- NetWitness Community
- Discussions
- Re: Web URL Request Alerting
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Web URL Request Alerting
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2017-01-17 01:38 AM
Hi, I have the squid logs being indexed by the log concentrator, and assigned to the 'url' meta correctly, via a custom parser. I now need to create an alert based on threat feed and notify on the event of a detection of a url requested, which is present in the threat list/feed. Can someone please guide me how to enable this?
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2017-01-17 06:35 PM
As is usual for all things, it depends. Having more information will be helpful.
- Do you have an ESA system?
- How frequently are these threat feeds going to be updated?
- Is the threat feed available in .csv format for inclusion in a NetWitness feed?
At first glance I'd setup a feed with my blacklist/threat feed against the url metakey and then have it alert to a custom metakey you use (i.e. squid.alert) and then have your reporting engine or ESA system just look at any events where squid.alert exists.
Obviously this could be much more complicated, you could add more comparisons at the log decoder level, at the ESA level, etc.
Please provide more context, as much as possible would be great.
Thanks,
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2017-01-18 12:56 AM
Hi Kevin, thanks for the details. I do have an ESA setup in the environment. I have the feed planned to be updated automatically (if feasible) or manually (once a week). I have the threat feed available in a .csv format. I have never setup use cases that utilize threat feeds, so this one is fairly new. Any further steps or docs would help me immensely, and I appreciate your help. Thanks!
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2017-01-18 03:39 PM
I'd take a look at the feed documentation first.
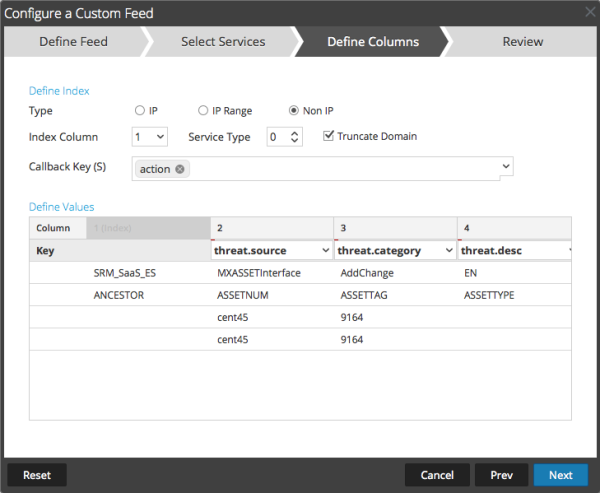
In this screenshot example you're CSV will populate data into column 2 threat.source based of the index in column 1. In the callback metakey it is "action".
So whenever an action is found matching column 1 in the .csv feed, it'll populate those additional columns as threat.source, threat.category, etc.
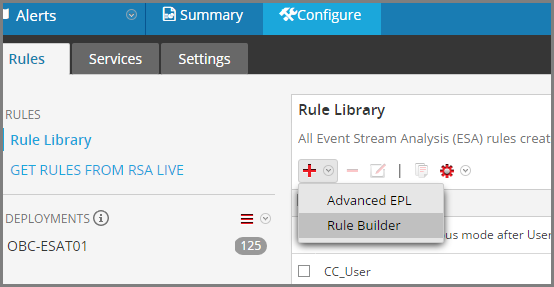
Once you've deployed that feed to your decoders, then I'd suggest attempting to define an ESA rule based off it.
Add a Rule Builder Rule - RSA Security Analytics Documentation
The parent document has a ton of info on ESA.
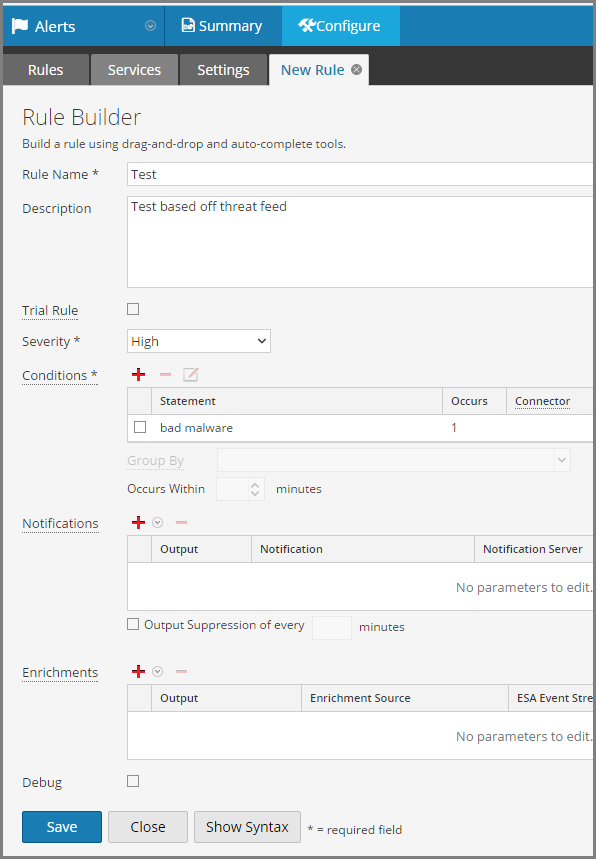
Example screenshot below.
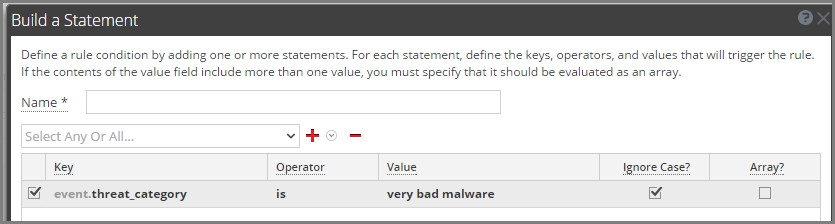
In the screenshot above I set the value of the meta in threat_category to "very bad malware". Something I'd expect in the feed in column 2 we setup earlier.
Then whenever the data is processed from the decoder, the feed will add the metakey, then when ESA processes it, it'll alert.
This method is useful for using the threat feed data in the platform for other use cases (investigations, reporting, etc) and reduces the load on ESA by pushing the logic down to the decoders.