- NetWitness Community
- Blog
- Detecting KeyBase keylogger variants using Security Analytics
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
A couple of weeks ago, security researchers at Palo Alto blogged about a new keylogger malware family called KeyBase. According to Palo Alto blog, the keylogger could be purchased directly from its author for $50. Although it is quite unsophisticated, KeyBase remains a threat that spreads through phishing campaigns mainly targeting high tech, higher education and retail industry.
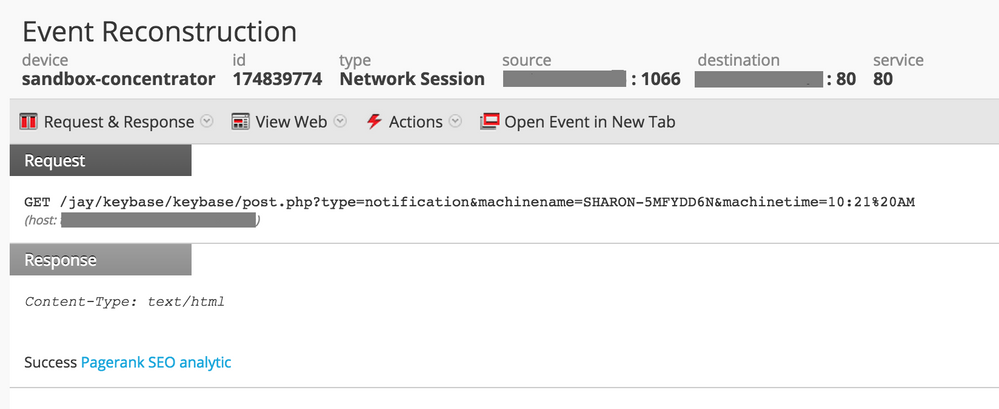
Once it runs on an infected host, the malware sends a notification to its C2 server. Time on the host and its name are sent in clear in the query string of the URL:
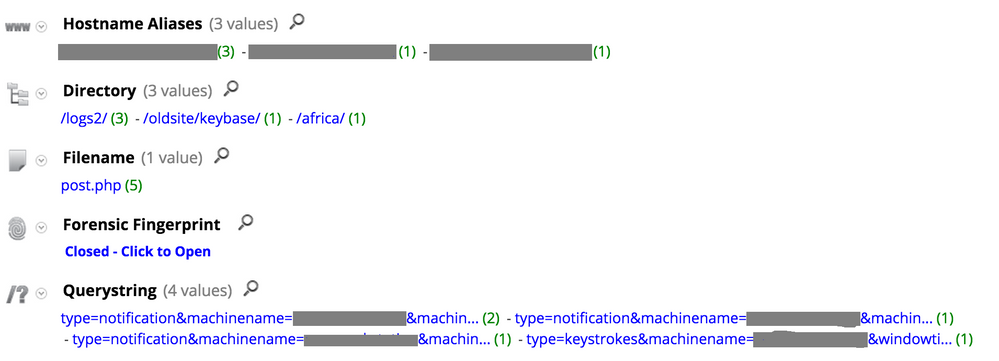
For KeyBase variants C2 beaconing activity, filename and query string format are fixed. However, directory names vary from one server to another:
Given all the network artifacts mentioned above and assuming the appropriate meta keys are enabled, an analyst can develop an app rule on RSA Security Analytics to detect the malicious traffic. The following query can be used:
filename = 'post.php' && query begins 'type=' && client !exists
Scan results for a couple of KeyBase variants can be found on VirusTotal:
SHA1: 6569a933f82c9ff8c06c2cfc70da0efd92d78a95
SHA1: ef0d13645fab775a21f00ffff5b587955884498c
Finally, all of the IOCs from those HTTP sessions were added to RSA FirstWatch Live feeds.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Using NetWitness to Detect Phishing reCAPTCHA Campaign
- Netwitness Platform Integration with Amazon Elastic Kubernetes Service
- Netwitness Platform Integration with MS Azure Sentinel Incidents
- Netwitness Platform Integration with AWS Application Load Balancer Access logs
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- New HotFix: Addresses Kernel Panic After Upgrading to 12.4.1
- Automation with NetWitness: Core and NetWitness APIs
- HYDRA Brute Force
- DDoS using BotNet Use Case
-
Announcements
64 -
Events
12 -
Features
12 -
Integrations
15 -
Resources
68 -
Tutorials
32 -
Use Cases
31 -
Videos
119