- NetWitness Community
- Discussions
- Can we create nested rule in RSA Netwitness Packets and logs?
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Can we create nested rule in RSA Netwitness Packets and logs?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-01-10 05:00 AM
I want to create rule which will take output from one rule and use it in a new rule.
***********************************************************
Rule 1-
Select
event.time, ip.src, country.src, ip.dst, ip.dstport, action, event.desc
Where
event.desc contains "scanner" && device.class != 'Anti Virus'
Rule 2-
Select
event.time, ip.src, country.src, ip.dst, ip.dstport, action, event.desc
Where
ip.src = (Source IP address from Rule 1 output)
*********************************************************
Hope that is clear.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-01-10 08:10 AM
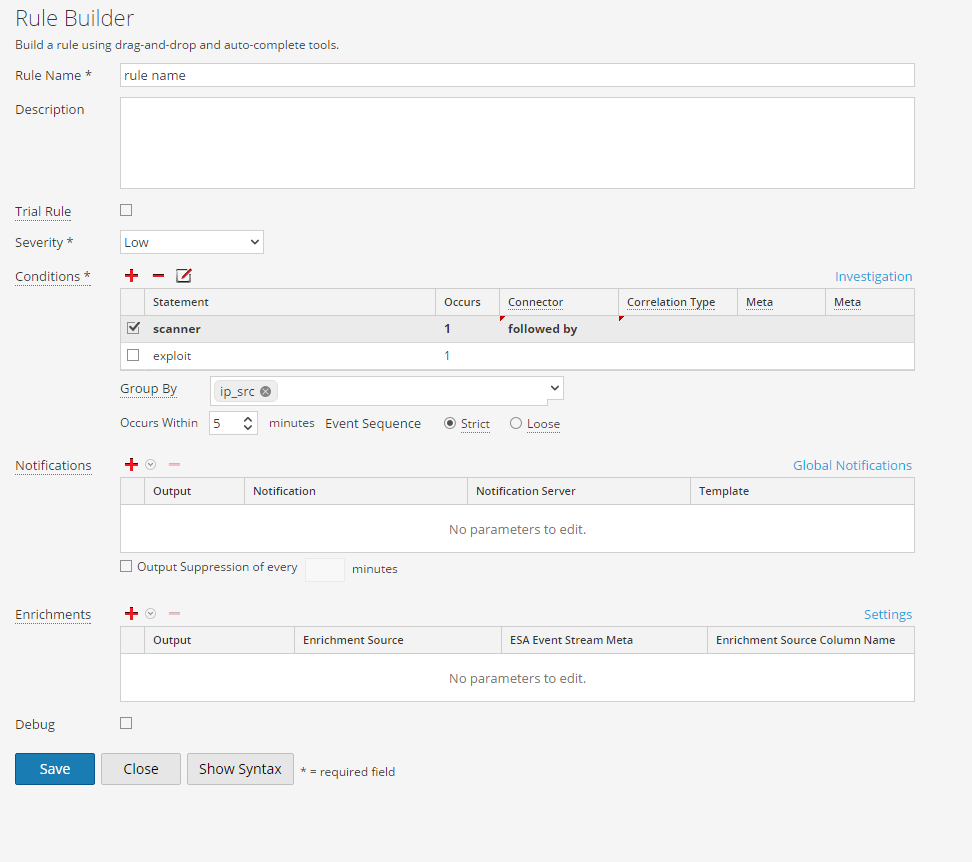
If you use ESA you will create a rules like:
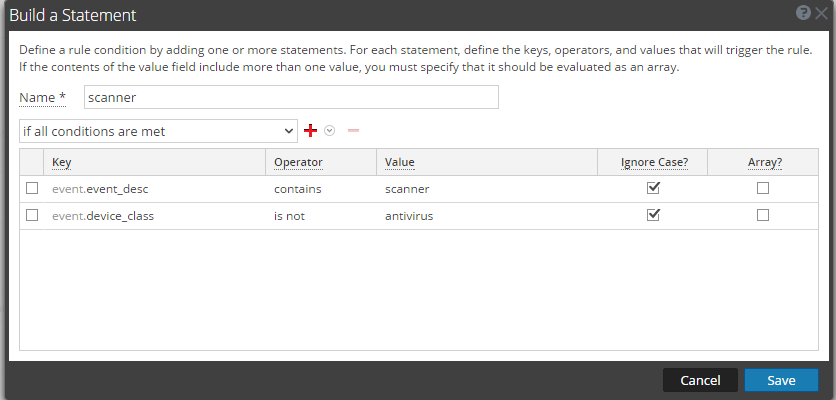
Where scanner is:
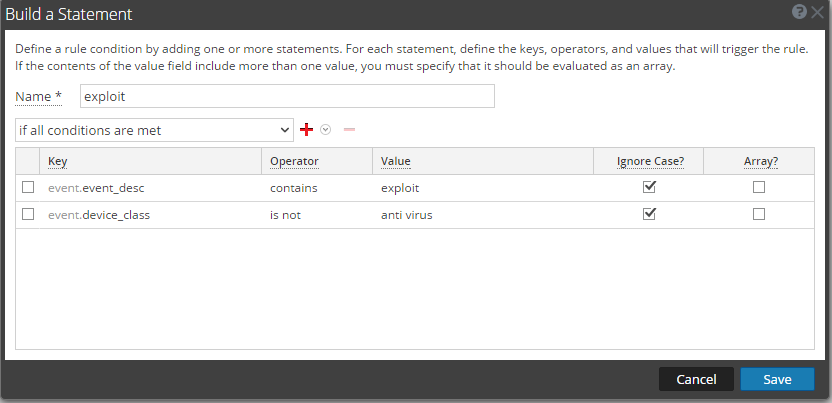
and exploit is:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-01-10 09:10 AM
The other option you have is to use a data window. Windows are used to store values for a predetermined time.
For example in your sample rule, you could take the output from rule 1 and store the result for say 30 minutes. Then run rule 2 and see if there is a match from the past 30 minutes.
Think of a data window as a decaying list based on a time value you define.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-01-10 10:14 AM
As you can already see, there are a few different ways to achieve this goal. The above comments seem to rely on the use of ESA, which is certainly up to the task. I want to show a different approach using the decoder and reporting engine.
The rules you have created for yourself are fine, however may not achieve the goal in the reporting engine. However, if we modify rule 1 to just pull back ip.src, we can then take those results and populate a dynamic list in the reporting engine. Then, in rule 2, we can take the results that are in that newly populated dynamic list and feed ip.src.
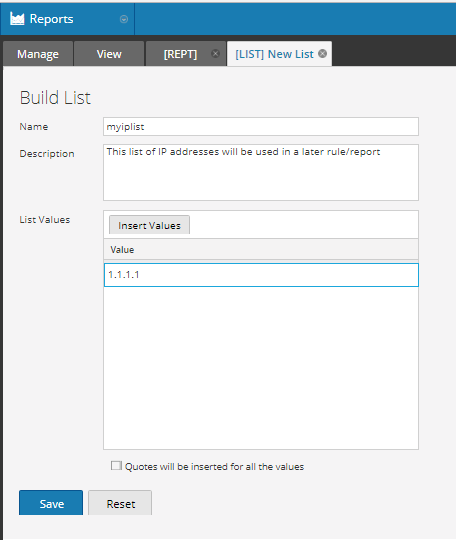
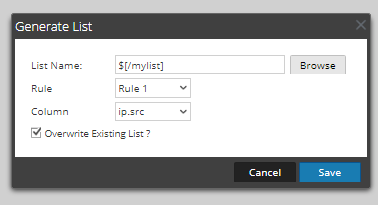
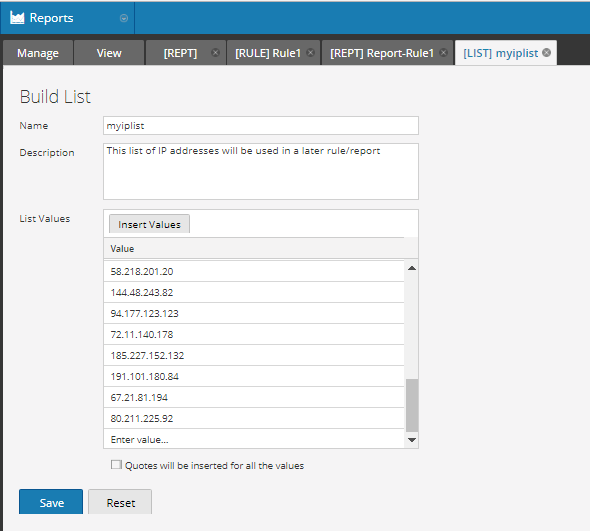
First, we create the dynamic list. We will just populate it with a dummy value so that it will save.
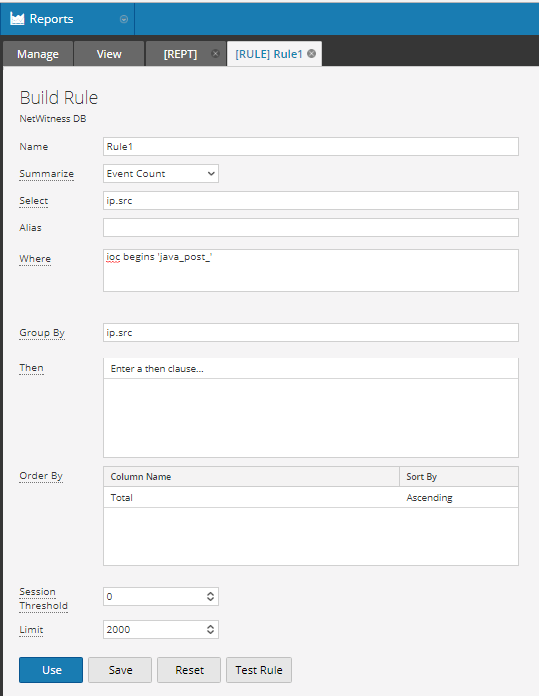
Once our list is created, we create our modified Rule 1.
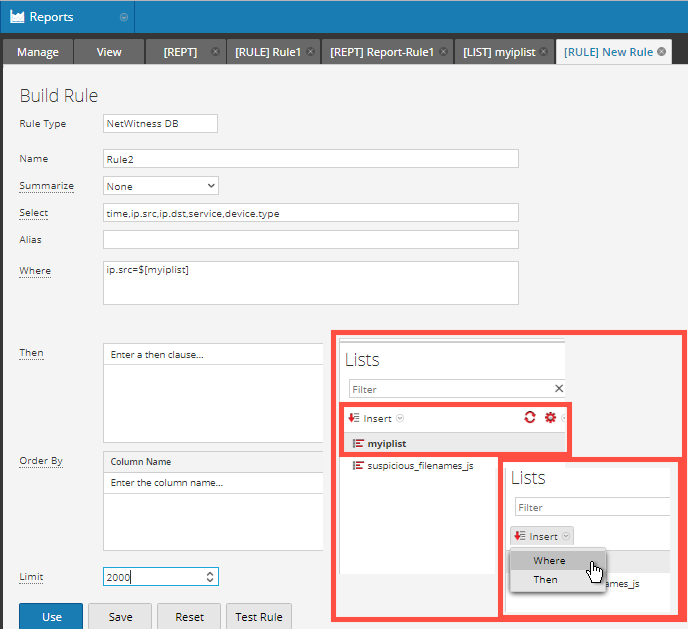
Here, I am only selecting ip.src meta which will then be used to populate the follow up rule for my report. Again, the where clause does not matter...it can be any legitimate query. In this case, it is finding some custom meta I have in my environment.
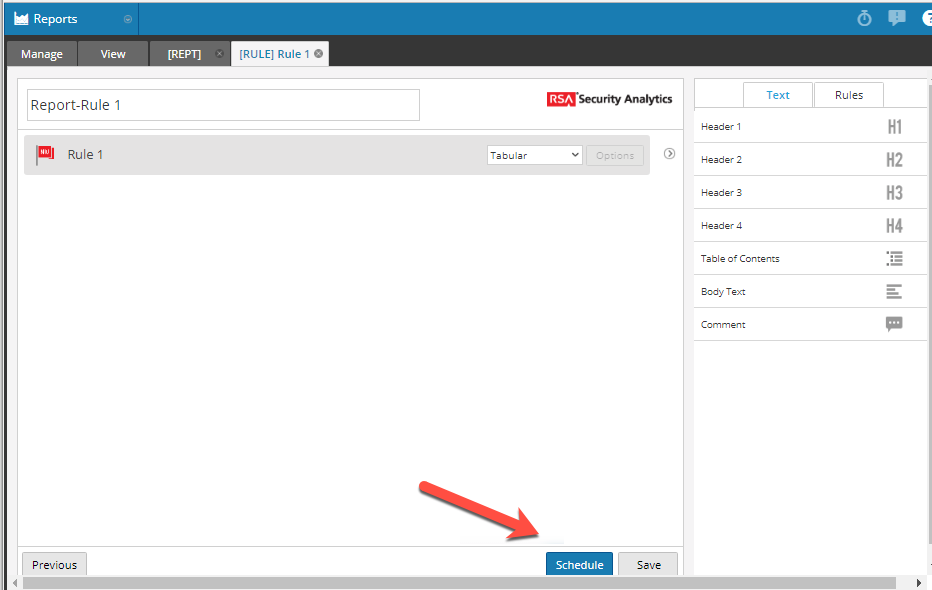
Once saved, I USE that rule in a new report and click SCHEDULE.
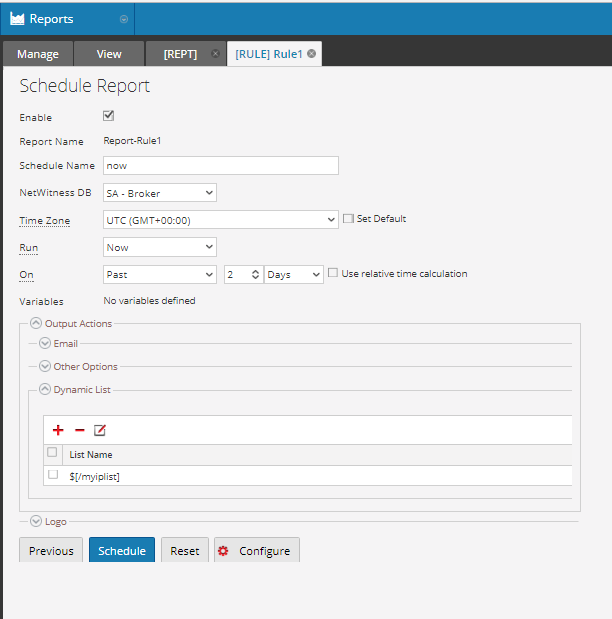
In the schedule options, I specifically pick the Dynamic List in the Output Actions.
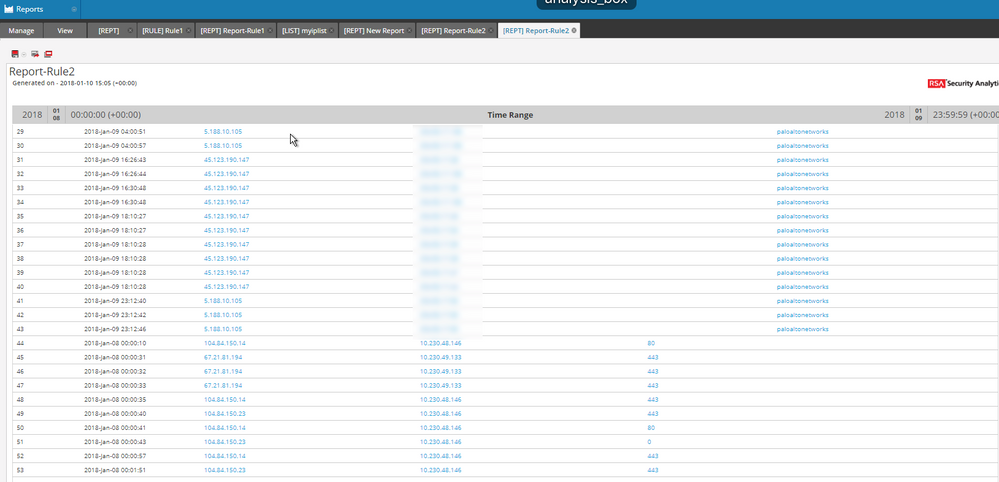
If we look back into the dynamic list we created, we now see it populated with results.
Now that our list has data, we can use it in our second report rule. You can type out the list name manually, or you can use the LIST option in the lower right column and add it to your where clause.
We would do the same thing as we did for the first rule. We save the rule, then USE it in a new report. We can create a schedule and then run the report.
One important note about dynamic lists, however. Dynamic lists operate like a giant OR statement against a meta key. OR statements can take a lot longer to process through. One way around all of this is to go back and revisit what my use-case really is.
In rule 1, you have a where clause "event.desc contains "scanner" && device.class != 'Anti Virus' ". What I might do, is create a simple application rule and push it out to all my log decoders. That way, meta would be created at the point of capture. Now, rather than having to find all the source IP's in one query to be used in another, I could complete the task with one query "metakey = 'meta_value'" and return the values I am interest in (event.time, ip.src, country.src, ip.dst, ip.dstport, action, event.desc).
Again...a few different approaches to this. Hope this helps.
Chris
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-01-10 10:31 AM
I like your approach. It will be useful for further use cases. I will keep it in mind.
Thanks Chris, very useful!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-01-11 12:14 AM
Hey Chris. That was helpful. Thank you very much. Can you please help me to understand how can i achieve this
" What I might do, is create a simple application rule and push it out to all my log decoders. That way, meta would be created at the point of capture. Now, rather than having to find all the source IP's in one query to be used in another, I could complete the task with one query "metakey = 'meta_value'" and return the values I am interest in (event.time, ip.src, country.src, ip.dst, ip.dstport, action, event.desc). "
with the help of screenshots.
Thanks Again
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-01-11 07:48 AM
Abdoot,
The more I am thinking about this, the more I think the app rule approach might not be best. The first rule is basically looking for scanner systems and to collect the IP addresses from those. This would really just be around scanner log activities from just those event sources. However the second rule takes the IP addresses and looks for ANY traffic or logs from those IP addresses.
Therefore, I think if that is what you are trying to find...any traffic or logs from those source IP addresses...then the report engine approach with dynamic list would be the way to go.
Chris