- NetWitness Community
- Blog
- Detecting the Russian CryptoLocker Variant
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
RSAFirstWatch has been tracking a new variant of CryptoLocker, a malware family that will lock a local system until a ransom is paid to the malware author. This variant has a very specific beaconing pattern, and the detection rule for it is included below.
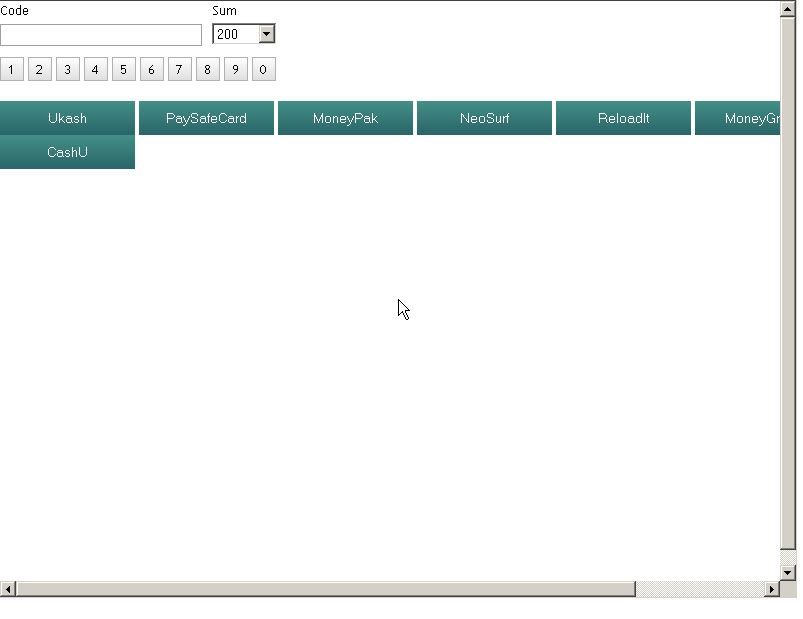
Once infected, a local system will display the following on the screen:
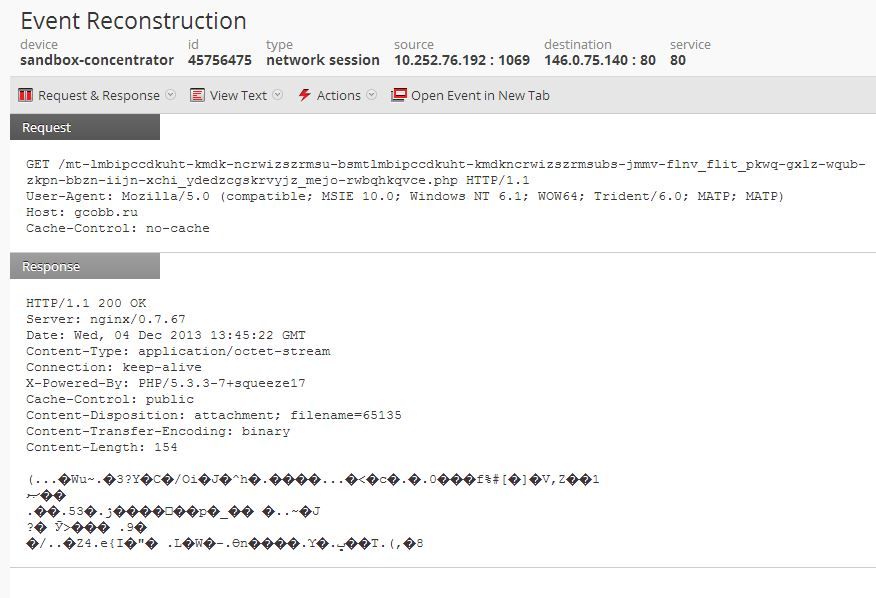
The local system calls a specific HTML or PHP page at a command and control server, which returns a binary encoded string. A session capture is below.
We have been tracking this malware for a while, and most of the hostnames this malware communicates with have already been added to the FirstWatch C2 Domains feed. There are some new domains that will be added to this feed today as well. The new domains are:
dzwej.ru, gcobb.ru, wrso.su, vepfx.ru
For those that do not subscribe to the FirstWatch feeds, you may be able to create a local feed to detect the following domains:
eywh.su, vepfx.ru, ighr.ru, dzwej.ru, bkdt.ru, bkvs.su, vqcny.su, vfoux.ru, rnye.su, xqcml.su, gcobb.ru, xshyq.ru, oxur.ru, gcxn.ru, efmg.su, reupy.su, hovmp.ru, tqzr.su, bfdfa.ru, yzaed.net, serc.su, mftaw.net, irvrh.su, nfymz.biz, hnvy.ru, efgb.su, ywsld.ru, xrwu.su, wviq.su, wrso.su, vymmf.ru, vdsvs.su, scey.su, qyds.ru, mvkbc.su, kagpk.ru, jvxiw.com, jcxb.su, idojv.net, htfq.ru, gybdr.biz, gcsqz.ru, fpgvu.com, erqkn.su, cmfdd.com, cffe.ru, bkvz.su
To detect the beaconing pattern, create a new rule on your decoders. Alert it to your alert field.
Call the rule CryptoLocker Beaconing. The rule content is:
service=80 && extension=html,php && attachment exists && filename length 40-u
Attached is a PCAP you can use to test your rule.
Good luck and Happy Hunting!
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Using NetWitness to Detect Phishing reCAPTCHA Campaign
- Netwitness Platform Integration with Amazon Elastic Kubernetes Service
- Netwitness Platform Integration with MS Azure Sentinel Incidents
- Netwitness Platform Integration with AWS Application Load Balancer Access logs
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- New HotFix: Addresses Kernel Panic After Upgrading to 12.4.1
- Automation with NetWitness: Core and NetWitness APIs
- HYDRA Brute Force
- DDoS using BotNet Use Case
-
Announcements
64 -
Events
12 -
Features
12 -
Integrations
15 -
Resources
68 -
Tutorials
32 -
Use Cases
31 -
Videos
119