- NetWitness Community
- Blog
- Detecting the Zusy Botnet Beaconing
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
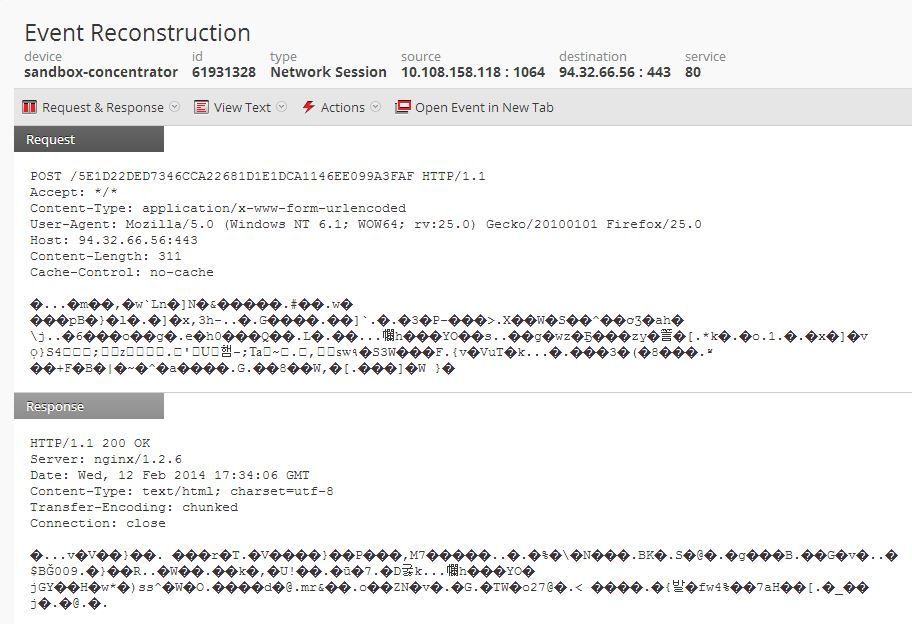
Since the beginning of February 2014, FirstWatch has seen a surge of Zusy malware in our database. Fortunately, this botnet is simple to detect. Here is what we've been seeing, starting with a session. You can see below that there is a post of a long hex string directly to an IP address instead of a hostname, using Firefox 25. You can also see some encoded traffic within the put strings, as well as encoded responses from the server.
This specific malware is identified at VirusTotal here as Zusy.
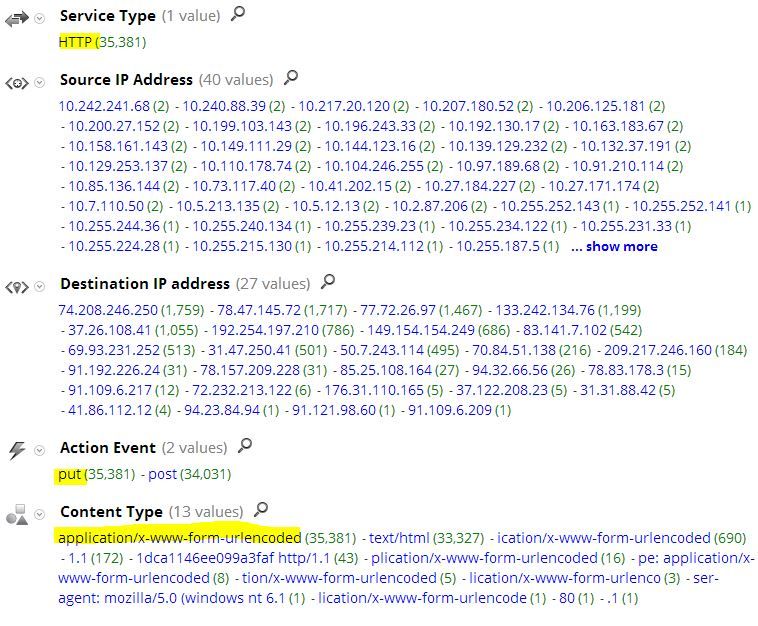
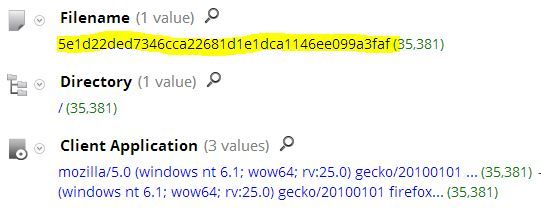
This specific botnet uses the same posted filename over and over for each of its c2 hosts. Drilling into the filename in our database reveals the following meta, showing that we have seen this filename 35,000 times since Feb 4. You can also see that each put command uses the url-encoding content type.
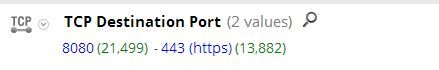
You will also note that this traffic is destined to a proxy port of 8080 and the SSL port of 443, however, the traffic is not encrypted.
By creating a simple rule of:
filename=5e1d22ded7346cca22681d1e1dca1146ee099a3faf
you can detect the many variants of Zusy since each seems to reuse this beaconing technique.
The destination IP addresses above that were seen to host the Command and Control services for this botnet have been added to the FirstWatch C2 feeds.
Good luck and happy hunting!
UPDATE!!
As it turns out, the filename shown above is unique to our environment. It appears to be a hash of some sort, and we are investigating further to determine what that hash is based upon. ThreatGrid is currently seeing the same activity, but from their sandbox, all beacon filenames are different- Their's is '46BC3A3BE440F54B18E7171E0C62710CCC46D034B9', and it never changes from the multiple variants of this malware they have captured.
So while the above rule would work great for us, it won't work for you. A better rule for now would be to search for the unique User-Agent string, which shows a Jan 1 2010 version of Firefox 25. Your rule would be:
client='mozilla/5.0 (windows nt 6.1; wow64; rv:25.0) gecko/20100101 firefox/25.0'
There is more to this malware, and we will be updating the community soon with a follow-on story. Stay tuned!
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Using NetWitness to Detect Phishing reCAPTCHA Campaign
- Netwitness Platform Integration with Amazon Elastic Kubernetes Service
- Netwitness Platform Integration with MS Azure Sentinel Incidents
- Netwitness Platform Integration with AWS Application Load Balancer Access logs
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- New HotFix: Addresses Kernel Panic After Upgrading to 12.4.1
- Automation with NetWitness: Core and NetWitness APIs
- HYDRA Brute Force
- DDoS using BotNet Use Case
-
Announcements
64 -
Events
12 -
Features
12 -
Integrations
15 -
Resources
68 -
Tutorials
32 -
Use Cases
31 -
Videos
119