- NetWitness Community
- Blog
- Detecting Malicious and Suspicious User-Agent Strings
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
RSA Firstwatch shines a spotlight in the darker corners of the Internet to better understand Internet Fraud and Criminal trends online. When possible, RSA Firstwatch members will use this space to share information about some of our findings.
Every mature Enterprise strives to create a standardized image for their endpoint workstations, and they often refer to this image as their "Gold Release." These images typically include a hardened operating system, a default browser, a version of Java, the company's preferred Office workflow application suite, and other helper applications such as flash, PDF reader, and a standardized AV suite. Once that Gold Release is pushed out to the endpoints, Enterprise managers typically expend a lot of audit hours and time to ensure that the endpoints aren't changed too badly by the users or by unauthorized software installations.
It is often frustrating enough that end users install silly software that isn't needed- like Weatherbug, Yahoo Search Toolbars, Daily Coupon Alerting software- and even more frustrating when users install applications that violate corporate policy such as Online Backup suites, XDrive, Bittorrent, MIRC or other applications. But with today's malware and adware, many of these endpoint alterations to your Gold Release comes accidentally via Java exploits, Adware phishing or trojanized flash games. Detecting these types of malware is often as easy as analyzing the rarest user-agent strings on your network.
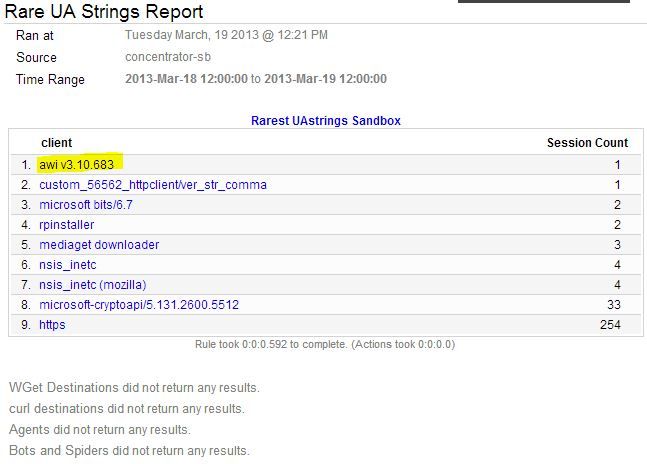
You should download and install the attached Informer Report below. It can be further customized to look for other known User-Agent abnormalities you are interested in. To show a real-life example of a malicious UA string, take a look at the screenshot I ran this morning:
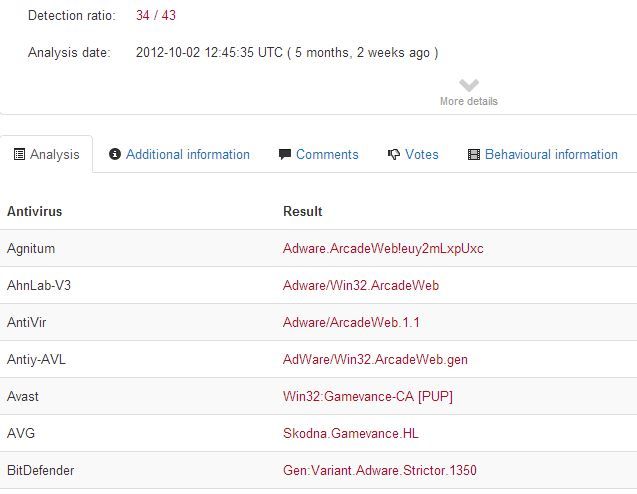
This report looks for the rarest clients where an OS or browser doesn't exist. I have highlighted the AWI v3 user-agent string. A google search shows that this string is a known malicious string used to download additional trojan horses according to VirusTotal.
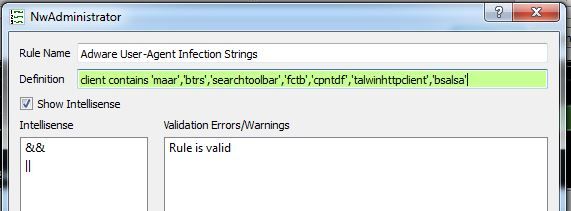
And of course, now that you know that string is malicious, a simple rule can be written to create an alert to notify you of its presence in the future. I also have attached a couple of rules to this post that you can deploy to your decoders. Usual caveat of "Your Mileage May Vary" applies.
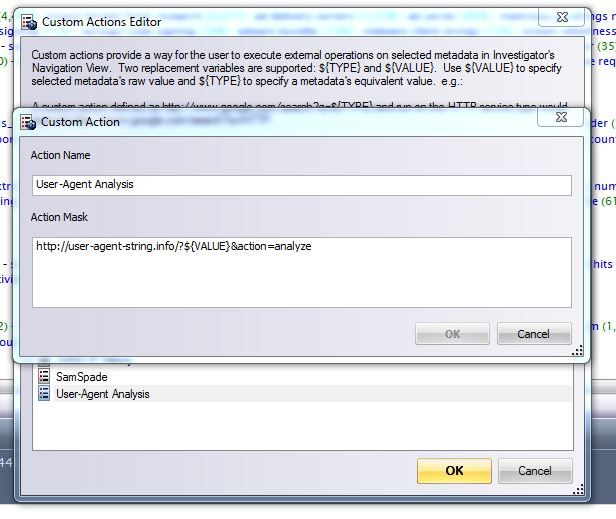
If you need help understanding what all of the pieces of a User-Agent string represent, there are online resources that decode them for you. My favorite site for this is user-agent-string.info. I have created a custom action to send client strings directly to the site from within Investigator. The custom action should be called "UA Analysis" and the action string is:
http://user-agent-string.info/?${VALUE}&action=analyze
Creating rules to normalize your user-agent strings will allow you to passively monitor your endpoints for out-of-date applications and unauthorized software. And this method can often be quicker, less network intensive, and even more accurate than an active vulnerability and compliance scanner. So give it a try and let us know what you think.
Happy Hunting!
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Using NetWitness to Detect Phishing reCAPTCHA Campaign
- Netwitness Platform Integration with Amazon Elastic Kubernetes Service
- Netwitness Platform Integration with MS Azure Sentinel Incidents
- Netwitness Platform Integration with AWS Application Load Balancer Access logs
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- New HotFix: Addresses Kernel Panic After Upgrading to 12.4.1
- Automation with NetWitness: Core and NetWitness APIs
- HYDRA Brute Force
- DDoS using BotNet Use Case
-
Announcements
64 -
Events
12 -
Features
12 -
Integrations
15 -
Resources
68 -
Tutorials
32 -
Use Cases
31 -
Videos
119