- NetWitness Community
- Blog
- How to Forward Syslog from a Remote Log Collector to another destination
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
(I've only managed to get this method working with UDP)
Customers often want to forward syslog traffic that is being sent to Netwitness for Logs to another syslog destination, so that the syslog traffic is processed by both Netwitness and the other syslog receiver.
There are many ways that this can be achieved (such as Configure Syslog Forwarding to Destination - RSA Security Analytics Documentation ) but here is another method.
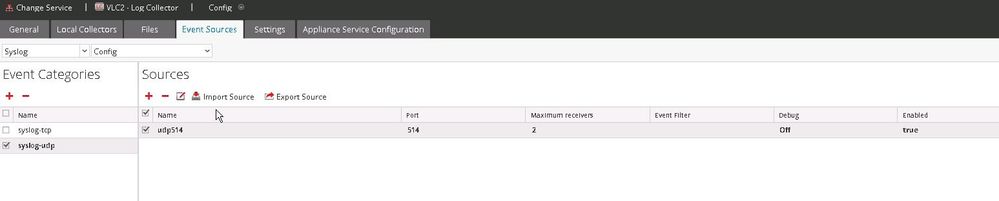
1) On the Remote Log Collector go to Event Sources -> Syslog and Config.
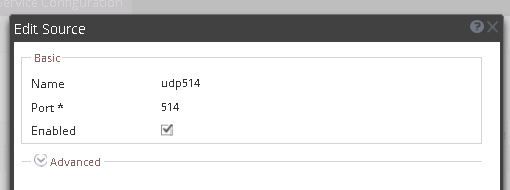
2) Disable the current syslog sources. These will typically be upd514 and tcp514. To disable edit each source and untick the Enabled box.
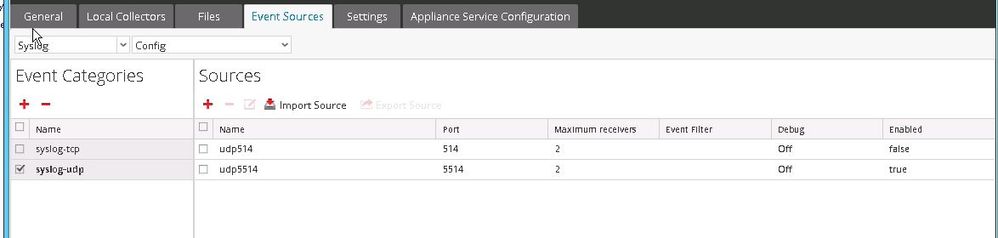
3) Set up new TCP and UDP listeners on a different port. In this case we use UDP 5514 and TCP 5514.
4) Stop and start the Syslog Collection Method
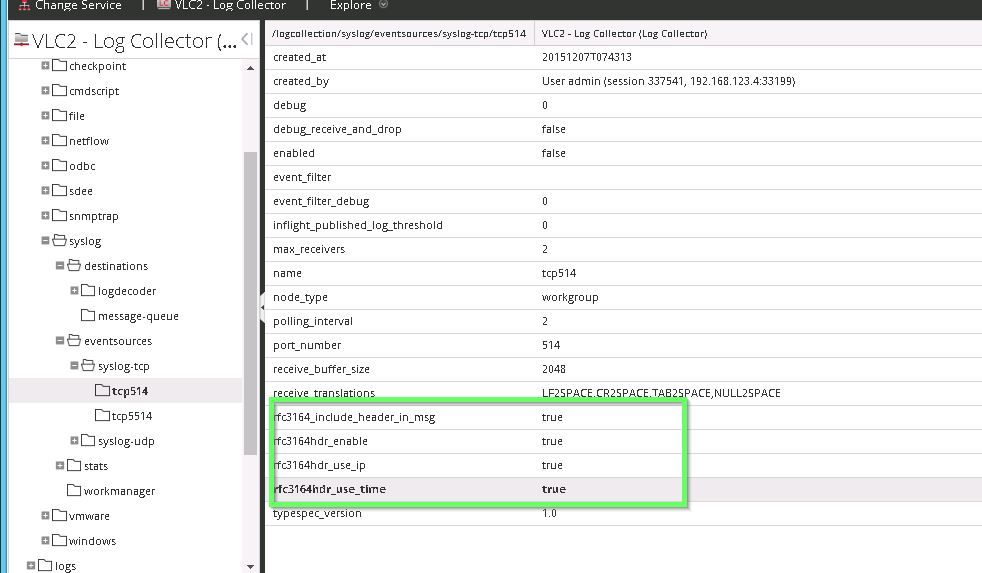
Make sure that in explore view under logcollection/syslog/eventsources/syslog-tcp and syslog udp that you set the following headers to true. This will ensure that when security analytics processes the message the original IP is seen.
5) Confirm with netstat -na |grep -i 514 that the system is only listening on your new ports 5514
netstat -na |grep -i 514
tcp 0 0 0.0.0.0:5514 0.0.0.0:* LISTEN
tcp 0 0 192.168.123.242:41566 192.168.123.27:514 ESTABLISHED
tcp 1 0 192.168.123.242:51282 192.168.123.27:514 CLOSE_WAIT
tcp 0 0 :::5514 :::* LISTEN
udp 0 0 0.0.0.0:5514 0.0.0.0:*
udp 0 0 127.0.0.1:50514 0.0.0.0:*
udp 0 0 :::5514 :::*
6) Edit the file /etc/rsyslog.conf
Uncomment the following lines:
# Provides UDP syslog reception
$ModLoad imudp
$UDPServerRun 514
# Provides TCP syslog reception
$ModLoad imtcp
$InputTCPServerRun 514
And add the line
$PreserveFQDN on
7) At the end of the file add the following lines:
*.* @@192.168.123.27:514
OR
*.* @192.168.123.27:514
This will forward all TCP traffic to 192.168.123.27 port 514 or all UDP traffic to 192.168.123.27
Also add one of the following lines
*.* @@localhost:5514
OR
*.* @localhost:514
This will forward all syslog traffic to our log collector for processing. The difference is that if @ is used the traffic gets forwarded as UDP syslog 514. If @@ is used the traffic gets forwarded as TCP. Forwarding as TCP is better as large syslog messages can be transferred and TCP has more robust packet delivery than UDP.
7) Restart the rsyslog service with service rsyslog restart
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Using NetWitness to Detect Phishing reCAPTCHA Campaign
- Netwitness Platform Integration with Amazon Elastic Kubernetes Service
- Netwitness Platform Integration with MS Azure Sentinel Incidents
- Netwitness Platform Integration with AWS Application Load Balancer Access logs
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- New HotFix: Addresses Kernel Panic After Upgrading to 12.4.1
- Automation with NetWitness: Core and NetWitness APIs
- HYDRA Brute Force
- DDoS using BotNet Use Case
-
Announcements
64 -
Events
12 -
Features
12 -
Integrations
15 -
Resources
68 -
Tutorials
32 -
Use Cases
31 -
Videos
119