- NetWitness Community
- Discussions
- Re: Lost Logs or Events
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Lost Logs or Events
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2019-02-06 12:56 PM
I need a rule ( ESA rule ) or anything that can do the trick to monitor if an event stopped sending logs.
Yesterday Apache, and the Firewall stopped sending events and logs for 3 hours and we did not noticed, because no alert was triggered.
Is there a way to monitor that by an alert or something like it? I could create a dashboard ( which we already have ) or open the alarns in the Event Source but if we are occupied analysing an incident or doing something else we cannot tell whats going one, like yesterday...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2019-02-07 09:23 AM
Then it should be disabled by default, unless RSA know for a fact that their majority of customers have less than 1000 event source entries (1 log hybrid basically). Hard to understand the logic.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2019-02-07 11:21 AM
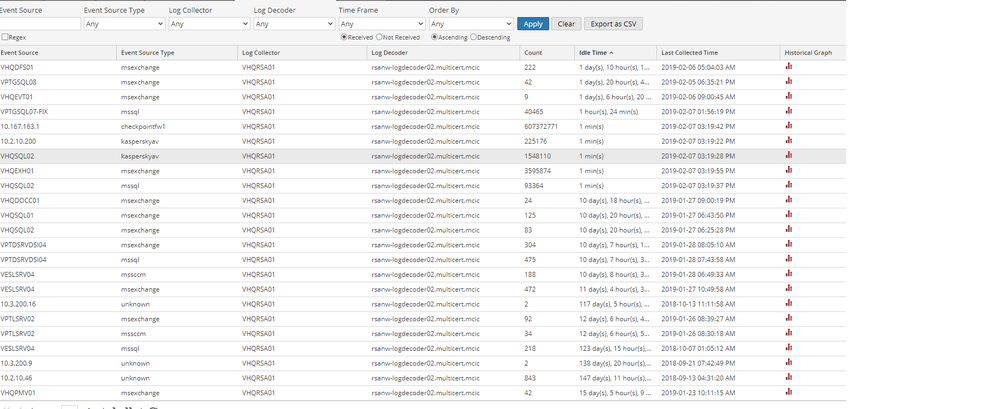
I event sources in idle:
I really need to get some king of alarm sent by email to be alerted. And never was i alerted of a failure in receiving the logs when they existed
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2019-02-08 06:54 AM
We are on 10.6.5 and had similar issues with ESM, where we didnt receive alerts when events sources stopped sending. We also had an issue that general alarms would not clear for health and wellness. we've been told that it is fixed in 10.6.6 but I wonder if anyone can confirm.
We've not upgraded as I implemented my own ESA Rules as a workaround. Here is an example for Windows Events not received within 2 hours.
========
CREATE CONTEXT ContextEveryMin_event_computer_mswindows INITIATED @now AND PATTERN [every timer:at(0, *, *, *, *)] TERMINATED AFTER 1 min;
@RSAPersist(serialization=Serialization.JSON)
@Hint("reclaim_group_aged=86400")
create window Window_mswindows_event_computer.std:unique(event_computer,device_type).win:time(5 days) (event_computer string,device_type string, last_timestamp long);
ON Event(
event_computer IS NOT NULL
and device_type is 'winevent_nic'
and parse_error IS NULL
AND isOneOfIgnoreCase(alert,{ 'critical event source group' })
and medium = 32
)
AS myevent
merge Window_mswindows_event_computer myWindow_mswindows_event_computer
where myWindow_mswindows_event_computer.event_computer.toLowerCase()=myevent.event_computer.toLowerCase()
AND myWindow_mswindows_event_computer.device_type.toLowerCase()=myevent.device_type.toLowerCase()
when matched
then update set last_timestamp = myevent.esa_time
when not matched
then insert
select event_computer.toLowerCase() AS event_computer,
device_type.toLowerCase() AS device_type,
myevent.esa_time AS last_timestamp;
@Name('event_computer Log Not Received within 2 hours')
@RSAAlert(oneInSeconds=0)
CONTEXT ContextEveryMin_event_computer_mswindows
SELECT
Window_mswindows_event_computer.event_computer AS event_computer,
Window_mswindows_event_computer.device_type AS device_type,
Window_mswindows_event_computer.last_timestamp AS last_timestamp
FROM Window_mswindows_event_computer
WHERE
(current_timestamp() - Window_mswindows_event_computer.last_timestamp) > 1000 * 3600 *2
AND (event_computer.toLowerCase() LIKE '%mycompany.co.uk')
GROUP BY event_computer,device_type
output snapshot WHEN TERMINATED;
========
You wont be able to use this out of the box, as it looks for Event Sources where we tag them with "Critical Event Source" using an app rule or feed. But the logic is sound. You will just need to modify for your environment.
It basically created a named window for each Windows event source and populates the value with when it was last seen. Then every minute it checks for those system where an event was not seen in over 1000*3600*2 milliseconds = 2 hours.
You then get an alert, that contains all windows devices that haven't generated an event in the last 2 hours.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2019-02-08 07:35 AM
I just cant understand how can RSA have a feature that does not work properly.
I stopped one event source to tested it and nothing ![]()
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2019-02-08 07:36 AM
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2019-02-08 11:24 AM
Yes, I agree Renato Goncalves. Its poor testing. I made the same comments when I worked at RSA and continue to make them now ive moved on.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2019-02-11 05:49 AM
Can this be good alert rule?
module Module_97f04f07_8a89_48af_bd55_3d0b16199f49;
@Name('Module_97f04f07_8a89_48af_bd55_3d0b16199f49_Alert')
@Description('')
@RSAAlert(oneInSeconds=0)
SELECT * FROM pattern
[every a = Event(
(device_ip in
(
'1.0.0.1',
'1.0.0.3',
'10.0.0.7'
)
or device_host in
(
'M.LOCAL','
M.OCAL',
'C.LOCAL',
'C.LOCAL'
))
and medium = 32
and customer_name = 'mc')
-> (timer:interval(12 hours) and not Event((device_ip = a.device_ip or device_host = a.device_host) and device_type = a.device_type and medium = 32))];
- « Previous
-
- 1
- 2
- Next »