This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
NetWitness Knowledge Base Archive
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- NetWitness Community
- NetWitness Knowledge Base Archive
- Meta Overflown alarm of tcp.srcport on H&W
-
Options
- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Meta Overflown alarm of tcp.srcport on H&W
Article Number
000039695
Applies To
RSA Product Set: RSA NetWitness Platform
RSA Product/Service Type: Core Appliance
RSA Version/Condition: 11.4.x / 11.3.x
Platform: CentOS
O/S Version: 7
RSA Product/Service Type: Core Appliance
RSA Version/Condition: 11.4.x / 11.3.x
Platform: CentOS
O/S Version: 7
Issue
In Netwitness version 11.4 below, sometimes you may see Meta Overflown alarm of tcp.srcport or tcp.dstport on H&W as shown below.
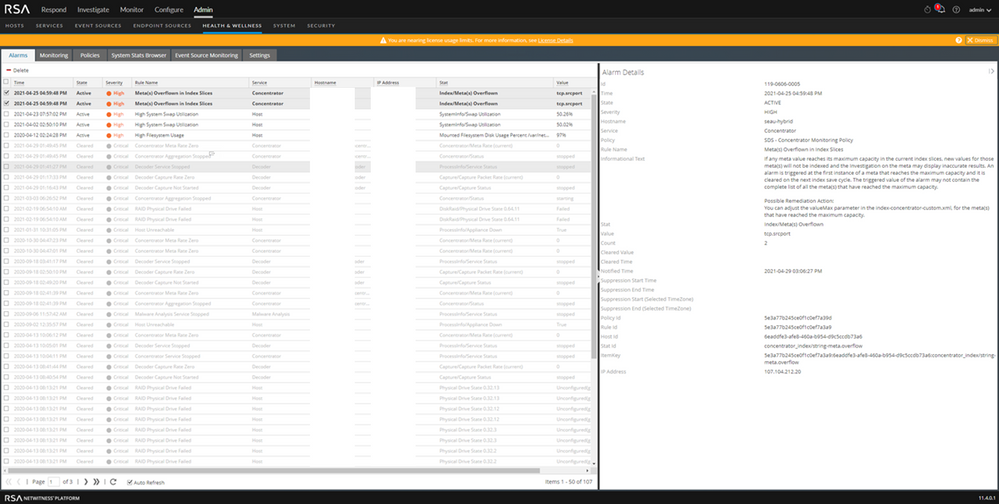 Image description
Image description
By default, valueMax of tcp.srcport is defined to 65536 as follows in index-concentrator.xml.
In theory, the port range is between 0~65535, so the max value can be 65536 depending on the customer's data or any custom parsers customer have.
You may observe "Metakey max capacity reached" messages in /var/log/messages as well.
This warning message is basically telling that the maximum capacity has reached and it will not take any new values.
But it doesn't mean that there are more values in this case.
For your information, you can monitor specific meta values inside index slices by using inspect in concentrator service.
 Image description
Image descriptionBy default, valueMax of tcp.srcport is defined to 65536 as follows in index-concentrator.xml.
# grep "tcp.srcport" /etc/netwitness/ng/index-concentrator.xml
<key description="TCP Source Port" name="tcp.srcport" format="UInt16" level="IndexValues" valueMax="65536">
<aliases copyFrom="tcp.srcport"/>
<keyref name="tcp.srcport"/>
<keyref name="tcp.srcport"/>In theory, the port range is between 0~65535, so the max value can be 65536 depending on the customer's data or any custom parsers customer have.
You may observe "Metakey max capacity reached" messages in /var/log/messages as well.
This warning message is basically telling that the maximum capacity has reached and it will not take any new values.
But it doesn't mean that there are more values in this case.
For your information, you can monitor specific meta values inside index slices by using inspect in concentrator service.
# NwConsole -c login localhost:50005 admin netwitness -c timeout 0 -c /index inspect key=tcp.srcport allSlices=True summarizeAllValues=True >> /root/tcp_sourceport.jsonResolution
Port range between 0 to 65535 is actually 65536 unique values.
Therefore, you need to change valueMax of tcp.srcport to 65537 to resolve this issue.
In spite of the data type(UInt16), the valueMax can be set for this key and it won't create any problems.
In Netwitness version 10.5 above, this value is set to 65537 by default.
Therefore, you need to change valueMax of tcp.srcport to 65537 to resolve this issue.
In spite of the data type(UInt16), the valueMax can be set for this key and it won't create any problems.
In Netwitness version 10.5 above, this value is set to 65537 by default.
# grep "tcp.srcport" /etc/netwitness/ng/index-concentrator.xml
<key description="TCP Source Port" name="tcp.srcport" format="UInt16" singleton="true" level="IndexValues" valueMax="65537">
<aliases copyFrom="tcp.srcport"/>
<keyref name="tcp.srcport"/>
<keyref name="tcp.srcport"/>Tags (46)
- 11.3
- 11.3.x
- 11.4
- 11.4.x
- 11.x
- Appliance
- Break Fix
- Break Fix Issue
- Broken
- Concentrator
- Concentrator Appliance
- Config
- Configuration
- Configuration Help
- Configuration Issue
- Configuration Problem
- Configuring Issue
- Configuring Problem
- Core Appliance
- Customer Support Article
- Issue
- Issue Configuring
- Issues
- KB Article
- Knowledge Article
- Knowledge Base
- NetWitness
- NetWitness Appliance
- NetWitness CConcentrator
- NetWitness Platform
- NW
- NW Appliance
- NwConcentrator
- Problem
- RSA NetWitness
- RSA NetWitness Platform
- RSA Security Analytics
- Security Analytics
- Setup Issue
- SIEM
- Version 11
- Version 11.3
- Version 11.3.x
- Version 11.4
- Version 11.4.x
- Version 11.x
100% helpful
(1/1)
In this article
Related Content

© 2022 RSA Security LLC or its affiliates. All rights reserved.
