- NetWitness Community
- Discussions
- Detecting Taidoor variants using Security Analytics
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Detecting Taidoor variants using Security Analytics
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2016-02-01 03:34 PM
Taidoor is a malware family that has been used in cyber espionage campaigns since 2008. In this blog post, we will discuss how to detect its beaconing activity using RSA Security Analytics.
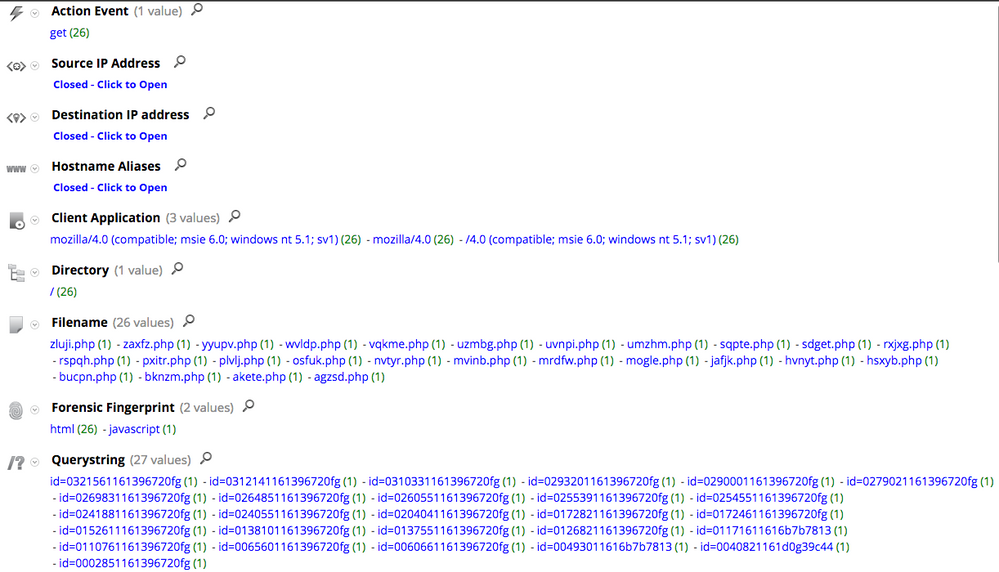
Taidoor binaries use a certain URL pattern in their communication with the C2 server. This is how the traffic looks in Security Analytics Investigator:
The value of the id parameter in the querystring is always 18 characters long where the last 12 characters represent an encoded value of the victim machine MAC address. The filename; without the extension; is always 5 characters long.
Given the artifacts above and assuming that the appropriate meta keys are enabled, the following query can be used to detect Taidoor network activity:
action = 'get' && extension = 'php' && query begins 'id=' && filename length 9 && query length 21
Scan results for a Taidoor variant can be found here.
All of the IOCs from those HTTP sessions were added to the following RSA FirstWatch Live feeds:
- RSA FirstWatch APT Threat Domains
- RSA FirstWatch APT Threat IPs
If threat.desc meta key is enabled then you can use the following app rule:
threat.desc = 'apt-taidoor-c2'
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2017-05-11 04:51 PM
Can we get this content updated to account for the FireEye blog here: Evasive Tactics: Taidoor « Threat Research Blog | FireEye Inc? It now can have a filename from between 8 and 12 characters in length and could be a .jsp. Maybe something like:
action = 'get' && extension = 'php','jsp' && query begins 'id=' && filename length 8-12 && query length 21
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2017-05-17 02:11 PM
Matthew,
FireEye blog post is from 2013. The app rule in this post is based on the samples we analyzed in early 2016.
-Ahmed