- NetWitness Community
- Blog
- Create an APT1 feed
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Mandiant recently published a report that many of you may have read. This report included an appendix which lists hundreds of domains and IP ranges associated with investigations into a threat actor called "APT1". If you are using NetWitness Live subscription chances are you already have these domains and IPs listed as malicious. However, I thought it would be a good exercise to build my own feed from the Mandiant AP1 appendix information.
I decided to create a feed for the APT1 domains because there are over 2000 of them. It is possible to create lists in Informer to alert on domains but these should be limited to a few dozen or so. A large feed, on the other hand, can create meta at the Decoder with little effort. This is a better option when dealing with large numbers of domains or IP addresses.
A feed is built using a CSV file and a bit of XML. Both files are attached so you have an example.
Create your feed
First, create the XML file that calls back the alias.host meta. This will create an alert (Mandiant_APT1_Domain) when the alias.host meta matches something from our CSV index column.
e.g. Mandiant_APT1_Domain.csv
<FDF>
<FlatFileFeed name="Mandiant_APT1_Domain" path="Mandiant_APT1_Domain.csv" separator=",">
<MetaCallback name="hostnames" valuetype="Text" apptype="0" truncdomain="false">
<Meta name="alias.host" />
</MetaCallback>
<LanguageKeys>
<LanguageKey name="alert" valuetype="Text" />
</LanguageKeys>
<Fields>
<Field index="1" type="index"/>
<Field index="2" type="value" key="alert"/>
</Fields>
</FlatFileFeed>
</FDF>
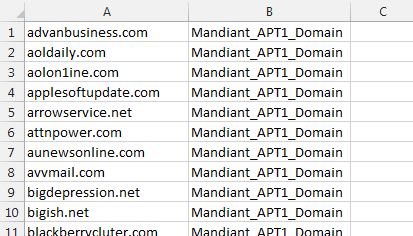
The CSV file can be put together easily in Excel using the Mandiant APT1 provided file Appendix D (Digital) - FQDNs.txt. Just add a column for the alert name that you want to see. This must align to the <Field index="2" type="value" key="alert"/> from your XML.
Now save your XML and CSV files together and give them a common name. e.g. Mandiant_APT1_Domain.csv and Mandiant_APT1_Domain.xml
Compile your feed
Compiling these files into a feed can be done many ways.
If you are using Live the easiest way is to drop the two files into a directory that will automatically build a Mandiant_APT1_Domain.feed file and publish it to any Decoders. By default the path is C:\Program Files (x86)\NetWitness\NetWitnes Live Manager\outgoing\devices\[decoder IP]\customfeeds\. If your XML and CSV file are correctly formatted they will be compiled by an automated process in Live and pushed out to the Decoder.
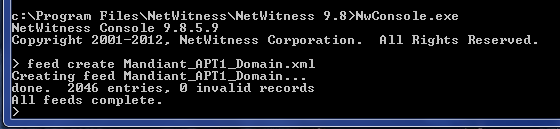
If you are not using Live the other way to test and build your feed is using the NwConsole command. This can be done locally on a Windows PC where you have installed Investigator. Copy the XML and CSV files to your NetWitness Investigator directory e.g. C:\Program Files\NetWitness\NetWitness 9.8\ and start a command prompt.
NwConsole.exe
> feed create Mandiant_APT1_Domain.xml
As seen in the screen shot above, the 2046 value returned in the output should correspond to the number of entries in your CSV file. If not, check your XML and CSV for errors.
Publish your feed
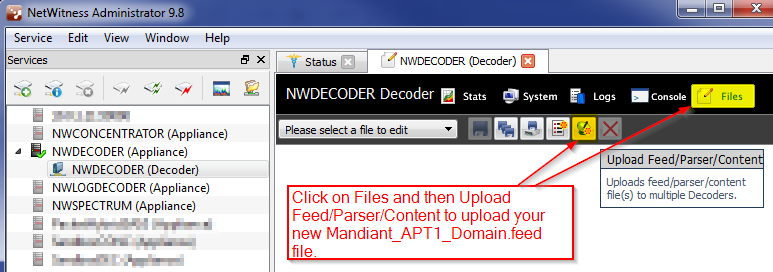
Now that you have made a Mandiant_APT1_Domain.feed file it is necessary to copy this to your Decoders for it to produce meta. You can Secure Copy (SCP) this over using something like WinSCP. Easier yet is to use NetWitness Administrator to copy up the file using the GUI.
Refresh the parser
One last step is required to tell the Decoder to make use of the new feed.
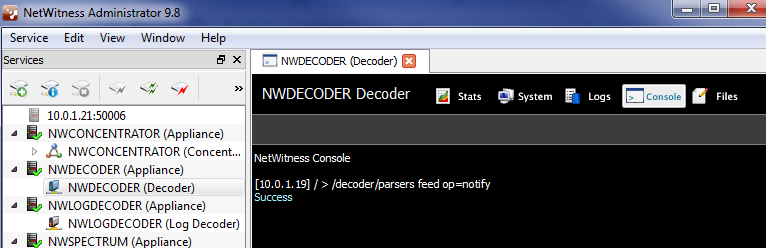
- From NetWitness Administrator, connect to and open the Decoder service.
- Navigate to the Console tab.
- Issue the following command to reload feeds on the Decoder:
/decoder/parsers feed op=notify
That is about it. If your network traffic ever creates meta for alias.host that belongs on your Mandiant_APT1_Domain.feed you will produce a new alert called Mandiant_APT1_Domain.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Using NetWitness to Detect Phishing reCAPTCHA Campaign
- Netwitness Platform Integration with Amazon Elastic Kubernetes Service
- Netwitness Platform Integration with MS Azure Sentinel Incidents
- Netwitness Platform Integration with AWS Application Load Balancer Access logs
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- New HotFix: Addresses Kernel Panic After Upgrading to 12.4.1
- Automation with NetWitness: Core and NetWitness APIs
- HYDRA Brute Force
- DDoS using BotNet Use Case
-
Announcements
64 -
Events
12 -
Features
12 -
Integrations
15 -
Resources
68 -
Tutorials
32 -
Use Cases
31 -
Videos
119