- NetWitness Community
- Blog
- Finding odd DNS TXT records in Security Analytics
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
This week security researchers at Palo Alto Networks revealed a new targeted attack by the APT group Wekby against a US-based organization. Unit42 named the malware used by the group as pisloader based on its metadata. Most notably pisloader uses DNS requests to communicate with its command and control server. In this blog post we will discuss how to use RSA Security Analytics reports to help an analyst in finding odd DNS requests.
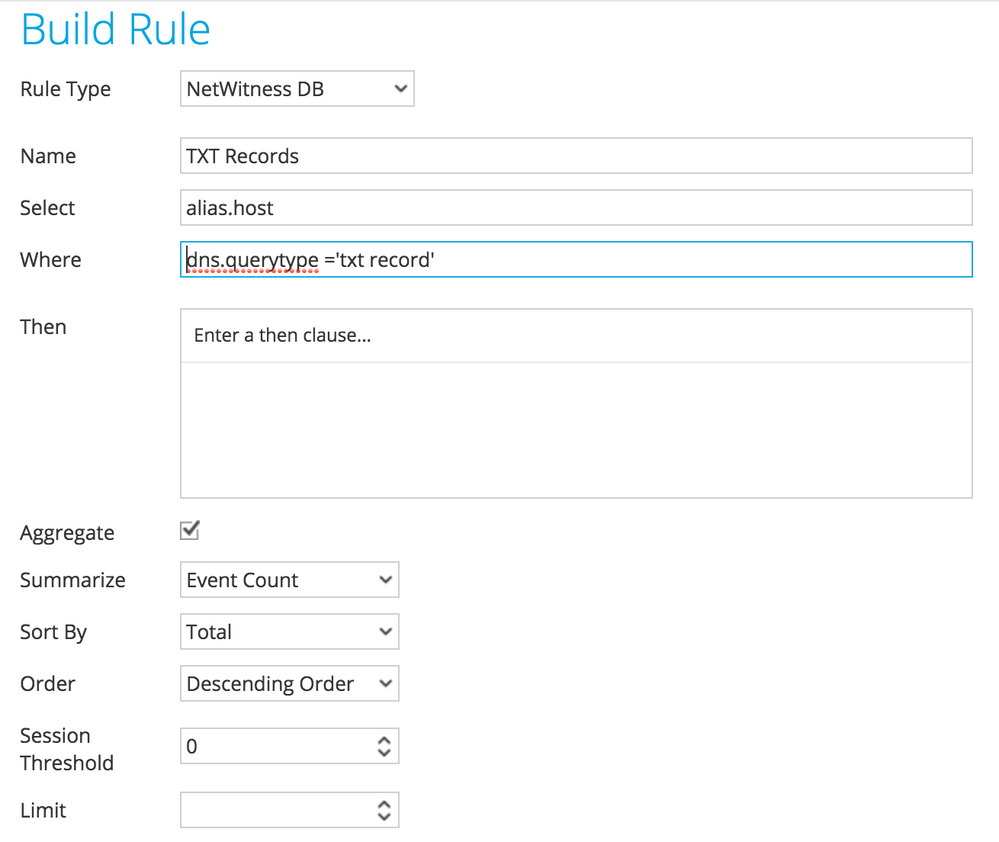
First, you need to start by creating a rule in SA. In this use case, we are interested in DNS requests for a TXT record:
The rule builder can be used to filter the result set or add more meta values to it if necessary. Next, you need to add the rule to a report and schedule it to run on a regular basis.
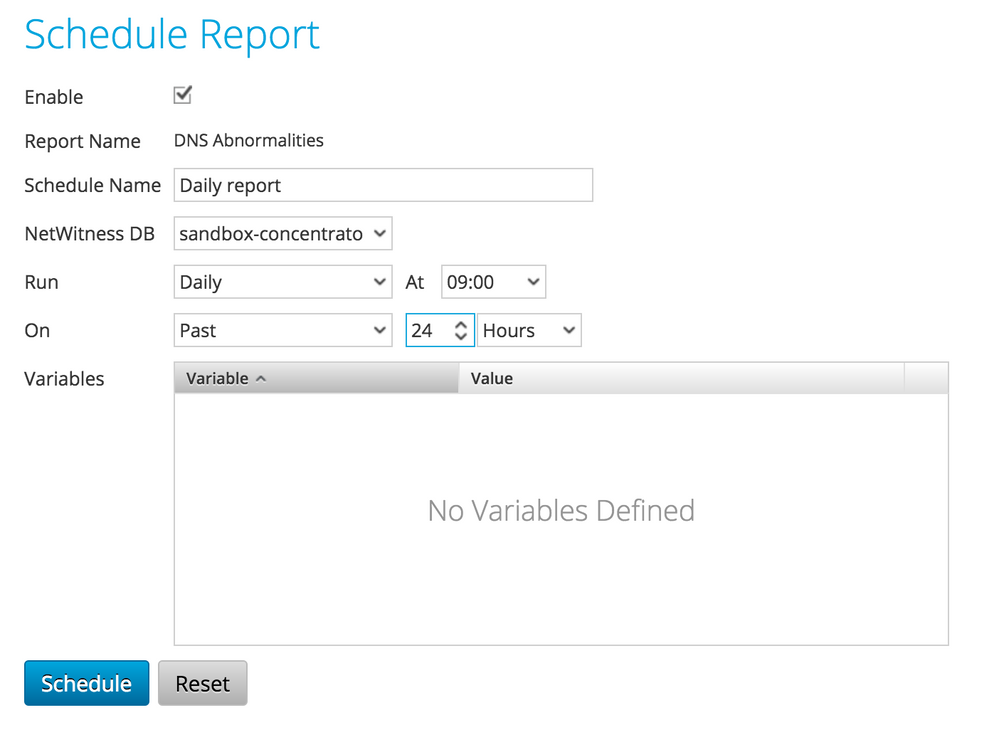
I chose to schedule a daily report that looks for DNS requests for a TXT record in the past 24 hours:
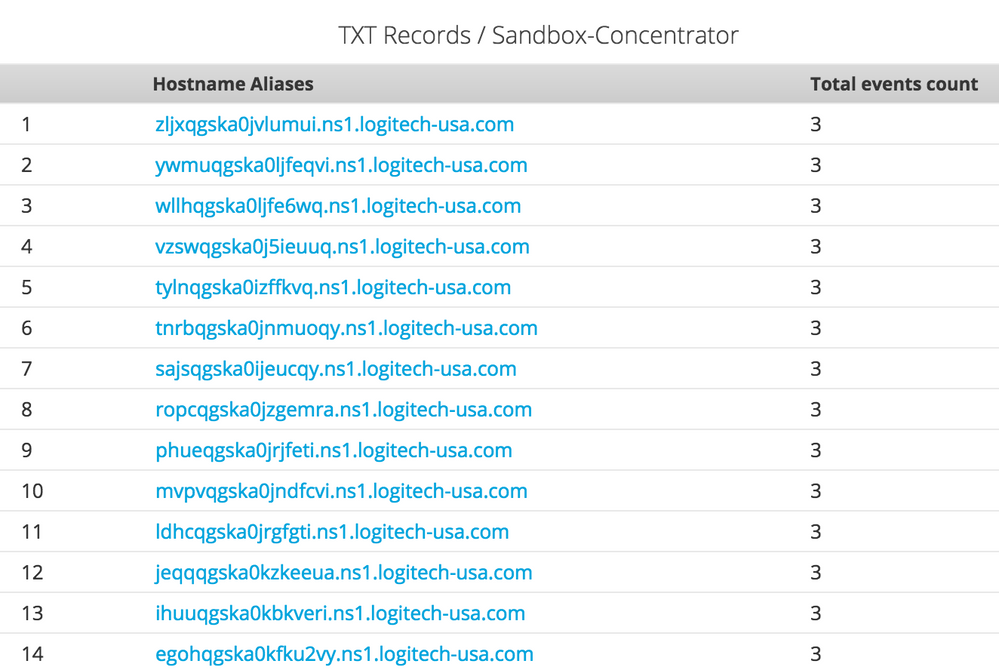
When RSA FirstWatch ran pisloader malware samples in its sandbox, the binaries started to beacon to their C2 servers. This is how the DNS requests look in the newly created report:
An analyst can go through the result set of the newly created report to rule out any false positives and dig deeper into more suspicious ones.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Netwitness Platform Integration with Amazon Elastic Kubernetes Service
- Netwitness Platform Integration with MS Azure Sentinel Incidents
- Netwitness Platform Integration with AWS Application Load Balancer Access logs
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- New HotFix: Addresses Kernel Panic After Upgrading to 12.4.1
- Automation with NetWitness: Core and NetWitness APIs
- HYDRA Brute Force
- DDoS using BotNet Use Case
- A Closer Look at Advanced EPL (ESA) Through a Rule and its Components
-
Announcements
64 -
Events
12 -
Features
12 -
Integrations
15 -
Resources
68 -
Tutorials
32 -
Use Cases
31 -
Videos
119