- NetWitness Community
- Blog
- Detecting XtremeRAT variants using Security Analytics
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
XtremeRAT is a publicly available remote access tool that has been around for few years now. It has been used by different malicious actors for targeted attacks as well as cybercrime operations. In this blog post, we will discuss how to detect the traffic between an infected host and the C2 server controlled by the attacker.
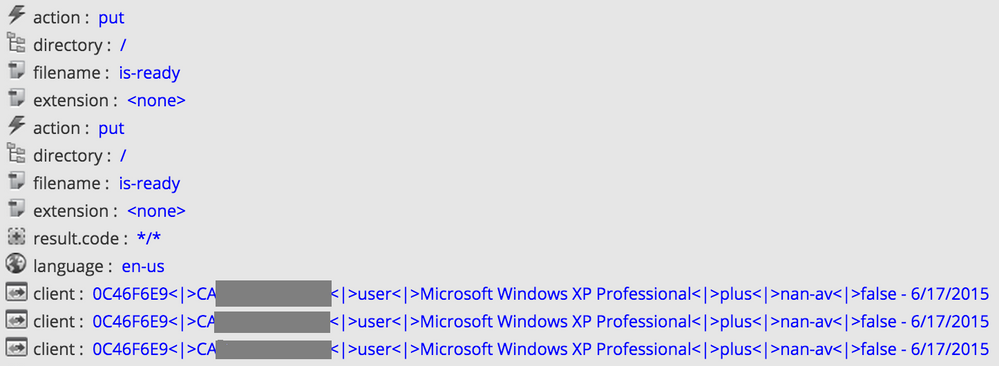
Once a host is infected, it sends an HTTP POST request to the C2 server as shown in the screenshot below:
There are some interesting artifacts in the session above. XtremeRAT embeds information about the infected host in its UA string. The information contains the hostname, the username, date of infection as well as the version of Windows.
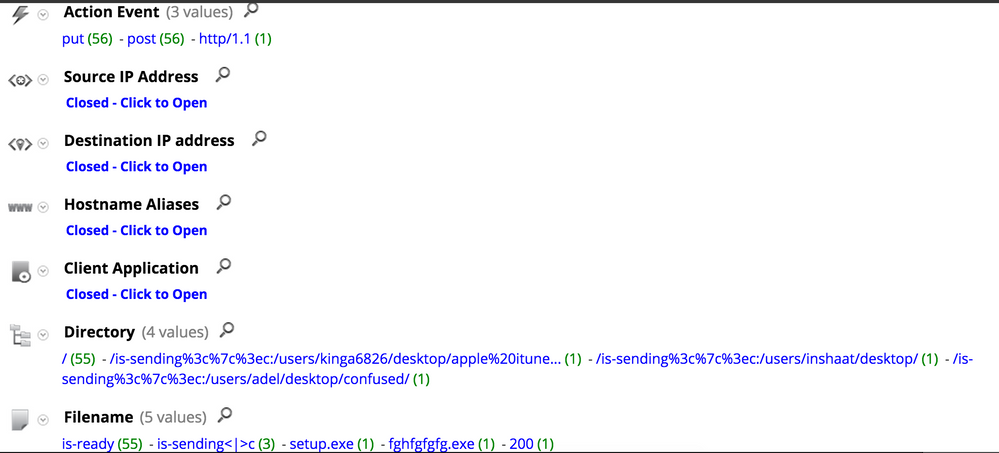
Developing an app rule based on those UA string values is a bit tricky. Unless all the hostnames in your environment follow a certain pattern, you might miss some of the infected machines. Luckily, enough information is available to detect the beaconing activity. This screenshot from RSA Security Analytics shows the network traffic between a group of XtremeRAT infected machines and their C2 servers:
Other filenames that XtremeRAT variants are known to use:
- is-enum-driver
- is-enum-faf
- is-enum-process
Given all the network artifacts mentioned above and assuming the appropriate meta keys are enabled, an analyst can develop an app rule on RSA Security Analytics to detect the malicious traffic. The following query can be used:
action = 'put' && filename begins 'is-' && extension = '<none>'
Scan results for an XtremeRAT sample can be found here.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Using NetWitness to Detect Phishing reCAPTCHA Campaign
- Netwitness Platform Integration with Amazon Elastic Kubernetes Service
- Netwitness Platform Integration with MS Azure Sentinel Incidents
- Netwitness Platform Integration with AWS Application Load Balancer Access logs
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- New HotFix: Addresses Kernel Panic After Upgrading to 12.4.1
- Automation with NetWitness: Core and NetWitness APIs
- HYDRA Brute Force
- DDoS using BotNet Use Case
-
Announcements
64 -
Events
12 -
Features
12 -
Integrations
15 -
Resources
68 -
Tutorials
32 -
Use Cases
31 -
Videos
119