- NetWitness Community
- Discussions
- How to get information on redirection domains?
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-04-29 02:23 AM
Hi,
I need a real quick help.
Long time I observed one domain “Ib.adnxs(.)com”, this seems it does redirection to multiple malicious malware related domains. I wanted to get information on all redirection domain happened through it.
Drilled with host alias there were lot many hits found. Can anyone please help me, what kind of informer report or custom drill will give me redirection domain information?
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-04-29 09:55 AM
Couple of ideas:
- write a parser for the redirection method (easy for 301/302 and metarefresh, hard for iframes with potential obfuscation). This allows you to write URLs into a separate report.
- search for "referer contains lb.adnxs(.).com". Then look at "alias.host", i.e., "select alias.host where referer contains lb.adnxs(.)com"
- search for "alias.host = lb.adnxs(.)com". Export all sessions to a PCAP. Then use tshark to extract the redirections.
I tend to apply the last method. tshark + regular expressions can be very powerful and with the REST-API you can very easily automate the process.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-04-29 09:55 AM
Couple of ideas:
- write a parser for the redirection method (easy for 301/302 and metarefresh, hard for iframes with potential obfuscation). This allows you to write URLs into a separate report.
- search for "referer contains lb.adnxs(.).com". Then look at "alias.host", i.e., "select alias.host where referer contains lb.adnxs(.)com"
- search for "alias.host = lb.adnxs(.)com". Export all sessions to a PCAP. Then use tshark to extract the redirections.
I tend to apply the last method. tshark + regular expressions can be very powerful and with the REST-API you can very easily automate the process.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-04-29 10:53 AM
Thanks for the information.
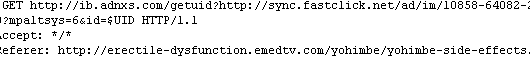
This site is not referring any domains while accessing it is redirecting to other malicious sites. Below is the screenshot
There were 40K hits for last 24 hr, It is not practically possible to get it from tshark.
Could please share the parser what you have mentioned on the redirection. That would help me a lot. Thanks again for your time.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-04-30 04:01 AM
In your example, the "erectile-dysfunction"-site seems to embed ads from ib.adnxs.com (potentially malicious). So you are looking for sites that lead to ib.adnxs(.)com, not the other way round?
The informer query:
referer where alias.host = ib.adnxs.com
should give you a list of domains like "erectile-dysfunction".
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-04-30 08:07 AM
Thanks a lot for the information.
There were lot many source hosts not able to get the infected file ![]() which is trying to reach all these domains.
which is trying to reach all these domains.
I got above 800 referer domains. Wanna try more to find the infection. Thank you
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-04-30 09:02 AM
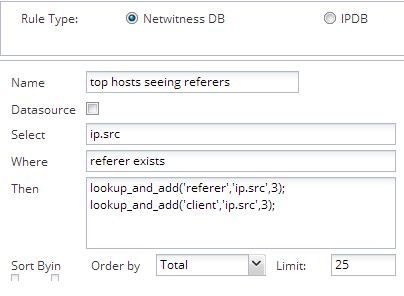
Yeah, you definitely have an adware infection. If your ultimate goal is to find out who likely has popup infections like this, one idea is to make an informer report to look for the top 25 source ips where referrer exists. That will give you a listing of the internal hosts that are being redirected the most. This will catch hosts that aren't going to ib.addnx.com.
And if the files aren't being found, make an informer report looking for the top 25 internal hosts that receive a 40x error. That rule is ip.src where org.dst exists && error begins '40'
Also take a look at user-agent strings with each of these. That would be as simple as putting in the then statement:
lookup_and_add('client','ip.src',3);
If you need any other ideas, let us know.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-04-30 09:17 AM
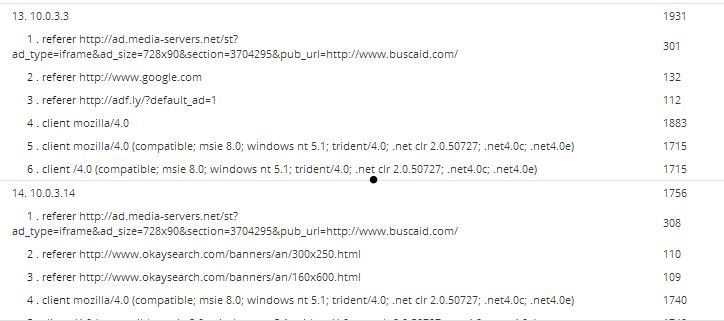
I have a sandbox running all kinds of malware and adware infected hosts. Here is an example of the output from one of my reports.
Note how one of the top referers are google.com? That's a sure sign that the referer is faked. A true referer would include the search string in the referer field. Note that my top 25 are ALL Malware driven. My rule for this is:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-05-01 02:56 AM
Thank you Fielder for your support.
I ran the reprot ip.src where org.dst exists && error begins '40' with then statement. I got the result but I did not see anything malicious on the result. I am not sure about error 40x. Could you please help me to understand on what parameter I have to look into it to confirm infection.
On your second post, I too created the same report and got results. How can be all 25 are Malware driven. What next I have investigate, on this kind of case does Antivirus scan will help? It is something I saw new like on the report output I can make sure the machine is 100% infected. Please explain so that I can put these as e-mail alert.
Thanks a again for you knowledge sharing. ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-05-01 03:53 AM
Why do you think you have an infection in the first place? I get even more than 40k hits per day. Adnxs is a very common tracking/advertisement site.
Also, "referer = http://www.google.com" is very common and not a sign for malware. If I do a google search for Netwitness and click on a link, the header looks like this
GET /the-new-netwitness-community-is-live/ HTTP/1.1
Host: blogs.rsa.com
(...)
Referer: https://www.google.com/
or like this
GET /url?sa=t&rct=j&q=netwitness&source=web&cd=1&sqi=2&ved=0CC0QFjAA&url=http%3A%2F%2Fwww.emc.com%2Fsecurity%2Frsa-netwitness.htm&ei=ZsmAUYPEOMaVtQaD94CYAw&usg=AFQjCNGrZH7fRfQYlFAZrQ52fwyq_h8rFQ&bvm=bv.45921128,d.ZWU HTTP/1.1
Referer: http://www.google.com/
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-05-01 08:54 AM
Anil, what were the file names being requested with the 40x error? If they are requests for exes, those might be attempts to download secondary packages to machines that are already infected.
I am not saying that the top referring hosts are all malware driven. But if you are looking for adware infected hosts, these are the first ones to examine. It takes time to figure out what is going on. One way to check is to see if those urls in the get requests are present in urlquery.net