This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
NetWitness Knowledge Base Archive
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- NetWitness Community
- NetWitness Knowledge Base Archive
- How to configure RSA Security Analytics to use Pluggable Authentication Modules (PAM) RADIUS to send...
-
Options
- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
How to configure RSA Security Analytics to use Pluggable Authentication Modules (PAM) RADIUS to send two-factor authentications to an RSA Authentication Manager deployment
Article Number
000034701
Applies To
RSA Product Set: SecurID, NetWitness Logs and Packets (formerly Security Analytics)
RSA Product/Service Type: Authentication Manager, Security Analytics UI
RSA Version/Condition: RSA Authentication Manager 8.2, RSA Security Analytics 10.6.1.1
Platform: SUSE Enterprise Linux/CentOS
RSA Product/Service Type: Authentication Manager, Security Analytics UI
RSA Version/Condition: RSA Authentication Manager 8.2, RSA Security Analytics 10.6.1.1
Platform: SUSE Enterprise Linux/CentOS
Issue
This article provides information on integrating RSA NetWitness Logs and Packets and RSA SecurID to provide better security when logging in the RSA Security Analytics user interface.
Resolution
This topic explains how to configure RSA Security Analytics to use Pluggable Authentication Modules (PAM) RADIUS to authenticate external user logins.
PAM login capability involves two separate components:
The PAM modules and associated services output information to /var/log/messages and /var/log/secure. These outputs can be used to assist in troubleshooting configuration problems.
This completes the PAM RADIUS configuration.
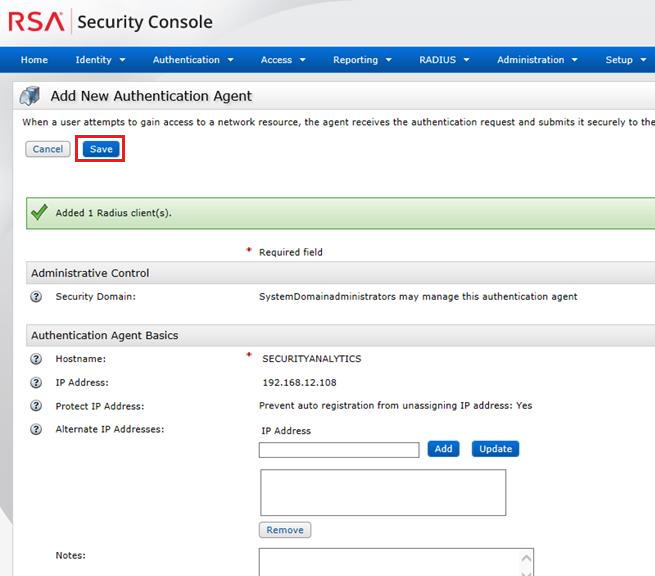 Image description
Image description
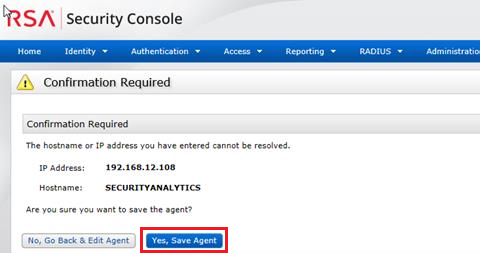 Image description
Image description
The completes the configuration for NSS UNIX.
 Image description
Image description
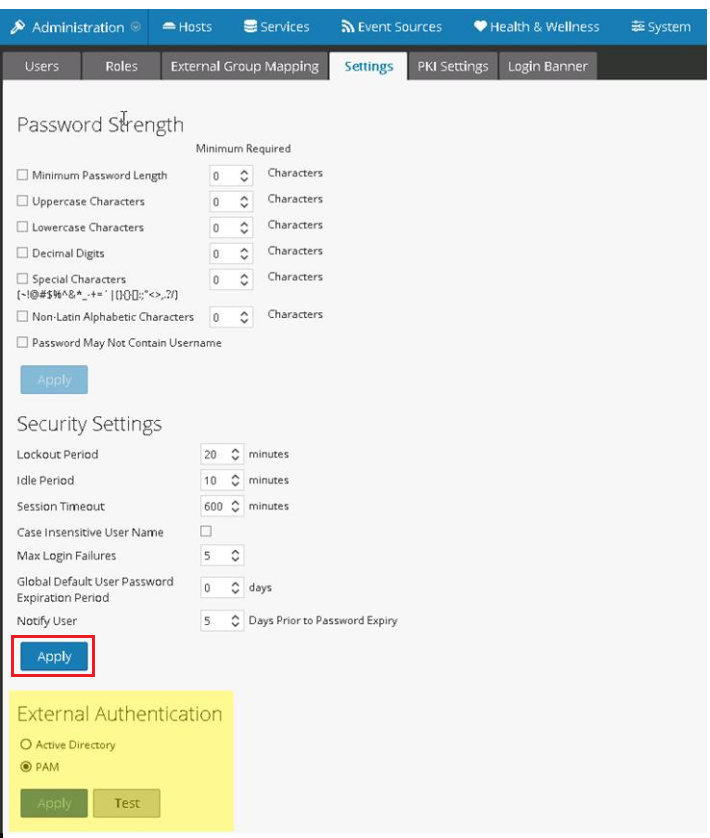 Image description
Image description
PAM is enabled and Active Directory is automatically disabled. The Active Directory configuration settings are stored and hidden.
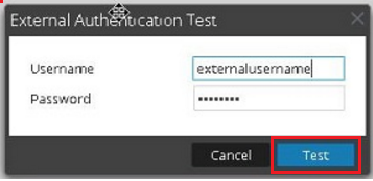 Image description
Image description
The external username must exist as a User ID in the Authentication Manager database with an authenticator assigned. Remember to have a real-time authentication activity monitor running when performing test authentications. To launch the monitor,
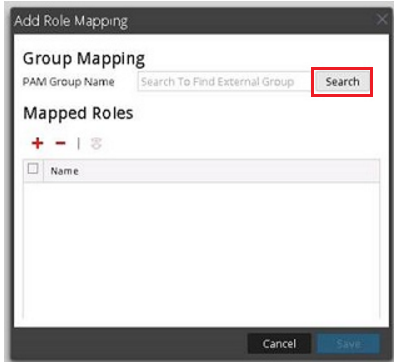 Image description
Image description
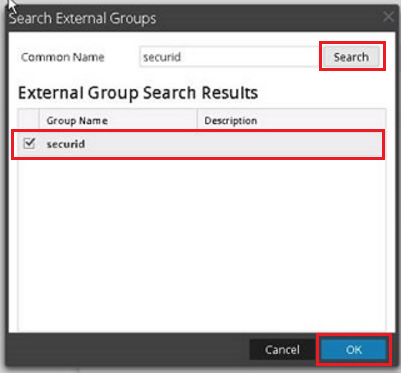 Image description
Image description
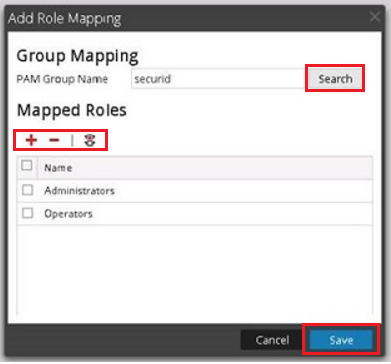 Image description
Image description
In this example; the operating system group name securid has Operators and Administrators as mapped roles:
 Image description
Image description
 Image description
Image description
PAM login capability involves two separate components:
- Pluggable Authentication Module (PAM) for user authentication
- Name Service Switch (NSS) for group authorization
Pluggable Authentication Module
PAM is a Linux-provided library responsible for authenticating users against authentication providers such as RADIUS.
Name Service Switch
NSS is a Linux feature that provides databases that the operating system and applications use to discover information like hostnames; user attributes such as the home directory, primary group, and login shell; and to list users that belong to a given group. Similar to PAM, NSS is configurable and uses modules to interact with different types of providers. RSA Security Analytics uses OS-provided NSS capabilities to authorize external PAM users by looking up whether a user is known to NSS and then requesting from NSS the groups of which that user is a member. RSA Security Analytics compares the results of the request to the RSA Security Analytics External Group Mapping and, if a matching group is found, the user is granted access to log on to SA with the level of security defined in the External Group Mapping.
Prerequisites
- This feature is only available for EL6-based RSA Security Analytics version 10.4 or later.
- Before beginning the setup of PAM, review the procedure and gather the external authentication server details depending on the PAM module you want to implement.
- Before beginning the setup of NSS, review the procedure, identify the group names that you will use in the External Group mapping, and gather the external authentication server details, depending on the NSS service being used.
- If you purchased a new host with RSA Security Analytics 10.4 or later installed, the required rpm packages for RADIUS are installed by default.
- Before beginning setup of PAM in RSA Security Analytics, identify the group names that you will use in the External Group mapping. When mapping roles, the role in RSA Security Analytics must match a group name that exists in the external authentication server.
Configure the PAM module - RADIUS
- If you have upgraded to RSA Security Analytics 10.6, execute the following command as root to check if the PAM RADIUS package is installed:
rpm -qa | grep pam_radius_auth
[root@ ~]# rpm -qa | grep pam_radius_auth
pam_radius_auth-1.3.17-1.x86_64
[root@ ~]#
yum --enablerepo=nwupdates install pam_radius_auth- Edit the radius configuration file /etc/raddb/server and update it with the RSA Authentication Manager instance hostname, RADIUS port, RADIUS shared secret and timeout value:
# server[:port] shared_secret timeout (s)
#127.0.0.1 secret 1
#other-server other-secret 3
192.168.12.200:1812 securid 10- Edit the RSA Security Analytics server PAM configuration file /etc/pam.d/securityanalytics to add the following line. If the file does not exist, create it and add the following line:
auth sufficient pam_radius_auth.soThe PAM modules and associated services output information to /var/log/messages and /var/log/secure. These outputs can be used to assist in troubleshooting configuration problems.
Adding a RADIUS Client and Associated Agent in the Authentication Manager Security Console
- Log into the RSA Security Console as an administrator.
- Select RADIUS > RADIUS Client > Add New.
- Enter the following information:
- A name for the RADIUS client,
- A valid IPv4 address,
- For Make/Model, select Standard RADIUS.
- Enter a RADIUS Shared Secret.
- Click Save & Create Associated RSA Agent.
For example,
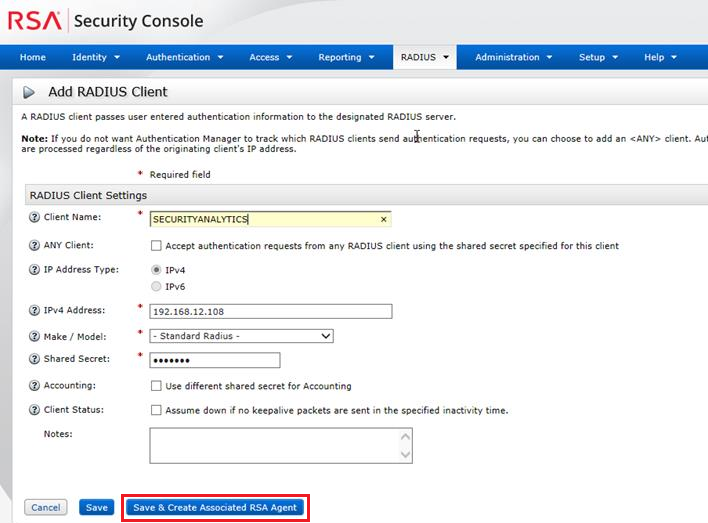 Image description
Image description
 Image description
Image description- On the page to add a new authentication agent, click Save.
 Image description
Image description- Where the RSA Authentication Manager instance cannot lookup the authentication agent name on the network the following is seen, click Yes, Save Agent.
 Image description
Image descriptionConfigure and Test the NSS Service
No configuration is necessary to enable the NSS Unix module; it is enabled in the host operating system by default. To authorize a user for a specific group, simply add that user to the operating system and add them to a group.
- Create an operating system group and add an external user to this new group.
groupadd <groupname>- Add an external user to the operating system and make the user a member of the new group.
adduser -G <groupname> -M -N <externalusername>This does not permit or allow access to the RSA Security Analytics server console or command line with this username. The <externalusername> must match the user ID in the RSA Authentication Manager database.
The completes the configuration for NSS UNIX.
Testing
- To test whether NSS is working with any of the previous NSS services, use the following commands:
getent passwd <externalusername>
getent group <groupname>For example:
[root@~]# getent passwd myuser
myuser:*:10000:10000::/home/myuser:/bin/sh
[root@~]# getent group mygroup
mygroup:*:10000:myuser3- If neither command produces output, NSS is not working properly for external authorization.
Enabling PAM on the RSA Security Analytics Server
- Log into RSA Security Analytics web interface using an administrative account.
 Image description
Image description- Under Dashboard select Administration > Security.
- Click the Settings tab.
- Under Extension Authentication, select PAM.
- Click Apply.
 Image description
Image descriptionPAM is enabled and Active Directory is automatically disabled. The Active Directory configuration settings are stored and hidden.
- Perform a test authentication with the PAM configuration.
- Click the Test button and enter the external username and passcode in the Password field.
- Click the Test button for the External Authentication Test.
 Image description
Image descriptionThe external username must exist as a User ID in the Authentication Manager database with an authenticator assigned. Remember to have a real-time authentication activity monitor running when performing test authentications. To launch the monitor,
- Login to the Security Console
- Select Reporting > Real-time Activity Monitors > Authentication Activity Monitor.
- Click Start Monitor.
- Use External Group Mapping to map the operating system group to a mapped role in the RSA Security Analytics UI.
- In the Security View click the External Group Mapping tab.
- Click + to add a Role Mapping.
- Click the Search button.
 Image description
Image description- Enter the operating system group name setup earlier into the Common Name field and click Search. In this example the group name is called securid. The group name is found in the External Group Search Results, check the Group Name and click OK.
 Image description
Image description- Click + to list the available roles.
- Select the required Role(s) and click Add.
- After confirming Group Mapping and Mapped Roles click Save.
 Image description
Image descriptionIn this example; the operating system group name securid has Operators and Administrators as mapped roles:
 Image description
Image description- Where the test authentication worked, test the external user account and log into the RSA Security Analytics web interface.
- Enter the passcode into the Password field.
- Click Login.
 Image description
Image descriptionNotes
The RSA Security Analytics login cannot handle New PIN Mode or Next Tokencode Mode for RSA SecurID authentications.
Tags (63)
- 10.6
- 10.6 Service Pack 1
- 10.6 Service Pack 1 Patch 1
- 10.6 SP1
- 10.6 SP1 P1
- 10.6.1
- 10.6.1.1
- 10.6.1.1.x
- 10.6.1.x
- 10.6.x
- 10.x
- 8
- 8.1
- 8.1.x
- 8.2
- 8.2.x
- 8.x
- AM
- Appliance
- Auth Manager
- Authentication Manager
- Customer Support Article
- KB Article
- Knowledge Article
- Knowledge Base
- NetWitness
- NetWitness Platform
- NetWitness UI
- NW
- RSA AM
- RSA Auth Manager
- RSA Authentication Manager
- RSA NetWitness
- RSA NetWitness Platform
- RSA NetWitness UI
- RSA SecurID
- RSA SecurID Access
- RSA SecurID Suite
- RSA Security Analytics
- RSA Security Analytics UI
- SecurID
- SecurID Access
- SecurID Appliance
- SecurID Suite
- Security Analytics
- Security Analytics UI
- SIEM
- UI
- User Interface
- Version 10
- Version 10.6
- Version 10.6.1
- Version 10.6.1.1
- Version 10.6.1.x
- Version 10.6.x
- Version 10.x
- Version 8
- Version 8.1
- Version 8.1.x
- Version 8.2
- Version 8.2.x
- Version 8.x
- Web Interface
No ratings
In this article
Related Content

© 2022 RSA Security LLC or its affiliates. All rights reserved.
