This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
NetWitness Knowledge Base Archive
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- NetWitness Community
- NetWitness Knowledge Base Archive
- Custom SSL certificate on web interface is removed after upgrading to RSA Security Analytics 10.4.0....
-
Options
- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Custom SSL certificate on web interface is removed after upgrading to RSA Security Analytics 10.4.0.2 or above
Article Number
000029187
Applies To
RSA Product Set: Security Analytics
RSA Product/Service Type: Security Analytics Server, Security Analytics UI
RSA Version/Condition: 10.4.0.2, 10.4.1.x, 10.5.x
Platform: CentOS
O/S Version: EL6
RSA Product/Service Type: Security Analytics Server, Security Analytics UI
RSA Version/Condition: 10.4.0.2, 10.4.1.x, 10.5.x
Platform: CentOS
O/S Version: EL6
Issue
After upgrading to RSA Security Analytics 10.4.0.2, the public CA certificate that was installed at a previous version following the instructions in the knowledgebase article 26817 no longer appears to be present.
When navigating to the Security Analytics user interface, it once again shows invalid HTTPS connection with the message: "The identity of this website has not been verified."
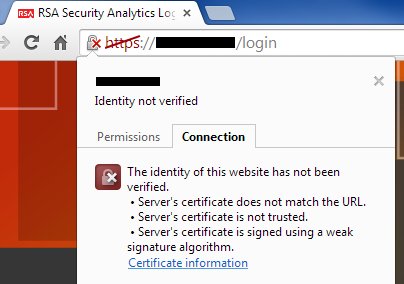 Image description
Image description
When navigating to the Security Analytics user interface, it once again shows invalid HTTPS connection with the message: "The identity of this website has not been verified."
 Image description
Image descriptionCause
In order to resolve some FIPS-related issues within Security Analytics, version 10.4.0.2 includes a Puppet module that changes the Jetty 9 web server keystore path from /opt/rsa/jetty9/etc/keystore to /opt/rsa/carlos/keystore, which is the default puppet keystore.
This forces the Puppet CA certificate to be used for the user interface.
This can be verified by looking at the Certificate Information from the web browser, which will display information similar to the example below.
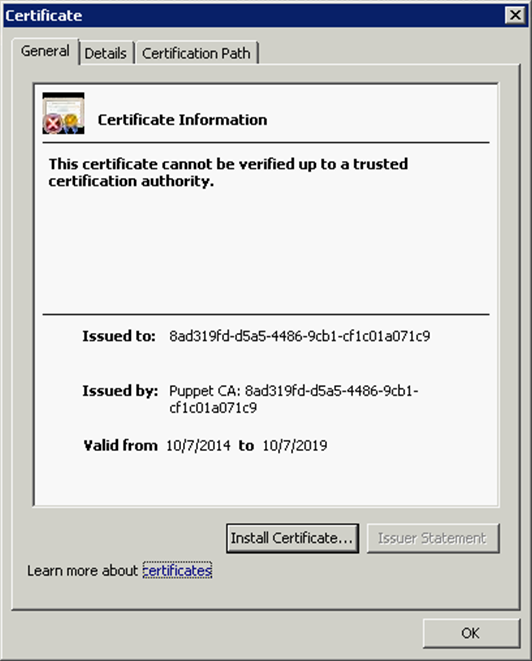 Image description
Image description
This forces the Puppet CA certificate to be used for the user interface.
This can be verified by looking at the Certificate Information from the web browser, which will display information similar to the example below.
 Image description
Image descriptionResolution
This issue will be addressed in Security Analytics 10.5, at which point it will be possible to import a custom CA certificate chain into the Puppet keystore.
However, if a backup was made to the /opt/rsa/jetty9/etc/jetty-ssl.xml file as instructed in the installation guide and in the knowledgebase articles entitled How to back up a public CA certificate configuration on an RSA Security Analytics 10.3 server prior to an upgrade and How to Install a Public CA Certificate on RSA Security Analytics 10.4.0.2 and Above, the workaround below may be performed to reapply the original keystore.
However, if a backup was made to the /opt/rsa/jetty9/etc/jetty-ssl.xml file as instructed in the installation guide and in the knowledgebase articles entitled How to back up a public CA certificate configuration on an RSA Security Analytics 10.3 server prior to an upgrade and How to Install a Public CA Certificate on RSA Security Analytics 10.4.0.2 and Above, the workaround below may be performed to reapply the original keystore.
Workaround
Follow the instructions below to replace the new jetty-ssl.xml file that is generated by the Puppet module with the backed up file from a previous version.
This workaround assumes that the backup file is located here: /opt/rsa/jetty9/etc/jetty-ssl.xml.bak
Issuing the puppet agent -t command will display output similar to the example below.
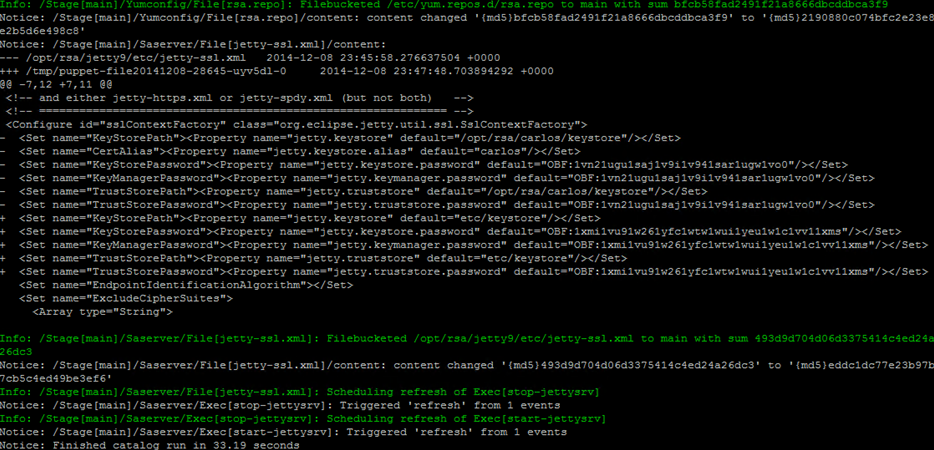 Image description
Image description
Allow several minutes for the Jetty web server to fully initialize before attempting to navigate to the user interface in a web browser. After that time, the custom certificate should be present.
If you are unsure of any of the steps above or experience any issues, contact RSA Support and quote this article number for further assistance.
This workaround assumes that the backup file is located here: /opt/rsa/jetty9/etc/jetty-ssl.xml.bak
- Connect to the Security Analytics server via SSH as the root user.
- Issue the command below to temporarily stop the puppetmaster service.
service puppetmaster stop
- Replace the Jetty keystore file with the backed up file from the previous version with the command below and confirm the operation.
cp /opt/rsa/jetty9/etc/keystore.bak /opt/rsa/jetty9/etc/keystore
- Replace the jetty-ssl.xml file in the Puppet module with the backed up file from the previous version with the command below and confirm the operation.
cp /opt/rsa/jetty9/etc/jetty-ssl.xml.bak /etc/puppet/modules/saserver/files/jetty-ssl.xml
- Start the puppetmaster service.
service puppetmaster start
- Push the changed file to the Jetty web server and automatically restart the jettysrv service with the command below.
puppet agent -t
Issuing the puppet agent -t command will display output similar to the example below.
 Image description
Image descriptionAllow several minutes for the Jetty web server to fully initialize before attempting to navigate to the user interface in a web browser. After that time, the custom certificate should be present.
If you are unsure of any of the steps above or experience any issues, contact RSA Support and quote this article number for further assistance.
Tags (33)
- Appliance
- Broker
- Broker Appliance
- Core Appliance
- Customer Support Article
- Head Unit
- HeadUnit
- KB Article
- Knowledge Article
- Knowledge Base
- NetWitness
- NetWitness Appliance
- NetWitness Broker
- NetWitness Head Unit
- NetWitness Platform
- NetWitness Server
- NetWitness UI
- NW
- NW Appliance
- NwBroker
- RSA NetWitness
- RSA NetWitness Platform
- RSA NetWitness UI
- RSA Security Analytics
- RSA Security Analytics UI
- Security Analytics
- Security Analytics Server
- Security Analytics UI
- SIEM
- UI
- UI Server
- User Interface
- Web Interface
No ratings
In this article
Related Content

© 2022 RSA Security LLC or its affiliates. All rights reserved.
