- NetWitness Community
- Blog
- Detecting HttpBrowser variants using Security Analytics
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
HttpBrowser is a Remote Access Trojan associated with cyberespionage campaigns. This blog will discuss how to detect its beaconing activity using RSA Security Analytics.
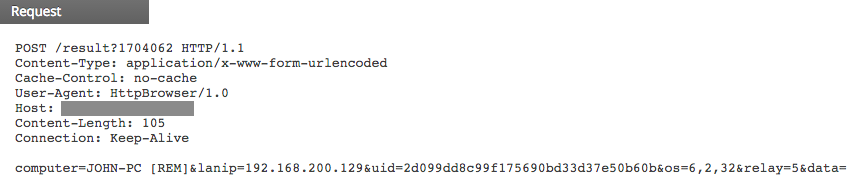
HttpBrowser sends information about the infected system to its C2 server via POST requests:
The querystring is the decimal representation of the value returned by the GetTickCount system call. It is the number of milliseconds that have elapsed since the system was started. In the request body itself, more information is included:
- computer: Machine hostname [username]
- lanip: IP address of the infected machine
- uid: An encoded value that has the Machine GUID and its volume serial number
- os: Windows Major version, Windows Minor version, System architecture
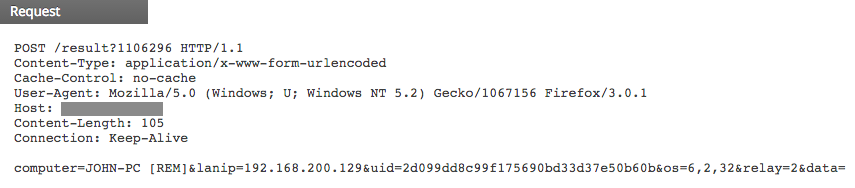
Malware researchers called this family HttpBrowser based on the unique User-Agent string used by its variants. However, recent HttpBrowser binaries dropped that UA string altogether and started using a common one in order to bypass signatures and blend in with other network traffic.
Except for the UA string, everything else stays the same. That’s how the traffic looks in Security Analytics Investigator:
Assuming the appropriate meta keys are enabled, the following query can be used to detect HttpBrowser network activity:
action = 'post' && directory = '/' && filename = 'result' && query exists
Scan results for an HttpBrowser variant can be viewed here.
All the IOC from those HTTP sessions were added to the following RSA FirstWatch Live feeds:
- RSA FirstWatch APT Threat Domains
- RSA FirstWatch APT Threat IPs
If threat.desc meta key is enabled then you can use the following app rule:
threat.desc = 'apt-httpbrowser-c2'
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Using NetWitness to Detect Phishing reCAPTCHA Campaign
- Netwitness Platform Integration with Amazon Elastic Kubernetes Service
- Netwitness Platform Integration with MS Azure Sentinel Incidents
- Netwitness Platform Integration with AWS Application Load Balancer Access logs
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- New HotFix: Addresses Kernel Panic After Upgrading to 12.4.1
- Automation with NetWitness: Core and NetWitness APIs
- HYDRA Brute Force
- DDoS using BotNet Use Case
-
Announcements
64 -
Events
12 -
Features
12 -
Integrations
15 -
Resources
68 -
Tutorials
32 -
Use Cases
31 -
Videos
119