- NetWitness Community
- Blog
- RSA Threat Content mapping with MITRE ATT&CK™
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Introduction to MITRE ATT&CK™
Adversarial Tactics, Techniques, and Common Knowledge (ATT&CK™) for enterprise is a framework which describes the adversarial actions or tactics from Initial Access (Exploit) to Command & Control (Maintain). ATT&CK™ Enterprise deals with the classification of post-compromise adversarial tactics and techniques against Windows™, Linux™ and MacOS™.
This community-enriched model adds techniques used to realize each tactic. These techniques are not exhaustive, and the community adds them as they are observed and verified.
To read more about how ATT&CK™ is helpful in resolving challenges and validate our defenses, please check this article.
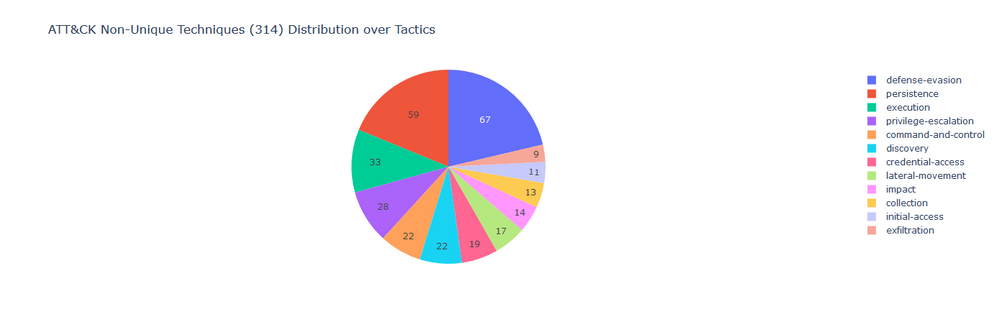
Some Techniques are mapped to multiple Tactics. There are total 244 unique Techniques which results in 314 Non-unique Techniques distributed over 12 Tactics.
RSA Threat Content Mapping with MITRE ATT&CK™
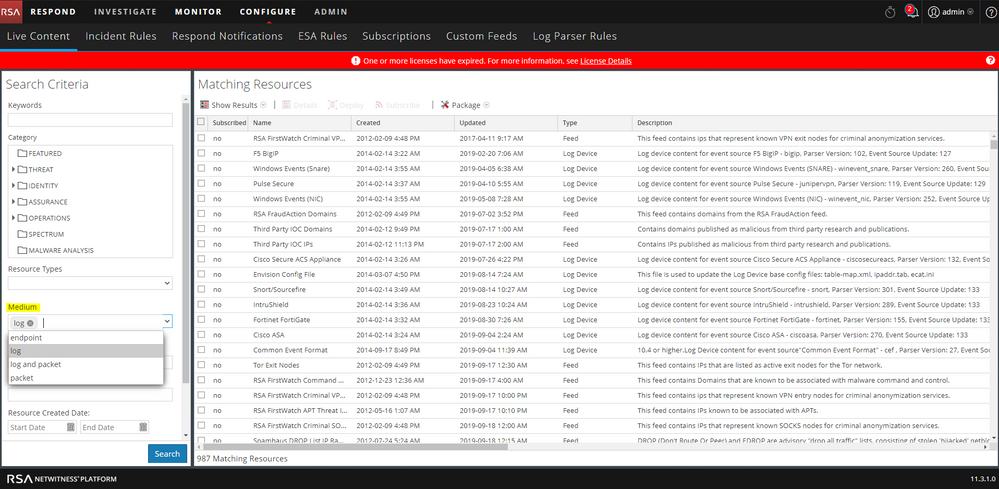
RSA has mainly three kinds of Threat Content: a. Application Rules, b. ESA Rules and c. LUA Parsers.These content types can be classified further as per the 'Medium' of each piece of content. Medium depends upon the source of the meta that particular content piece is using. For example: An application rule if using meta populated by packet data then its Medium will be packet. We can search LIVE content using Medium criteria:
We will try to measure how much ATT&CK™ matrix is covered by RSA Threat Content. Essentially mapping each piece of threat content to one or multiple ATT&CK™ techniques it detects. This mapping needs to be saved in a file and in case of ATT&CK™ the file type will be JSON. For example: In case of application rules, there will be mapping JSON files for each of the following:
- Mapping of only RSA Application Rules with Medium = log
- Mapping of only RSA Application Rules with Medium = packet
- Mapping of only RSA Application Rules with Medium = endpoint
- Mapping of only RSA Application Rules with Medium = log AND packet
- Mapping of all RSA Application Rules (Without considering Medium)
The same pattern will follow for ESA Rules and LUA Parsers depending upon Medium value.
This JSON is graphically viewable through ATT&CK™ Navigator web GUI tool which is described later in this post with the process of observing the GUI.
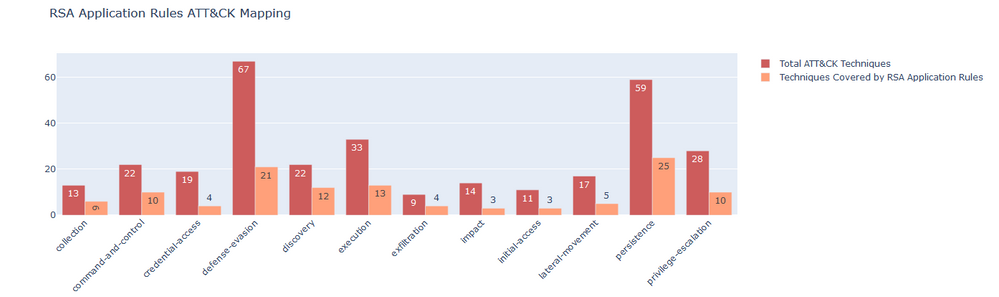
a. Application Rules - The Rule Library contains all the Application Rules and we can map these rules or detection capabilities to the tactics/techniques of ATT&CK™ matrix. The mapping shows how many Tactics/Techniques are detected by RSA NetWitness Application Rules. We have generated JSON files for application rules which can be viewed in Navigator. This JSON can be downloaded from attached archive in this blog post. Following are the mappings for RSA Application Rules:
| Content Type | Medium | Location of JSON in attached archive |
|---|---|---|
| RSA Application Rules | log | RSA_Threat_Content_ATTACK_JSON_Mapping\Application_Rules\Medium_log |
| RSA Application Rules | packet | RSA_Threat_Content_ATTACK_JSON_Mapping\Application_Rules\Medium_packet |
| RSA Application Rules | endpoint | RSA_Threat_Content_ATTACK_JSON_Mapping\Application_Rules\Medium_endpoint |
| RSA Application Rules | All Rules(Without considering Medium) | RSA_Threat_Content_ATTACK_JSON_Mapping\Application_Rules\All_RSA_Application_Rules |
Following is the plot which reflects number of techniques detected by all RSA Application Rules with respect to ATT&CK™:
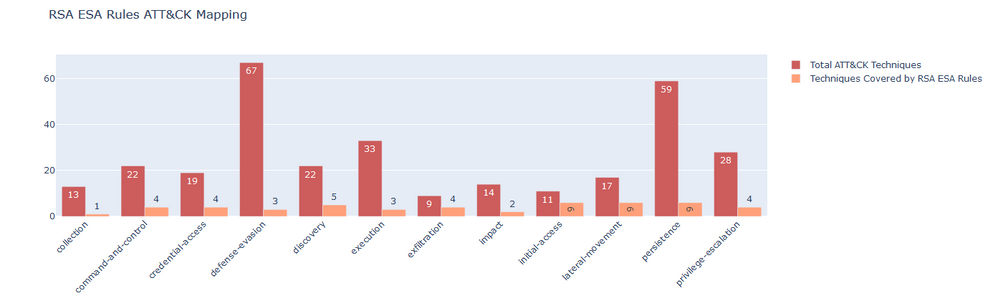
b. ESA Rules - ESA is one of the defense systems that is used to generate alerts. ESA Rules provide real-time, complex event processing of log, packet, and endpoint meta across sessions. ESA Rules can identify threats and risks by recognizing adversarial Tactics, Techniques and Procedures (TTPs). We have generated JSON files for ESA rules which can be viewed in Navigator. This JSON can be downloaded from attached archive in this blog post. Following are the mappings for RSA ESA Rules:
| Content Type | Medium | Location of JSON in attached archive |
|---|---|---|
| RSA ESA Rules | log | RSA_Threat_Content_ATTACK_JSON_Mapping\ESA_Rules\Medium_log |
| RSA ESA Rules | packet | RSA_Threat_Content_ATTACK_JSON_Mapping\ESA_Rules\Medium_packet |
| RSA ESA Rules | log AND packet | RSA_Threat_Content_ATTACK_JSON_Mapping\ESA_Rules\Medium_log_AND_packet |
| RSA ESA Rules | All Rules(Without considering Medium) | RSA_Threat_Content_ATTACK_JSON_Mapping\ESA_Rules\All_RSA_ESA_Rules |
Following is the plot which reflects number of techniques detected by all RSA ESA Rules with respect to ATT&CK™:
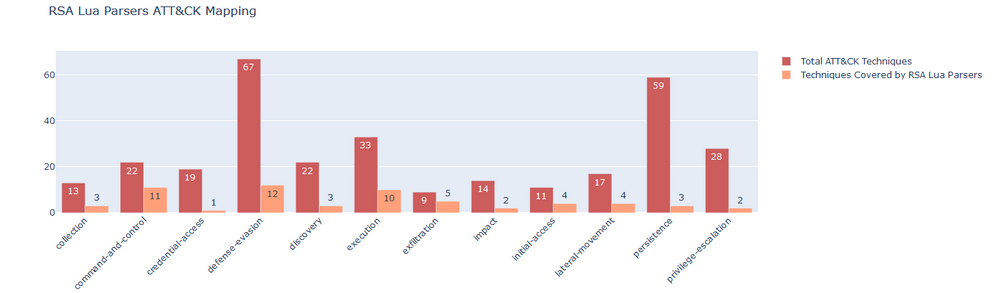
c. LUA Parsers - Packet parsers identify the application layer protocol of sessions seen by the Decoder, and extract meta data from the packet payloads of the session. Every packet parser is able to extract meta from every session. One of these packet parsers are LUA Parsers which can be customized by customers. We have generated JSON files for LUA Parsers which can be viewed in Navigator. This JSON can be downloaded from attached archive in this blog post. Following are the mappings for RSA LUA Parsers:
| Content Type | Medium | Location of JSON in attached archive |
|---|---|---|
| RSA LUA Parsers | packet | RSA_Threat_Content_ATTACK_JSON_Mapping\Lua_Parsers\Medium_packet |
| RSA LUA Parsers | All LUA Parsers(Without considering Medium) | RSA_Threat_Content_ATTACK_JSON_Mapping\Lua_Parsers\All_RSA_Lua_Parsers |
Note: The above two JSONs will be same as for LUA Parsers the only Medium is packet.
Following is the plot which reflects number of techniques detected by all RSA LUA Parsers with respect to ATT&CK™:
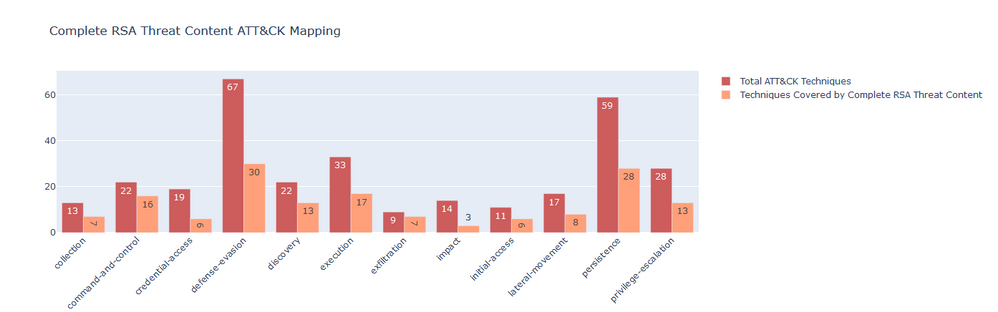
d. Complete RSA Threat Content (Application Rules + ESA Rules + Lua Parsers) - We have combined all three type of contents and created a combined JSON file for ATT&CK™ Navigator and can be downloaded from this blog post.
| Content Type | Medium | Location of JSON in attached archive |
|---|---|---|
| RSA Threat Content | All RSA Threat Content | RSA_Threat_Content_ATTACK_JSON_Mapping\All_RSA_Threat_Content |
Following is the plot which reflects number of techniques detected by all three threat content types combined with respect to ATT&CK™ coverage :
Although these statistics are bound to change with time as new content is added or updated. We can update ATT&CK™ coverage periodically which will help us to give us a consolidated picture of our complete defense system and thus we can quantify and monitor the evolution of our detection capabilities.
In above sections, we have talked about using JSON files (attached with blog post) in ATT&CK™ Navigator . In next section, we will discuss how to use and observe the JSON files.
Introduction to MITRE ATT&CK™ Navigator
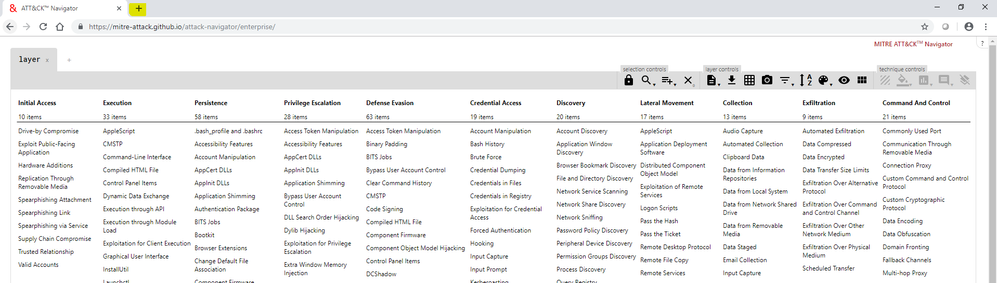
ATT&CK™ Navigator is a tool openly available through GitHub which uses the STIX 2.0 content to provide a layered visualization of ATT&CK™ model.
ATT&CK™ Navigator stores information in JSON files and each JSON file is a layer containing multiple techniques which can be opened on Navigator web interface. The JSON contains content in STIX 2.0 format which can be fetched from a TAXII 2.0 server of your own choice. For example, we can fetch ATT&CK™ content from MITRE's TAXII 2.0 server through APIs.
The techniques in this visualization can be:
- Highlighted with color coding.
- Added with a numerical score to signal severity/frequency of the technique.
- Added with a comment to describe that occurrence of technique or any other meaningful information.
These layers can be exported in SVG and excel format.
How to View a JSON in ATT&CK™ Navigator?
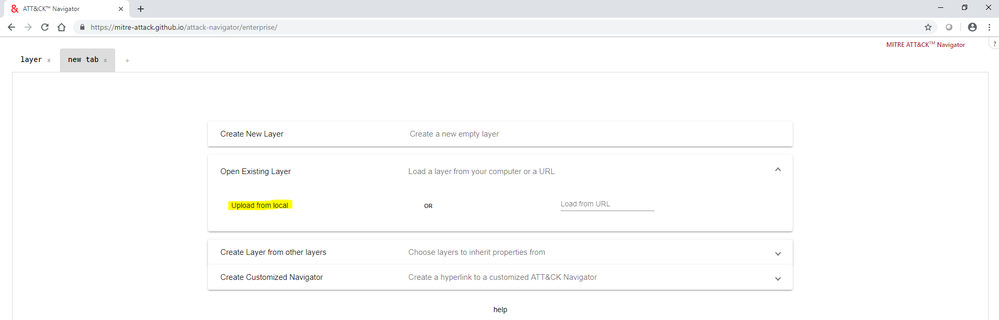
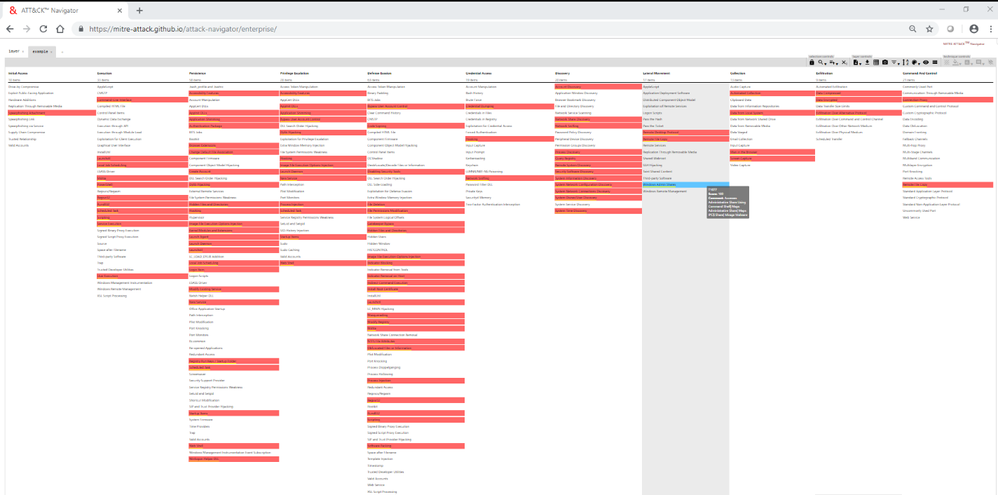
- Open MITRE’s ATT&CK™ Navigator web application. (https://mitre-attack.github.io/attack-navigator/enterprise/).
- In Navigator, open a New Tab through clicking '+' button.
- Then click on 'Open Existing Layer' and then 'Upload from Local' which will let you choose a JSON file from your local machine (or, the one attached later in this blog).
- After uploading JSON file the layer will be opened in Navigator and will look like this:
This visualization highlights the techniques covered in the JSON file with color and comments.
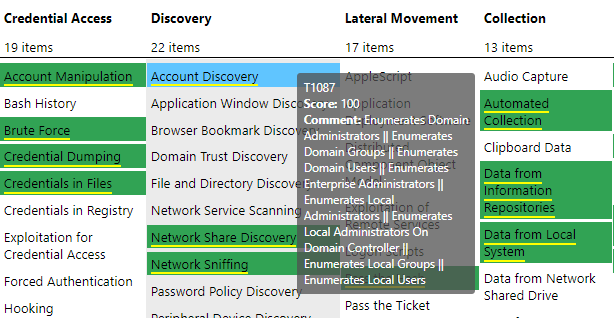
5. While hovering mouse over each colored technique you can see three things:
- Technique ID: Unique IDs of each technique as per ATT&CK™ framework.
- Score: Threat score given to each technique.
- Comment: We can write anything related in comment to put things in perspective. In this case, we have commented pipes (‘||’) delimited names of content/rules/parsers which cover that technique. For example, if you have opened application rule JSON then comments will contain pipes delimited name of those application rules which detect hovered technique.
Other blog posts written before regarding Threat Content coverage of ATT&CK™ can be found here and here.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Using NetWitness to Detect Phishing reCAPTCHA Campaign
- Netwitness Platform Integration with Amazon Elastic Kubernetes Service
- Netwitness Platform Integration with MS Azure Sentinel Incidents
- Netwitness Platform Integration with AWS Application Load Balancer Access logs
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- New HotFix: Addresses Kernel Panic After Upgrading to 12.4.1
- Automation with NetWitness: Core and NetWitness APIs
- HYDRA Brute Force
- DDoS using BotNet Use Case
-
Announcements
64 -
Events
12 -
Features
12 -
Integrations
15 -
Resources
68 -
Tutorials
32 -
Use Cases
31 -
Videos
119