This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
NetWitness Knowledge Base Archive
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- NetWitness Community
- NetWitness Knowledge Base Archive
- How to properly configure Global Notification for Script
-
Options
- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
How to properly configure Global Notification for Script
Article Number
000040015
Applies To
RSA Product Set: RSA NetWitness Platform
RSA Product/Service Type: Security Analytics Server
RSA Version/Condition: 11.5.2.0
Platform: CentOS
O/S Version: 7
RSA Product/Service Type: Security Analytics Server
RSA Version/Condition: 11.5.2.0
Platform: CentOS
O/S Version: 7
Issue
If you configure Global Notification for Script, you may face an issue to execute the script even though the ESA rule is fired.
In this case, It is hard to find the root cause because there is no error message appeared regarding this issue.
There is a document on how to configure("Configure Script as a Notification" in the System Configuration Guide), but it is not enough to cover this topic.
In this case, It is hard to find the root cause because there is no error message appeared regarding this issue.
There is a document on how to configure("Configure Script as a Notification" in the System Configuration Guide), but it is not enough to cover this topic.
Resolution
To configure successfully, you need to consider followings
1. You can use "Default Script Template" as a template.
2. UI pop-up appears when you define script as shown below "Script will be saved to /opt/rsa/esa/scripts" but it is actually saved to mongo db since 11.3.
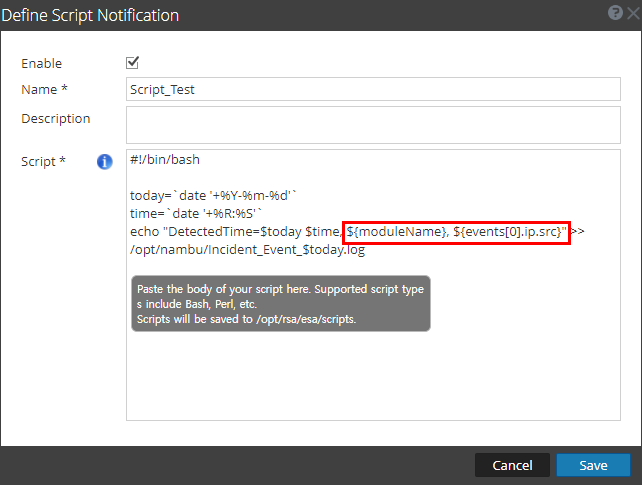 Image description
Image description
3. You must locate the script under /tmp, otherwise script will not execute.
4. In case of bash shell, you can use following syntax(echo $*) to get all ESA parameters below and this is sample script output.
 Image description
Image description
1. You can use "Default Script Template" as a template.
2. UI pop-up appears when you define script as shown below "Script will be saved to /opt/rsa/esa/scripts" but it is actually saved to mongo db since 11.3.
 Image description
Image description3. You must locate the script under /tmp, otherwise script will not execute.
4. In case of bash shell, you can use following syntax(echo $*) to get all ESA parameters below and this is sample script output.
 Image description
Image description
# cat /tmp/bash_test.txt
Tue Dec 7 08:17:57 UTC 2021
{"id": "41a15340-bb5e-45f9-a049-e2b49f17dca3", "severity":3, "time": "2021-12-07T08:17:57Z", "module_name" : "CS support rule for Script", "events": [{"analysis_session" : ["request no payload", "response no payload", "ratio high transmitted", "host not listening", "zero payload", "session size 0-5k"], "attack_tactic" : "exfiltration", "attack_technique" : "data transfer size limits", "attack_tid" : "T1030", "capture_port" : "eth0", "com_rsa_netwitness_streams_arrival_sequence" : 11, "com_rsa_netwitness_streams_arrival_timestamp" : 1638865076236, "com_rsa_netwitness_streams_source_trail" : ["admin@192.168.26.105:50005"], "com_rsa_netwitness_streams_stream" : "c-s-support-sa-managed-stream", "community_id" : "1:xa3WM28Id5DyRYPnARWOx/BHJ3M=", "did" : "pkthybrid", "direction" : "lateral", "esa_time" : 1638865077237, "eth_dst" : "00:50:56:01:36:82", "eth_dst_vendor" : "VMware, Inc.", "eth_src" : "00:50:56:01:46:75", "eth_src_vendor" : "VMware, Inc.", "eth_type" : 2048, "event_source_id" : "192.168.26.105:50005:1292845", "feed_name" : ["investigation", "investigation", "investigation", "investigation", "investigation", "investigation"], "inv_category" : ["operations", "operations", "operations", "operations", "operations", "operations"], "inv_context" : ["event analysis", "protocol analysis", "event analysis", "protocol analysis", "event analysis", "protocol analysis", "event analysis", "protocol analysis", "event analysis", "protocol analysis", "event analysis", "protocol analysis"], "ip_dst" : "192.168.26.109", "ip_proto" : 6, "ip_src" : "192.168.26.105", "lifetime" : 0, "medium" : 1, "netname" : ["private src", "private dst"], "packets" : 2, "payload" : 0, "payload_req" : 0, "payload_res" : 0, "rid" : 1292844, "service" : 0, "sessionid" : 1292845, "size" : 134, "streams" : 2, "tcp_dstport" : 4505, "tcp_flags" : 22, "tcp_flags_desc" : "syn", "tcp_srcport" : 34108, "tcpflags" : "syn", "time" : 1638865011000}]}Tags (56)
- 11.3
- 11.3.x
- 11.4
- 11.4.x
- 11.5
- 11.5.x
- 11.x
- Appliance
- Best Practice
- Best Practices
- Broker
- Broker Appliance
- Core Appliance
- Customer Support Article
- Head Unit
- HeadUnit
- Helpful Hints
- How To
- Informational
- Instructions
- KB Article
- Knowledge Article
- Knowledge Base
- NetWitness
- NetWitness Appliance
- NetWitness Broker
- NetWitness Head Unit
- NetWitness Platform
- NetWitness Server
- NW
- NW Appliance
- NwBroker
- Process Steps
- Recommendations
- Recommended
- Recommended Practice
- RSA NetWitness
- RSA NetWitness Platform
- RSA Security Analytics
- Security Analytics
- Security Analytics Server
- SIEM
- Tip & Tricks
- Tips and Tricks
- Tutorial
- UI Server
- Version 11
- Version 11.3
- Version 11.3.x
- Version 11.4
- Version 11.4.x
- Version 11.5
- Version 11.5.x
- Version 11.x
- Walk Through
- Walkthrough
No ratings
In this article
Related Content

© 2022 RSA Security LLC or its affiliates. All rights reserved.
