- NetWitness Community
- Blog
- Detection of Squiblydoo COM+ Whitelist Bypassing with ECAT
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
By RSA Incident Responders Brian Baskin and Andrew Nelson
Endpoint protection is a very difficult task for Windows and endpoint agents alike. Microsoft has deployed many solutions over its various Windows versions to battle the effects of local malicious activity. Attackers continually strive to find new ways of injecting code and malware onto vulnerable systems. New exploits uncovered over time provide many avenues of remote code execution through vulnerabilities in web browsers and document viewers, giving adversaries a small window of attack to place malware onto a targeted system. Discovering such weaknesses, and covering them up, has been a continual cat and mouse game between vendors, security researchers, and advanced adversaries.
Part of this battle is due to the fact that Windows contains a great deal of seldom used or legacy functionality. The result is many possible weaknesses cannot be known until they are discovered in the wild. Due to this, many security professionals have begun to utilize whitelisting programs in order to protect against malware executing in their environments. As a result, malware authors have often looked for instances of valid Windows programs to use as conduits for their malicious code. That’s exactly what occurred recently when security researcher Casey Smith (subTee) reviewed years of data related to the Windows Component Object Model (COM+).
“Its not well documented that regsvr32.exe can accept a url for a script.”
-- Casey Smith
A casual statement underlines a small crack deep into the heart of Windows. As Smith discovered, Windows can process COM+ Scriptlets (SCT), small XML files that contain various commands. But what was unique to his discovery is learning that these Scriptlets, processed by regsvr32.exe, can be hosted on Internet-based sites. While registering an object into Windows requires administrative privileges, Smith learned that unregistering an object using a scriptlet can be performed by limited user accounts, even if that object doesn’t exist. While not granting any escalated privileges, the method by which this exploit runs can bypass traditional whitelists. All operations occur with standard Windows components and leave behind no trace of their execution. Smith came public and announced his findings under the code name "squiblydoo".
In keeping up with security threats, RSA’s Incident Response team immediately went to testing and evaluating the exploit. Using the proof of concept written by Smith, Windows XP, 7, and 10 were all vulnerable to the same code, even when run from a limited user account. Analysis performed in a custom sandbox showed no registry artifacts by the execution. Since Windows treats an HTTP address load as an Internet access, it uses standard Internet Explorer libraries to retrieve the file, and creates a connection with a default User-Agent. In modern versions of Windows, this is the User-Agent of Internet Explorer’s compatibility view (IE7). This also leaves behind a single IE Cached file for the downloaded script that is executed by regsvc32.exe. However, as this execution can also use HTTPS, the SSL connection can prevent the download from seen by an IDS, with the only artifact being the cached file.
Endpoint security is the critical piece in detecting this attack as it occurs. RSA’s ECAT has the unique ability to monitor execution paths on every endpoint, collecting command line arguments and tracking file system artifacts. ECAT also holds a very unique strength over the market by empowering security teams with an open and accessible backend, thus allowing for quick queries to be written on-the-fly to hunt for novel attack methods such as this.
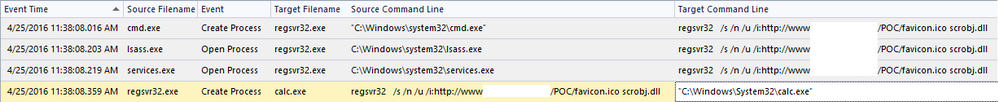
In running the malicious command on an ECAT-monitored endpoint, ECAT’s process event tracking immediately recorded the command being executed and its follow on activity. While this test case was performed directly from cmd.exe, the same artifacts would be observable from other parent processes such as commonly exploited client software like AcroRd32.exe (Adobe Acrobat) or IExplore.exe (MS Internet Explorer).
Using ECAT’s endpoint tracking feature, attempts to spawn this COM+ attack are readily noticeable.
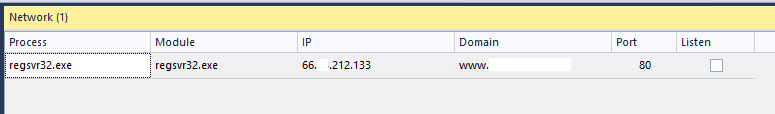
However, the tell-tale sign of this activity is recorded in the network connections from regsvr32.exe. This application should typically have no access to the Internet and any detection of this behavior should be immediately investigated.
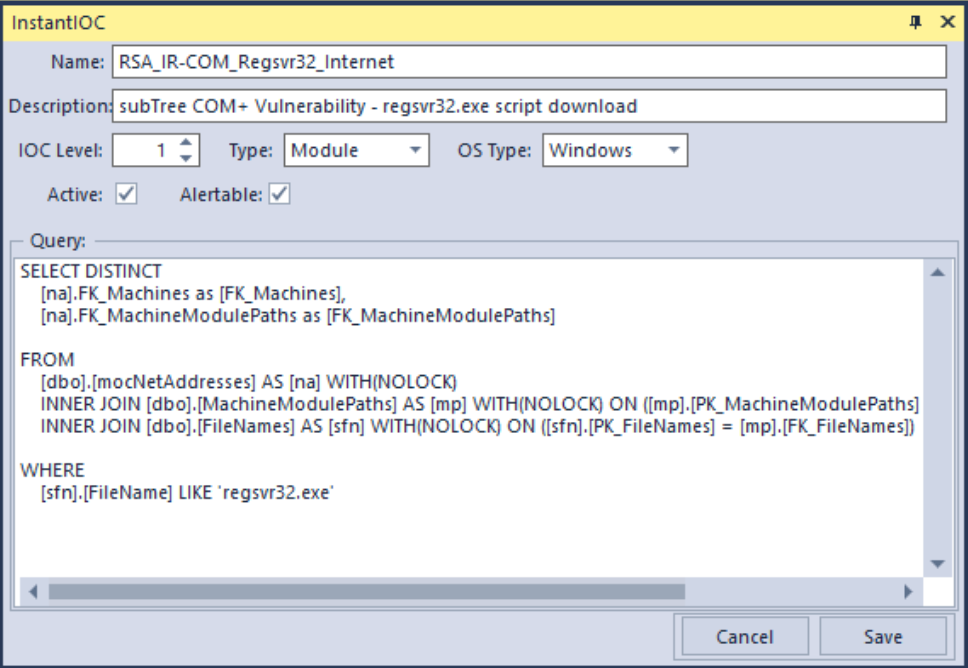
With this in mind, a simple SQL query against the ECAT database, seen as a custom Instant IOC (IIOC), can give rapid results as to any system exhibiting the behavior, assigning that process an IIOC score of 1024 (blacklist).
Within ECAT simply create a new Instant IOC, shown below, and monitor any alerts that are created:
| Instant IOC Query |
|---|
SELECT DISTINCT [na].FK_Machines as
FROM INNER JOIN INNER JOIN
WHERE [sfn].[FileName] LIKE 'regsvr32.exe' |
In addition to its unique endpoint tracking feature, RSA ECAT also has integrated support for YARA rules. This allows for quick blacklisting of known bad files based upon custom written signatures. While attacks using this method leave no trace in the registry they do leave a single copy of the downloaded script within the Internet Explorer cache. By integrating the following YARA rule, ECAT can detect as soon as this script is written to the hard drive and immediately alert security teams of its existence:
| Malicious SCT Script YARA rule |
|---|
rule RSA_IR_Windows_COM_bypass_script { meta: author="RSA IR" Date="22 Apr 2016" comment1="Detects potential scripts used by COM+ Whitelist Bypass" comment2="More information on bypass located at: http://subt0x10.blogspot.com/2016/04/bypass-application-whitelisting-script.html"
strings: $s1 = "<scriptlet>" nocase $s2 = "<registration" nocase $s3 = "classid=" nocase $s4 = "[CDATA[" nocase $s5 = "</script>" nocase $s6 = "</registration>" nocase $s7 = "</scriptlet>" nocase
condition: all of ($s*) } |
While this discovery is an issue that will undoubtedly be mitigated by a Windows Update in the future, the vast number of potentially unpatched systems combined with an open window of easy attack make for period in which this vulnerability could be used successfully. Until this behavior is patched, security teams can only rely upon endpoint agents that can detect its subtle method of execution. As an enterprise level hunting solution, RSA ECAT empowers security teams to detect threats such as Casey Smith’s whitelist bypass as well as modern threats used by advanced adversaries to keep organizations secure.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Using NetWitness to Detect Phishing reCAPTCHA Campaign
- Netwitness Platform Integration with Amazon Elastic Kubernetes Service
- Netwitness Platform Integration with MS Azure Sentinel Incidents
- Netwitness Platform Integration with AWS Application Load Balancer Access logs
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- New HotFix: Addresses Kernel Panic After Upgrading to 12.4.1
- Automation with NetWitness: Core and NetWitness APIs
- HYDRA Brute Force
- DDoS using BotNet Use Case
-
Announcements
64 -
Events
12 -
Features
12 -
Integrations
15 -
Resources
68 -
Tutorials
32 -
Use Cases
31 -
Videos
119