- NetWitness Community
- Discussions
- Detecting PlugX using Security Analytics
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Detecting PlugX using Security Analytics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2016-01-22 12:50 PM
PlugX is a RAT (Remote Access Trojan) malware family that is around since 2008 and is used as a backdoor to fully control the victim's machine. Once the machine is infected, a cybercriminal can remotely execute several kinds of commands on the affected system.
Notable features of this malware family is the ability to execute commands on the affected machine in order to retrieve machine information, capture the screen, send keyboard and mouse events, key logger, reboot the system, manage processes (create, kill and enumerate), manage services (create, start, stop, etc.), manage Windows registry entries, open a shell, etc. More details can be found here.
In this blog post, we will discuss how to detect its C2 beaconing activity.
The malware can communicate with the C2 server by using several protocols, like TCP, UDP and HTTP. All transmitted data is encrypted and compressed with customized algorithms.
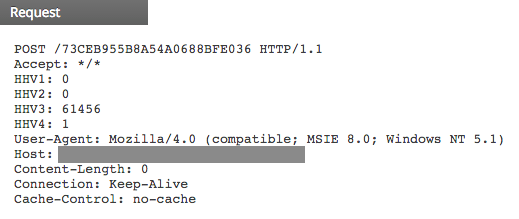
Following is an example of a POST request used by the malware to communicate with the C2 server:
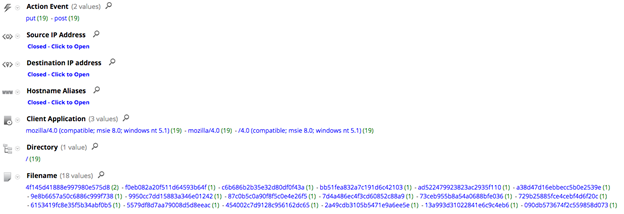
The screenshot below shows the network activity in RSA Security Analytics investigator:
Assuming the appropriate meta keys are enabled, the following query can be used:
action = 'put' && directory ='/' && filename length 24 && extension = '<none>' && query !exists
Scan results for a PlugX variant can be viewed here.
All of the IOCs from those HTTP sessions were added to the following RSA FirstWatch Live feeds:
- RSA FirstWatch APT Threat Domains
- RSA FirstWatch APT Threat IPs
If threat.desc meta key is enabled then you can use the following app rule: threat.desc = 'apt-plugx-c2'.