This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
NetWitness Knowledge Base Archive
Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
Showing results for
- NetWitness Community
- NetWitness Knowledge Base Archive
- Newly created Incident Management (IM) aggregation rules for ESA alerts are processing old alerts in...
-
Options
- Subscribe to RSS Feed
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Newly created Incident Management (IM) aggregation rules for ESA alerts are processing old alerts in RSA Security Analytics
Article Number
000032434
Applies To
RSA Product Set: Security Analytics
RSA Product/Service Type: Incident Management, Event Stream Analysis (ESA), Security Analytics UI
RSA Version/Condition: 10.5.x, 11.X
Platform: CentOS
O/S Version: EL6
RSA Product/Service Type: Incident Management, Event Stream Analysis (ESA), Security Analytics UI
RSA Version/Condition: 10.5.x, 11.X
Platform: CentOS
O/S Version: EL6
Issue
Newly created Incident Management (IM) aggregation rules for ESA alerts are processing old alerts.
For instance, if an aggregation rule is created today, alerts in Incident Management Alerts Or SecOps Incidents contain alerts going as far back as a couple of months.
For instance, if an aggregation rule is created today, alerts in Incident Management Alerts Or SecOps Incidents contain alerts going as far back as a couple of months.
Cause
By default, aggregation rules will look up all the alerts in the alert database.
Resolution
In the aggregation rule, there is an option to select alerts based on "Date Created".
Add a condition for "Date Created" that is greater than or equal to the date desired in the aggregation rule itself.
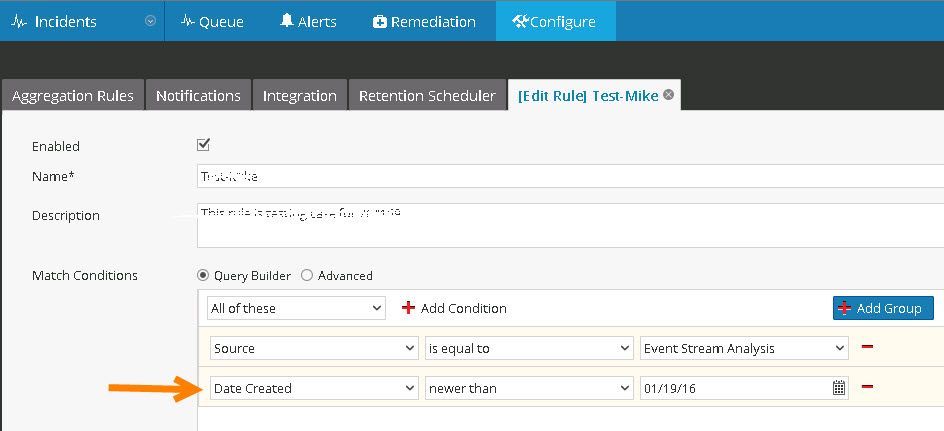 Image description
Image description
In 11.X version,
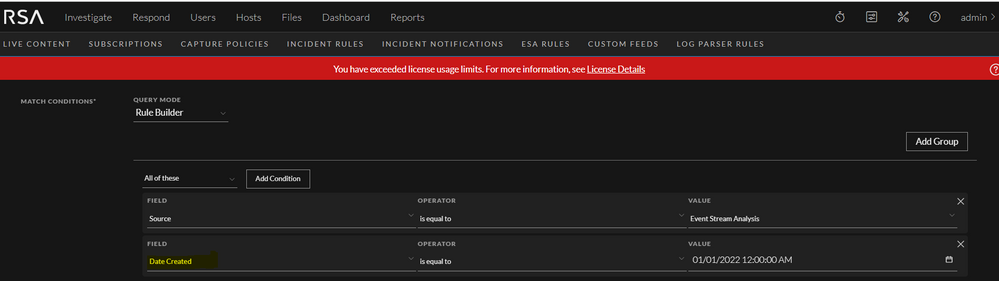 Image description
Image description
If Query Mode is Advanced for Incident rules, please use below syntax for Incident creation greater than the required date.
{"$and":[{"alert.source":"Event Stream Analysis"},{"alert.name":{"$in":["rule1", "rule2"]}},{"alert.timestamp":{"$gt":{"$date":"2021-12-30T12:00:30Z"}}}]}
Add a condition for "Date Created" that is greater than or equal to the date desired in the aggregation rule itself.
 Image description
Image descriptionIn 11.X version,
 Image description
Image descriptionIf Query Mode is Advanced for Incident rules, please use below syntax for Incident creation greater than the required date.
{"$and":[{"alert.source":"Event Stream Analysis"},{"alert.name":{"$in":["rule1", "rule2"]}},{"alert.timestamp":{"$gt":{"$date":"2021-12-30T12:00:30Z"}}}]}
Tags (58)
- 11.x
- Appliance
- Broker
- Broker Appliance
- Config
- Configuration
- Configure
- Configuring
- Core Appliance
- Customer Support Article
- ESA
- ESA Appliance
- ESA Service
- Event Stream Analysis
- Head Unit
- HeadUnit
- Helpful Hints
- How To
- Implementation
- Implementing
- Informational
- Instructions
- KB Article
- Knowledge Article
- Knowledge Base
- NetWitness
- NetWitness Appliance
- NetWitness Broker
- NetWitness Head Unit
- NetWitness Platform
- NetWitness Server
- NetWitness UI
- NW
- NW Appliance
- NwBroker
- Process Steps
- RSA NetWitness
- RSA NetWitness Platform
- RSA NetWitness UI
- RSA Security Analytics
- RSA Security Analytics UI
- Security Analytics
- Security Analytics Server
- Security Analytics UI
- Set Up
- Setup
- SIEM
- Tip & Tricks
- Tips and Tricks
- Tutorial
- UI
- UI Server
- User Interface
- Version 11
- Version 11.x
- Walk Through
- Walkthrough
- Web Interface
No ratings
In this article
Related Content

© 2022 RSA Security LLC or its affiliates. All rights reserved.
