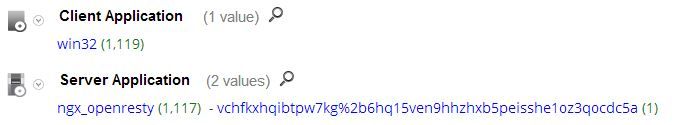- NetWitness Community
- Discussions
- Obvious Kazy Variant is Obvious
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Obvious Kazy Variant is Obvious
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2014-01-27 12:59 PM
A new variant of Kazy stands out via Packet Capture by breaking all the rules of malware being stealthy. It uses a unique user-agent string, beacons and downloads additional commands via the Gnutella Protocol, and uses a Web Server banner that belongs to a plug-in app for NGINX, the lightweight web server. I'm posting up this description of this Kazy Variant for instructive purposes. A PCAP is attached for demonstration purposes and to test rules.
The specific infector malware we are describing is detailed at VirusTotal here.
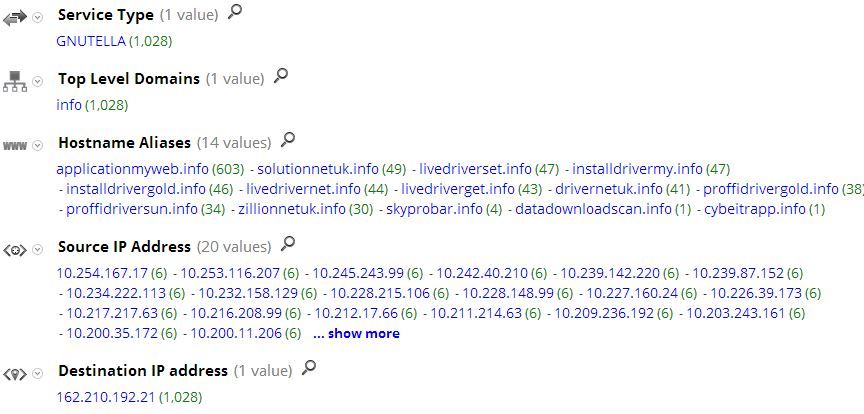
Below is how it appears in our Massive Malware Database:
Most organizations block the Gnutella Protocol, so risk of encountering this threat in most environments is pretty low. In this instance, there are a dozen .INFO domain names resolving to a single destination IP address. The Get request uses a falsified user-agent string of "win32" and the NGX_OpenResty server allows for LUA parsing from an NGINX server.
To detect this threat, you could add the win32 UA String to a feed of known malicious strings. The IP destination above has been added to the FirstWatch C2 Feeds.