- NetWitness Community
- Blog
- Detecting Sinkholed Domains in Your Environment
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
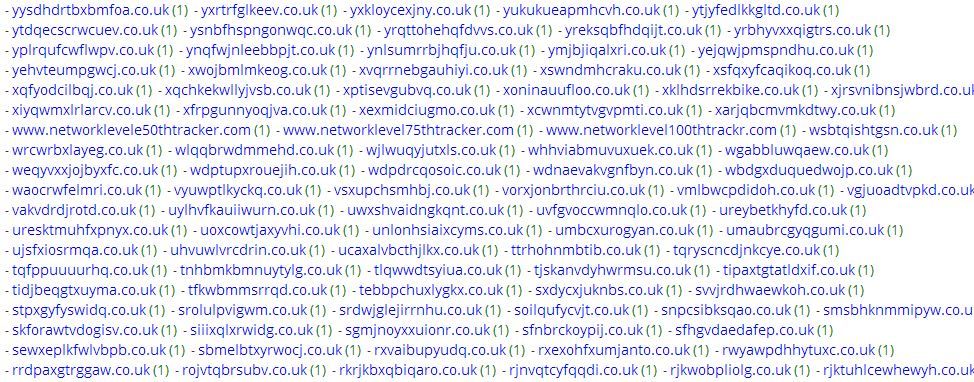
Over the past 90 days the RSA FirstWatch team has seen over 140 Dynamically Generated Algorithmic (DGA) Domains associated with a CryptoLocker variant that has been sinkholed, preventing the ransomware from locking up victim computers. In this case, all of the domains are in the ".co.uk" Top Level Domain.
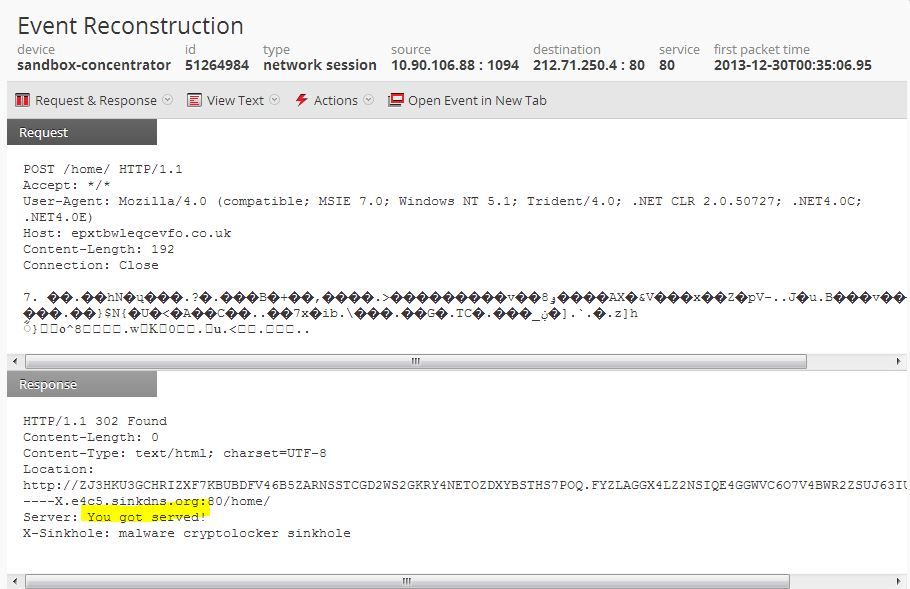
Rather than providing a list of each of these domains, it is actually quite easier to detect these connection attempts to these hosts, and all of the others yet to appear, by looking for the unique server banner hosted at the Sinkhole Site. Here is what a session of this traffic looks like:
See the highlighted "You got served!" server banner? Each of the 140 plus DGA connections each had this unique server banner. This would make for a very easy rule to detect beaconing to this particular family of CryptoLocker.
You can add this to another Security Analytics capture detection capability to detect the keyword "sinkhole" in a DNS name, which is effective at detecting other sinkholed malicious sites. The combination rule would be:
alias.host contains 'sinkhole' || server='You got served!'
Simply call the rule "Sinkholed Domains Warning Banners" and alert to your alerts field or SOC Alerts field, or perhaps risk.warning.
In addition, the same capture rule can be used as a custom query to search in the past for these specific meta elements, so you might be able to identify past sinkholed connection attempts.
Hope it works for you, and Happy Hunting!
Jan-31-2014 UPDATE!!
As a followup, we have identified several domains for this CryptoLocker variant that is not sinkholed. Those domains are:
ghvoersorwsrgef.org, yebdbfsomgdbqu.biz, usyusdoctfpnee.org, gavhopncgfmdq.org, gtdipovkdxricgl.biz, hkhrkvaycqoocii.org, huqenkdqtoatvnc.biz, vipclsgsdejgbpr.net, jchvghemqbmsj.org, mdaodtaifpkqkk.org, wxntojirxraawe.org, tdneerhyvurglh.org, stmdjbsbhojxp.net, ftltwlsqhegsnav.org, cvlagtrfprixtf.com, oxgufearvtqkwh.org, iryymjeallxat.net, immokfiqmakoo.com, nrpqtoiavtaf.net, dsgyvstkmmkb.com, xtjpdaobtycsr.org, tlsylihoxxmvc.org, tavnxtjxqyyprsi.net, qcsmufbvungpdck.org, ypxnqheckgjkbu.org, ynqpivhnrlud.biz, xvaxsxbptmerjb.com, xktrpjxjpeaocs.biz, wqblsdgavfmnlmv.biz, wifgslrwgvxwsy.com, vtcyrmxkkxvrick.biz, puwttsskvnchdl.com, njwaeqaydhbh.org, lbgtnunjpgirnbm.com, hwuiingqeuubi.org, digvfgleengor.net, dhjicdgfykqoq.org, axqrgervreovhhc.biz
It would be easier to blacklist the following IP addresses since there may be many more DGA domains that we haven't seen. Those IPs are:
188.65.211.137, 46.149.111.28, 95.59.26.43, 81.17.140.104, 109.234.154.254, 185.20.227.220, 195.210.47.118, 95.172.146.68, 144.76.192.130, 95.59.26.89, 93.189.44.187, 192.155.83.72, 83.69.233.25, 192.210.230.39
The best rule to detect this CryptoLocker Variant would be:
action=put && filename='<none>' && directory='/home/' && risk.info='http post missing content-type'
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Using NetWitness to Detect Phishing reCAPTCHA Campaign
- Netwitness Platform Integration with Amazon Elastic Kubernetes Service
- Netwitness Platform Integration with MS Azure Sentinel Incidents
- Netwitness Platform Integration with AWS Application Load Balancer Access logs
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- New HotFix: Addresses Kernel Panic After Upgrading to 12.4.1
- Automation with NetWitness: Core and NetWitness APIs
- HYDRA Brute Force
- DDoS using BotNet Use Case
-
Announcements
64 -
Events
12 -
Features
12 -
Integrations
15 -
Resources
68 -
Tutorials
32 -
Use Cases
31 -
Videos
119