- NetWitness Community
- Discussions
- Detecting Ransom32 using Security Analytics
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Detecting Ransom32 using Security Analytics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2016-01-13 05:47 PM
Ransom32 is a new ransomware malware family that comes packaged as an NW.js application. NW.js is a framework that lets developers use javascript to create desktop applications that can run on Windows, Mac OS X and Linux. Having an OS independent ransomware, or any malware for that matter, is quite interesting. However, its host and network behavior is still similar to other ransomware families. In this blog post, we will discuss how to detect its network traffic using RSA Security Analytics.
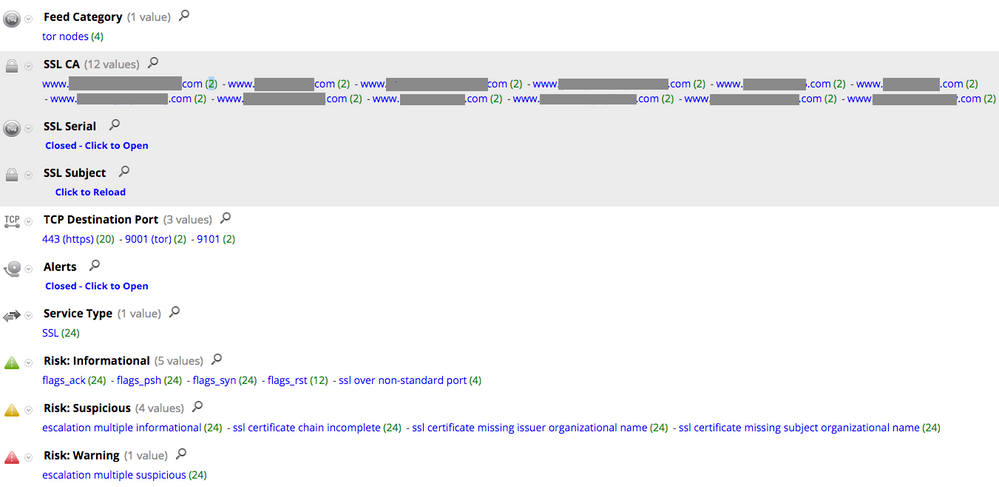
Among the different components that get installed on a system infected with Ransom32, there is a Tor client responsible for the communication with the command and control server hidden in the Tor network. This is how the traffic looks in Security Analytics:
The SSL handshake between the client and the server is using a certificate with an anomalous certificate authority field. The value of the SSL CA key is a URL that starts with ‘www.’. Please note that this network behavior is not exclusive to Ransom32.
The following query can be used to detect Ransom32 network activity:
ssl.ca begins ‘www.’ && tcp.dstport = 9001
Scan results for a Ransom32 can be found here. You can read more about Ransom32 here.