- NetWitness Community
- Discussions
- Ampersanding Overflows and How to Detect Them
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Ampersanding Overflows and How to Detect Them
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-05-30 04:31 PM
Over the past few days I've noticed a trend on UrlQuery that shows scores of Ampersanded commands in the web queries. These ampersanded commands are intended to run a query, but by flooding the web browser with the commands it may be possible to inject an IFRAME into some browsers. Check out this search parameters for "&amp" at UrlQuery here.
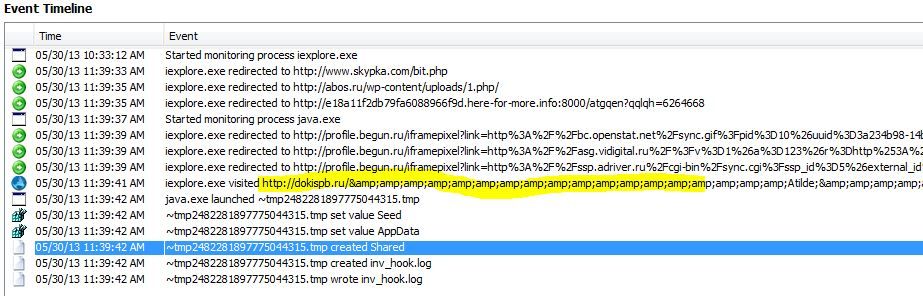
I visited one of these sites with an Invincea protected web browser to see if I would be exploited. I was. Here is the event timeline.
In this instance, a process and a local share was injected via a single pixel IFRAME. Other sites with similar ampersanded queries lead to blackhole exploits, toolbar downloads or other malware delivery.
The good news is that Security Analytics / NetWitness can easily detect these ampersanded overflows. Just create a new capture rule on the decoders. Name the Rule "Ampersanding Overflow WebQuery"
Rule Contents are: query contains '&'
Good Luck and Happy Hunting!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-06-05 03:56 AM
Hey I got alerts triggered for the same rule ![]()
Could you please brief on the action needed for these kind of alerts. I am not sure to which all team I need to contact for it.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-06-05 10:35 AM
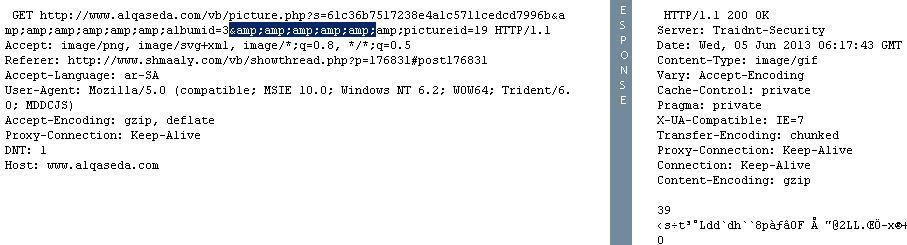
This one actually looks normal. It looks like a poorly coded insertion of a photo in a news article. What you are looking for are dozens of these in the query along with 'Atilde'- which is url code for '~'
Check out the urlquery link above for the examples.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-06-23 03:26 AM
Yeah I found dozens for amp on the query.
Would you suggest me what action I have to take?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-06-24 04:29 AM
Please also post the preliminary results of your analysis. What's your general approach when you see "strange" URLs in Netwitness? You should at least be able to answer those questions:
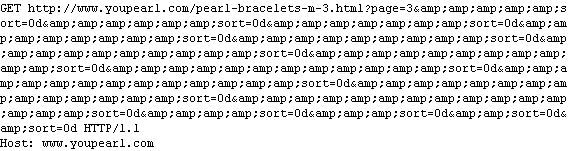
- What led the GET request? Did a malicious site redirect there? Was it a link in a phishing mail? Or was it normal web browsing originating from www.youpearl.com? If it was the latter, can you reproduce the long query?
- Is the domain "youpearl.com" suspicious? Is it blacklisted? Who registered the domain and when?
- How is the query generated? Do you find code that concatenates a large number of "&"s ?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-06-24 08:59 AM
Yes you are right.
I did the initial analysis on the domain, did not get get anything bad reputation on it. I did not find any code that concatenates a large number of "&". On my analysis I did not find anything suspicious.
Just a curiosity to know any abnormal from above screenshot. as previous comments of , it was mentioned that the query will contain 'Atilde'. On this case "'Atilde'" was not there between "@amp".
I was asking for action because this will not relate to source hosts infection. So if I found it what would be corrective actions.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-06-24 09:47 AM
Yeah Youpearl seems like a legit site. Remember the multiple ampersanding is just a way to join multiple queries. Since this site has a merchant front end, this seems to be legit, although poorly coded, and the query also does not call for directory traversals or iframe injections.