- NetWitness Community
- Discussions
- Huffington Post False Positive?
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-03-26 04:51 PM
Has anyone seen any unusual activity with huffington post recently?
We have a nightly report set up for botnets and have seen daily activity on it for about a week or so.
I know the site is legit so I am curious if anyone else is seeing anything weird.
Maybe its a false positive? The weird thing about it is that each IP that went to the site only had 1-2 sessions.
I'm thinking anyone going to that site will be clicking on more than 1-2 links.
Any thoughts on this?
Thanks
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2014-01-03 11:24 AM
To get rid of these false positives disable nw45030.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-03-27 08:41 AM
Are the queries out of business hours? Are they happening only when users turn their computers on in the morning? Is there other user initiated behavior going on during the times when the "beacons" appear? Pivot on a source IP and step through a timeline to see if it looks like pattern-of-life behavior or pattern-of-malware. 😉
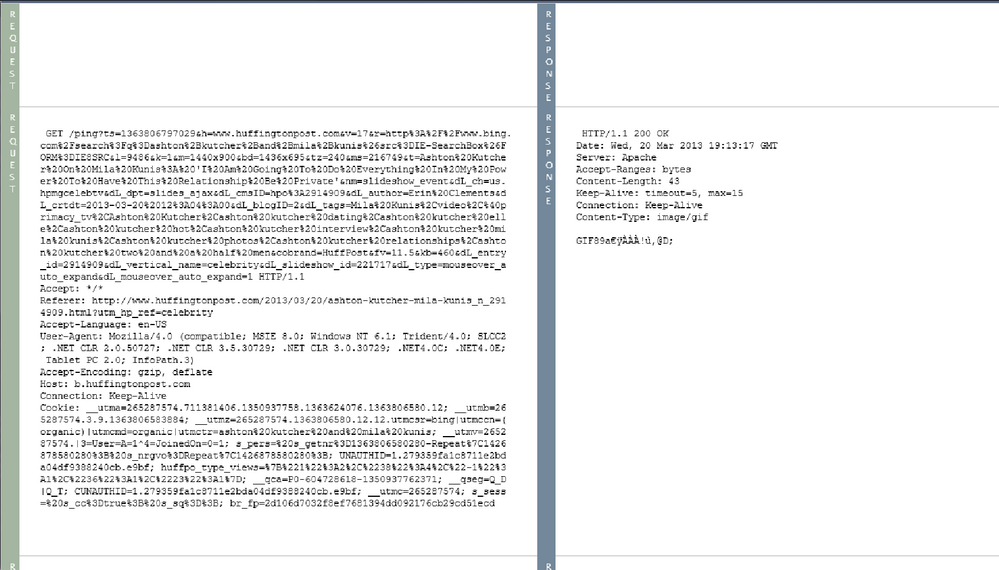
Also, what are the queries? Do they look like standard GET requests or are they POST methods with unusual base64 encoded strings? Are your internal systems calling out to Huffington Post doing anything else unusual like trying to call out on unusual ports or protocols?
These are the things that would be going through my mind if I was looking at your data.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-03-27 12:11 PM
Please bare with me as I am a little new with NetWitness and these investigations. ![]()
If I do a alias.host drill for huffingtonpost.com for the last 7 days, I see thousands of hits on that site but I only see this botnet alert for 1-3 users per day and their traffic is only 1-3 hits per user.
I am thinking with the type of site this is, that the users would be clicking on more than 1-3 links.
I did approach one of the users about this and apparently he did not know he was even going to this site. He showed me how he goes to aol.com for news but did not know that most of their news feed comes from huffington which you can clearly see once you click on the link and are routed to huffingtonpost.com.
In regards to your questions:
Are the queries out of business hours? no
Are they happening only when users turn their computers on in the morning? various times during the day
Is there other user initiated behavior going on during the times when the "beacons" appear? doesnt seem to be
Pivot on a source IP and step through a timeline to see if it looks like pattern-of-life behavior or pattern-of-malware. i notice 1-3 hits to the site and thats it but theres no apparent pattern for these alerts
Also, what are the queries? random things on huffington
Do they look like standard GET requests or are they POST methods with unusual base64 encoded strings? not sure. i am still a bit of a noob with this
Are your internal systems calling out to Huffington Post doing anything else unusual like trying to call out on unusual ports or protocols? doesnt look it
Thanks so much for your time.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-03-27 04:10 PM
Joe,
Looks like HuffPo is using a sketchy advertiser. The bot traffic that is triggering has a query that begins 'ts=' and that query is known for some beaconing. This may be a false positive, but if its the same source IP's doing it every time, I'd take a look at the sources to see if they have any browser helpers or toolbars installed.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-03-27 04:36 PM
Fielder,
I can definitely poke around but this is not contained to 1 or 2 users.
We are seeing this on 1-3 users daily at this point.
Thanks so much for the advice.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-03-28 01:09 AM
I have seen quite a few huffington post hits (about 4 per day over the last week). They came up at normal times and triggered on/as botnet and botnet_bredolab threats. After some simple Google foo the conclusion that I drew was that it triggered on action=bot and was a false positive.
The reason I thought this is that I found articles like this
- http://www.securelist.com/en/analysis/204792152/End_of_the_Line_for_the_Bredolab_Botnet
that showed what the C&C traffic might look like. And the action=bot was present in that also also as "event_action=bottom_thumbnail_nav" in ONE of the GET requests in the session ![]() . Unfortunately it looks like the detection rule is not "anchored" on the ends (ie: it doesnt need to match 1 parameter).
. Unfortunately it looks like the detection rule is not "anchored" on the ends (ie: it doesnt need to match 1 parameter).
On a related side question - is there any way in NW to go BACKWARDS to find what caused a rule to be triggered? EG: which domain/part of a request has resulted in NW thinking that it is an Advanced Persistent Threat would be great!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-03-28 08:32 AM
im starting to think its a false positive as well. im still kinda new to all this so its a learning process along the way to discovering things.
i think i am going to open a ticket and post this link to it and see what they have to say.
thanks
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-03-28 11:18 AM
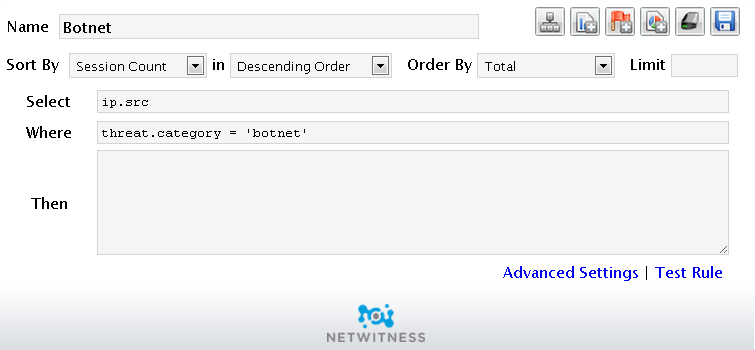
We don't have any rules that look for "action=bot." What is the exact name of the indicator meta that says this is bot traffic?
Also, I'd love to know what the user-agent strings of the requesting hosts are.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-03-28 11:48 AM
Fielder,
This is what we have. I did not set this up personally. This was set up when our PS rep came in a month ago.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2013-04-01 02:51 PM
Hi Joe. That's a mighty thin report. See my post here on detecting botnet traffic, how to setup your live charts, and implement zero-payload tracking to threat sources. Also make sure you have the latest rules I've been posting that detect the most modern botnets in my blog post here.
Don't let Informer intimidate you. It is the most powerful tool we have to find the bad stuff. If you get lost or need examples, check out the excellent help file- it will even show you how to filter out false positives from your result sets.