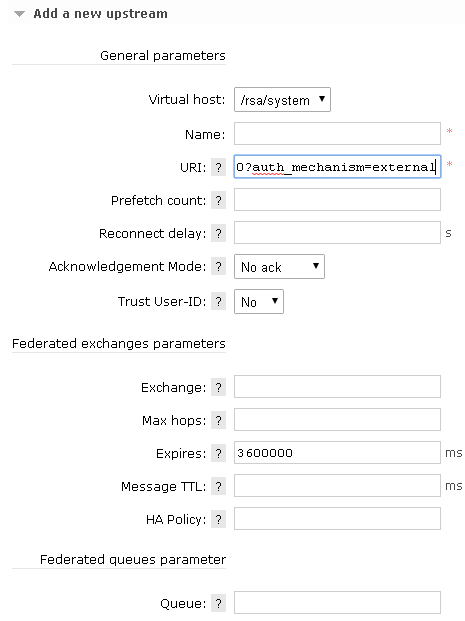
Identify the wrong upstream and take note of the virtual host, URI, Expires and the Name of this upstream
Create a new upstream and enter the right information for the URI, with the new IP, the Name, the Virtual Host and the Expires:
When adding this new upstream, it will match the upstream name and automatically replace the one with the wrong information.
And now the device is in a ready state and the health status changed from RED to GREEN
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Using NetWitness to Detect Phishing reCAPTCHA Campaign
- Netwitness Platform Integration with Amazon Elastic Kubernetes Service
- Netwitness Platform Integration with MS Azure Sentinel Incidents
- Netwitness Platform Integration with AWS Application Load Balancer Access logs
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- New HotFix: Addresses Kernel Panic After Upgrading to 12.4.1
- Automation with NetWitness: Core and NetWitness APIs
- HYDRA Brute Force
- DDoS using BotNet Use Case
-
Announcements
64 -
Events
12 -
Features
12 -
Integrations
15 -
Resources
68 -
Tutorials
32 -
Use Cases
31 -
Videos
119