- NetWitness Community
- Discussions
- Netwitness Spectrum Cloud Services
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Netwitness Spectrum Cloud Services
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2014-12-19 04:02 PM
I'm a bit confused about how Spectrum handles file analysis with regard to accessing services via the cloud. I know that when a file is analyzed, there is an option to send the md5 hash of that file to virustotal (for example) for searching their database. What I don't know is where that file gets hashed. Does spectrum first upload the file to the cloud, then hashing it there and sending that hash to virustotal? Or, does spectrum hash the file first and only send the hash to the cloud?
Asked in another way: when using a service like virustotal via the NW cloud, what exactly does our local spectrum appliance send to the cloud?
Thanks,
Josh
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2014-12-22 06:20 PM
I'm guessing nobody knows? This is a pretty important piece of information that I can't seem to find clarification for anywhere. Not in the docs, not in this community (yet) and thus far support has failed to grasp what I'm asking. I'm hoping they come back with some good information eventually, but it takes days just to find someone who understands what we need...
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2014-12-23 10:06 AM
Josh, sorry for the delay, I'm checking to see if I can get the right answer for you. Stay tuned.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2014-12-23 02:06 PM
here's a response I got from Support. Can we verify that this is a complete and correct list?
--snip--
Authenticode: Actual file is sent in order to validate its internal certificate
Bit9: MD5 Hash of file being analyzed
NSRL: MD5 Hash of file being analyzed
Robtex: Domain Name in network session (Server's Domain Name)
GFI Sandbox: Actual file is sent in order to execute it
ThreatGrid: Actual file is sent in order to execute it
URLVoid: URL targeted in network session (Server's URL)
URIBL: URL and Domain Name from network session
VirusTotal: MD5 Hash of file being analyzed
Google Malware: URL targeted in network session (Server's URL)
WhoisXML: Domain Name from network session
--snip--
Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2014-12-23 02:43 PM
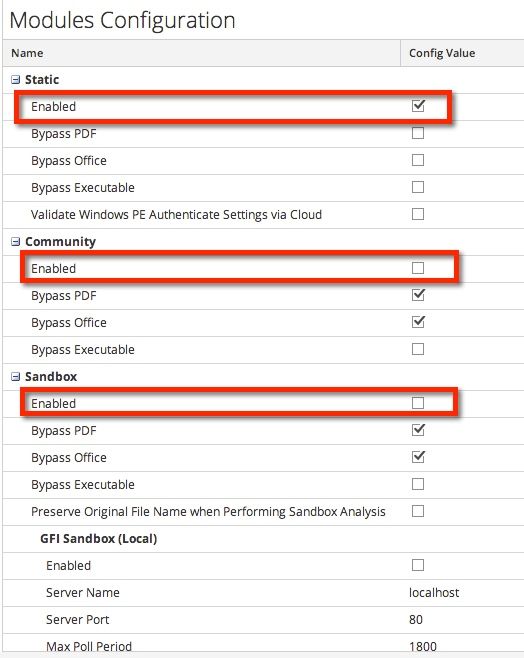
I loaded up an MA box and disabled any processing of files in the cloud or through the Sandbox.
Then, I manually submitted a file for scanning (yara.exe). The result was the md5 hash was created and displayed without the file being sent for analysis. The information was stored in the Static analysis area, which is processed on the Spectrum/MA appliance.
Log entries from /var/lib/netwitness/rsamalware/spectrum/logs/spectrum.log on the MA appliance:
2014-12-23 14:35:59,547 [fileUploadExecutor-1] INFO com.netwitness.malware.server.scheduler.jobs.AdHocJob - Uploading file: yara.exe.
2014-12-23 14:36:01,985 [fileUploadExecutor-1(#18 digest:b368a9581070c419788981cd3b081dde)] INFO com.netwitness.malware.server.scheduler.jobs.AdHocJob - Manual file upload: yara.exe completed in 2.41 seconds.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2014-12-23 02:57 PM
in that test, did you have services like VirusTotal enabled for access via the cloud? Did you get results from those services? Also, how did you verify that a file was never uploaded to the cloud?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2014-12-23 03:03 PM
I did not. Those services were not enabled in the MA configuration. Second, I never registered my test system for cloud services with Support. I also never configured DNS on this system.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2014-12-23 03:08 PM
I definitely appreciate the effort to assist, but my question is specifically about how cloud services behave. If you have a way to enable VirusTotal via the cloud and run tests with it enabled, I would be grateful.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2014-12-23 04:52 PM
It is just sending the hash. The hash is generated on the MA appliance first. Then, the hash is sent to the cloud community services to check whether it was observed by the community. The only time the actual file is sent anywhere is to a Sandbox, whether that is a cloud based sandbox or a local instance. In those cases, you would select whether you want PDF's and Office files submitted as those can contain sensitive material that organizations may not want submitted to a cloud provider.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2014-12-23 05:07 PM
That's what I was hoping for, except that I know of at least one instance (Authenticode) where the file is sent to a non-sandbox environment. Several others where additional meta is sent out, not just an md5 hash. It's the conflicting information from RSA that is giving us pause here.
FWIW, there are cases where we might not want any files of any type sent outside our own network. That's why we're trying to determine exactly when things are sent out and when they are not.