- NetWitness Community
- Blog
- BadRabbit: a New Ransomware Outbreak
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Yesterday news emerged about a new ransomware outbreak dubbed Bad Rabbit. The new ransomware has some similarities to the Petya/Not Petya ransomware attack that took the world by storm last summer. Both ransomware families encrypt the entire disk. As of now, it appears that most reported victims are in Eastern Europe with some reports suggesting that some victims were detected in the United States. While the US-CERT issued a notice that it is aware of the attacks, it has no specific information on US victims.
Bad Rabbit binary is currently being delivered to the victim as a fake Adobe Flash update (SHA256: 630325cac09ac3fab908f903e3b00d0dadd5fdaa0875ed8496fcbb97a558d0da) through compromised websites, and one particular delivery domain, 1dnscontrol[.]com, has been identified in numerous Industry reports. Researchers at Cisco Talos demonstrated how BadRabbit victims were redirected to this delivery domain via compromised websites.
First, there was a POST request to 185.149.120[.]3/scholargoogle to collect some information such as user agent, referring site, cookie and domain name of the session. Next, the ransomware dropper was delivered via two paths:
- 1dnscontrol[.]com/index.php
- 1dnscontrol[.]com/flash_install.php
At this time, it appears that the delivery domain is no longer active; however, both the IP and domain have been placed into FirstWatch C2 feeds available in RSA Live with the following meta tags:
- threat.category = "ransomware"
- threat.desc = "badrabbit"
Executing the malware on a 32bits Windows machine, it dropped the following files on the system (names of the dropped files might vary from one system to another):
| File Path | SHA256 | Notes | |
|---|---|---|---|
| C:\Windows\cscc.dat | 682adcb55fe4649f7b22505a54a9dbc454b4090fc2bb84af7db5b0908f3b7806 | diskcryptor driver | |
| C:\Windows\infpub.dat | 14d82a676b63ab046ae94fa5e41f9f69a65dc7946826cb3d74cea6c030c2f958 | ||
| C:\Windows\dispci.exe | 8ebc97e05c8e1073bda2efb6f4d00ad7e789260afa2c276f0c72740b838a0a93 | diskcryptor client | |
| a81b01737a22b8dae8f3e4fe3693c2f56eae0c6e24670146d91832ba6b76c82f |
Executing the malware on a 64bits Windows machine, it dropped the following files:
| File Path | SHA256 | Notes | |
|---|---|---|---|
| C:\Windows\cscc.dat | 0b2f863f4119dc88a22cc97c0a136c88a0127cb026751303b045f7322a8972f6 | diskcryptor driver | |
| C:\Windows\infpub.dat | 14d82a676b63ab046ae94fa5e41f9f69a65dc7946826cb3d74cea6c030c2f958 | ||
| 8ebc97e05c8e1073bda2efb6f4d00ad7e789260afa2c276f0c72740b838a0a93 | diskcryptor client | |
| fdef2f6da8c5e8002fa5822e8e4fea278fba66c22df9e13b61c8a95c2f9d585f |
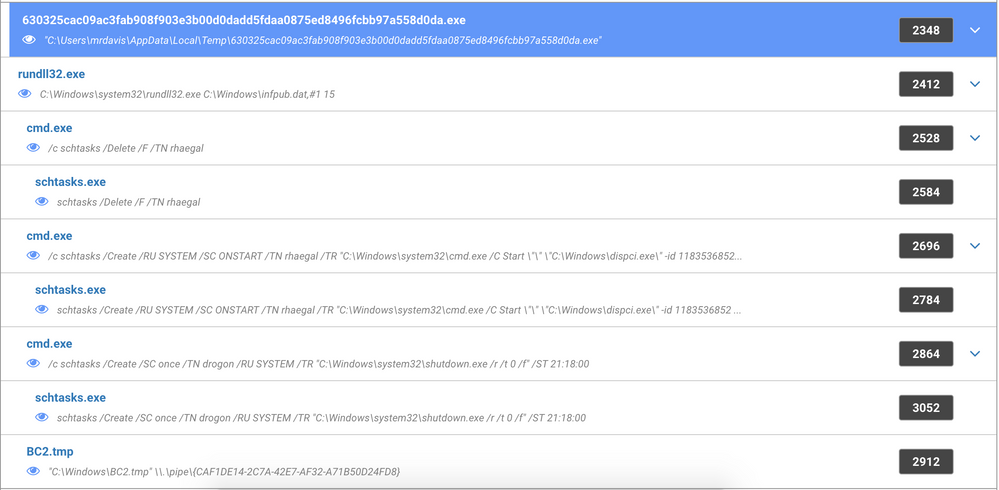
Here is a process tree after running the dropper:
The malware creates two scheduled tasks to perform the following:
- A scheduled task to run the open source utility DiskCryptor to encrypt the entire disk.
- A scheduled task to reboot the system at a certain time.
Strings embedded in the unpacked DLL suggest that the malware also targets a certain list of files for encryption:
- .3ds.7z.accdb.ai.asm.asp.aspx.avhd.back.bak.bmp.brw.c.cab.cc.cer.cfg.conf.cpp.crt.cs.ctl.cxx.dbf.der.dib.disk.djvu.doc.docx.dwg.eml.fdb.gz.h.hdd.hpp.hxx.iso.java.jfif.jpe.jpeg.jpg.js.kdbx.key.mail.mdb.msg.nrg.odc.odf.odg.odi.odm.odp.ods.odt.ora.ost.ova.ovf.p12.p7b.p7c.pdf.pem.pfx.php.pmf.png.ppt.pptx.ps1.pst.pvi.py.pyc.pyw.qcow.qcow2.rar.rb.rtf.scm.sln.sql.tar.tib.tif.tiff.vb.vbox.vbs.vcb.vdi.vfd.vhd.vhdx.vmc.vmdk.vmsd.vmtm.vmx.vsdx.vsv.work.xls.xlsx.xml.xvd.zip.
- Note: It remains unclear why the malware has a list of target file extensions, while it's behavior encrypts the whole disk.
The malware also drops mimikatz-like binaries to harvest credentials. Communication between those binaries and the malware is done through a named pipe as shown in the process tree above.
In addition to the stealers, the malware comes embedded with a list of default usernames and passwords. These credentials are used by the malware to try to login to other systems via SMB and infect them. It should be noted, that BadRabbit does not currently use the EternalBlue vulnerability for lateral movement; instead this is basic scanning and login attempts for the following shares.
- admin
- atsvc
- browser
- eventlog
- lsarpc
- netlogon
- ntsvcs
- spoolss
- samr
- srvsvc
- scerpc
- svcctl
- wkssvc
If a login attempt is successful, 'infpub.dat' is dropped into Windows directory and executed via SCManager and rundll.exe.
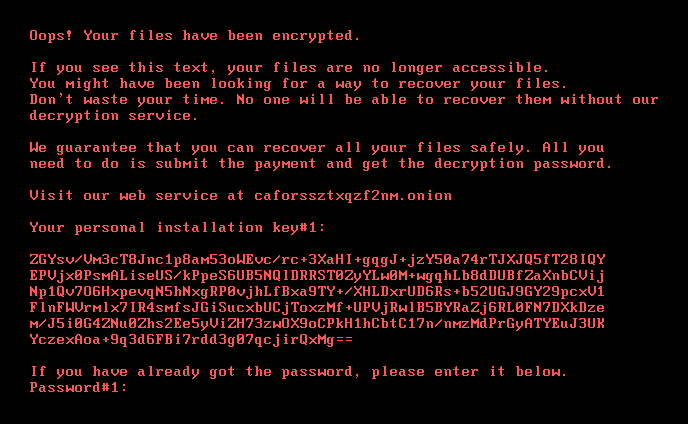
In it's final stages, Bad Rabbit executes a system reboot, after which the victim is presented with a ransom note:
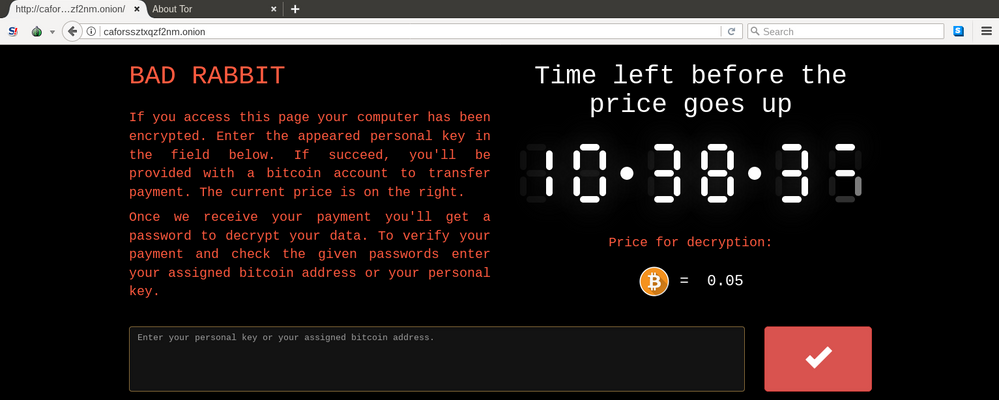
The helpful message on caforssztxqzf2nm[.]onion notifies victims of 0.05 Bitcoin ransom with a message suggesting that the price will go up after some 10+ hours.
Microsoft recently released a threat bulletin on Bad Rabbit [6]. It has the following instructions to stop the system from rebooting (thus stopping it from encrypting the disk):
- Check event logs for the following IDs: 1102 and 106
Event 1102 indicates that the audit log has been cleared, so previous activities can’t be seen.
Event 106 indicates that scheduled tasks "drogon" and "Rhaegel" have been registered (these are ransomware wipers)
If events 1102 and 106 are present, issue a shutdown -a to prevent a reboot
Halim Abouzeid has a detailed post on how the post infection activity looks in both NetWitness Packets and NetWitness Endpoint.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Using NetWitness to Detect Phishing reCAPTCHA Campaign
- Netwitness Platform Integration with Amazon Elastic Kubernetes Service
- Netwitness Platform Integration with MS Azure Sentinel Incidents
- Netwitness Platform Integration with AWS Application Load Balancer Access logs
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- New HotFix: Addresses Kernel Panic After Upgrading to 12.4.1
- Automation with NetWitness: Core and NetWitness APIs
- HYDRA Brute Force
- DDoS using BotNet Use Case
-
Announcements
64 -
Events
12 -
Features
12 -
Integrations
15 -
Resources
68 -
Tutorials
32 -
Use Cases
31 -
Videos
119