- NetWitness Community
- Discussions
- Parsing a Firewall Log
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Parsing a Firewall Log
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2017-12-27 11:28 AM
Hello
I need to parse a firewall log but every time i parse it NW doesn't give me any useful results
This is the parser:
device="SFW" date=2017-01-01 time=13:36:34 timezone="WET" device_name="things" device_id=AA203100004445 log_id=010101600001 log_type="Firewall" l
og_component="Firewall Rule" log_subtype="Allowed" status="Allow" priority=Information duration=300 fw_rule_id=02 policy_type=1 user_name="anonimo@sapo.pt"
user_gp="utilizadores" iap=66 ips_policy_id=7 appfilter_policy_id=8 application="Secure Socket Layer Protocol"
application_risk=10 application_technology="Network Protocol" application_category="Infrastructure" in_interface="" out_interface="WAN" src_mac=00: 0:00: 0:00: 0
src_ip=10.000.000.00 src_country_code=A1 dst_ip=200.00.000.111 dst_country_code=USA protocol="TCP" src_port=12345 dst_port=123 sent_pkts=66 recv_pkts=66 sent_bytes=6666
recv_bytes=6666 tran_src_ip= tran_src_port=0 tran_dst_ip= tran_dst_port=0 srczonetype="LAN" srczone="LAN" dstzonetype="WAN" dstzone="WAN" dir_disp="" connevent="Stop" connid="2183694848" vconnid="" hb_health="No Heartbeat"
Im using NW LPT1.0
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2017-12-28 08:56 AM
I'm putting device="SFW" has messageID. Is that correct?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-01-02 01:59 PM
When you say "this is the parser," is what you have pasted below the actual content of the XML file? If yes, then it isn't structured correctly.
(it should look something like this:
"<event.cat.name>:<ec_activity>: in:<interface>out:(none), src-mac<smacaddr>, proto<protocol>(<tcpflags>,<tcpflags>),<stransaddr>:<sport>-><dtransaddr>:<dport>, len<bytes>"
)
Or is what you have pasted below that an example of the logs you are trying to parse?
Additionally, when you say it doesnt give you any useful information, can you be more specific? Is it not parsing anything at all? Is everything populating in the "word" meta key? Are certain fields that you want to see not showing up? Are meta values appearing in different meta keys than you want or expect?
Mr. Mongo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-01-03 12:12 PM
Hello Joshua,
First of all thanks for the reply
Sorry for not being specific. What i've pasted is the log of the firewall that i've downloaded from NW.
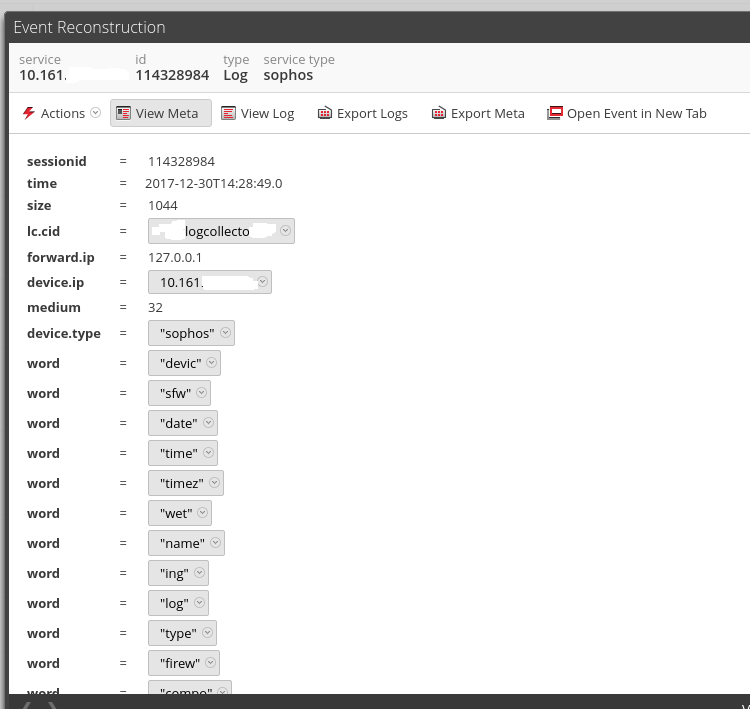
I'll attach the info that i'm getting in NW
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-01-03 08:31 PM
No apologies necessary ![]() . From that screenshot, we can tell a couple things about what's happening.
. From that screenshot, we can tell a couple things about what's happening.
First is that, because the device.type is identified as "sophos," NetWitness is using the sophos parser on the log.
Second is that, because everything is ending up in the "word" metakey, the sophos parser does not have a defined message ID that matches the payload of the log.
So then, a couple more questions - have you added any custom or non-standard headers or fields to your sophos logs? Or adjusted the default log format in any way?
If these are custom or non-default logs, then the Log Parser Tool will be the best tool for you to create a new message ID (RSA, a Dell Technologies business, announces the release of RSA® NetWitness Log Parser Tool v1.0 and the RSA® NetWitness Log Parser Community ). The User Guide and On-Demand eLearning Course at this link should help get you started with that.
If these are OOTB sophos logs with no customization and no changes to the format, then you could submit a completed parser for review and inclusion in the official parser to the community site on GitHub, or submit a request for official support of that event using the "Request an Event Source" link here: RSA Supported Event Sources .
Hope this helps.
Mr. Mongo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-01-04 10:42 AM
Hello Joshua,
We do not added any custom oior non standard headers to the sophos log and didn't made any adjustment in the log format.
I already used the Parser Tool but it gave me the same result. My difficulty is how to choose the header ID....I've also tried to parse has the learning course and the user guide suggests but it stays the same
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-01-04 11:21 AM
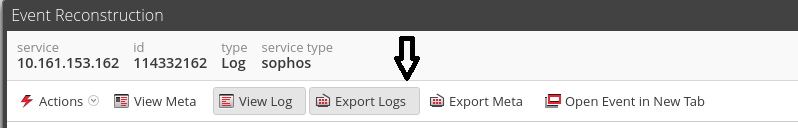
can you post the original raw log message for a few messages...change any IP to remove internal data bu keep the format intact so we can take a look at it.
you can get the raw from the same screen you showed the meta in, just export the raw log in .log format for us to take a look at.
this should be a sophos log correct?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-01-04 01:49 PM
The device is really Cyberoam CR200iNG which is a subcompany of Sophos
Heres some few messages. I've altered some data but this is the general picture.
device="SFW" date=2017-12-11 time=13:36:34 timezone="WET" device_name="CR200iNG" device_id=C2031434445 log_id=010101600001 log_type="Firewall" log_component="Firewall Rule" log_subtype="Allowed" status="Allow" priority=Information duration=259 fw_rule_id=13 policy_type=2 user_name="me@something.corp" user_gp="big group" iap=21 ips_policy_id=5 appfilter_policy_id=3 application="Secure Socket Layer Protocol" application_risk=1 application_technology="Network Protocol" application_category="Infrastructure" in_interface="" out_interface="WAN" src_mac=01:0:00: 0:00: 0 src_ip=10.000.000.00 src_country_code=R1 dst_ip=200.00.000.000 dst_country_code=USA protocol="TCP" src_port=5000 dst_port=200 sent_pkts=21 recv_pkts=26 sent_bytes=3370 recv_bytes=2342 tran_src_ip= tran_src_port=0 tran_dst_ip= tran_dst_port=0 srczonetype="LAN" srczone="LAN" dstzonetype="WAN" dstzone="WAN" dir_disp="" connevent="Stop" connid="1123356" vconnid="" hb_health="No Heartbeat"
device="SFW" date=2017-01-01 time=13:36:34 timezone="WET" device_name="things" device_id=AA203100 log_id=010101600001 log_type="Firewall" log_component="Firewall Rule" log_subtype="Allowed" status="Allow" priority=Information duration=300 fw_rule_id=02 policy_type=1 user_name="anonimous@something.corp" user_gp="big group" iap=66 ips_policy_id=7 appfilter_policy_id=8 application="Secure Socket Layer Protocol" application_risk=10 application_technology="Network Protocol" application_category="Infrastructure" in_interface="" out_interface="WAN" src_mac=00: 0:00: 0:00: 0 src_ip=10.000.000.00 src_country_code=A1 dst_ip=200.00.000.111 dst_country_code=USA protocol="TCP" src_port=12345 dst_port=123 sent_pkts=66 recv_pkts=66 sent_bytes=6666 recv_bytes=6666 tran_src_ip= tran_src_port=0 tran_dst_ip= tran_dst_port=0 srczonetype="LAN" srczone="LAN" dstzonetype="WAN" dstzone="WAN" dir_disp="" connevent="Stop" connid="218369" vconnid="" hb_health="No Heartbeat"
device="SFW" date=2017-12-11 time=13:40:53 timezone="WET" device_name="CR200iNG" device_id=C2031434 log_id=050901616001 log_type="Content Filtering" log_component="HTTP" log_subtype="Allowed" status="" priority=Information fw_rule_id=13 user_name="johndoe@something.corp" user_gp="big group" iap=21 category="Whitelist" category_type="Productive" url="https://www.google.com/" contenttype="" override_token="" httpresponsecode="" src_ip=199.000.000.00 dst_ip=200.00.000.000 protocol="TCP" src_port=50000 dst_port=100 sent_bytes=0 recv_bytes=1394 domain=www.google.com exceptions=https activityname="" reason=""
device="SFW" date=2017-12-11 time=13:40:44 timezone="WET" device_name="CR200iNG" device_id=C203143 log_id=010101600001 log_type="Firewall" log_component="Firewall Rule" log_subtype="Allowed" status="Allow" priority=Information duration=10 fw_rule_id=13 policy_type=2 user_name="women@something.corp" user_gp="big group" iap=21 ips_policy_id=5 appfilter_policy_id=3 application="" application_risk=0 application_technology="" application_category="" in_interface="LAN" out_interface="" src_mac=00: 0:00: 0:00: 0 src_ip=100.000.000.000 src_country_code=R1 dst_ip=10.000.000.000 dst_country_code=R1 protocol="TCP" src_port=5000 dst_port=1000 sent_pkts=5 recv_pkts=5 sent_bytes=486 recv_bytes=409 tran_src_ip= tran_src_port=0 tran_dst_ip= tran_dst_port=0 srczonetype="LAN" srczone="LAN" dstzonetype="WAN" dstzone="WAN" dir_disp="" connevent="Stop" connid="295600" vconnid="" hb_health="No Heartbeat"
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-01-04 02:15 PM
is that the meta export or raw log export? the format doesn't look like what i would expect ..
headers like this:
%sophoses:
%SOPHOS
please confirm
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-01-04 02:52 PM
I went with Export Logs