- NetWitness Community
- Blog
- Integrating Rapid 7 Nexpose into Netwitness Logs
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
The official Rapid 7 Nexpose Guide seemed unfortunately to be short of a few details (Rapid 7 NeXpose Event Source Configuration Guide ) so I described how I integrated the Windows version of Rapid 7 Nexpose into Security Analytics.
I was using Nexpose 5.17.1 on a Windows 2008 Server.
The screenshots have been taken from Security Analytics 10.6.1
This document assumes that the reader is familiar with installing the SFTP Agent and setting it up.
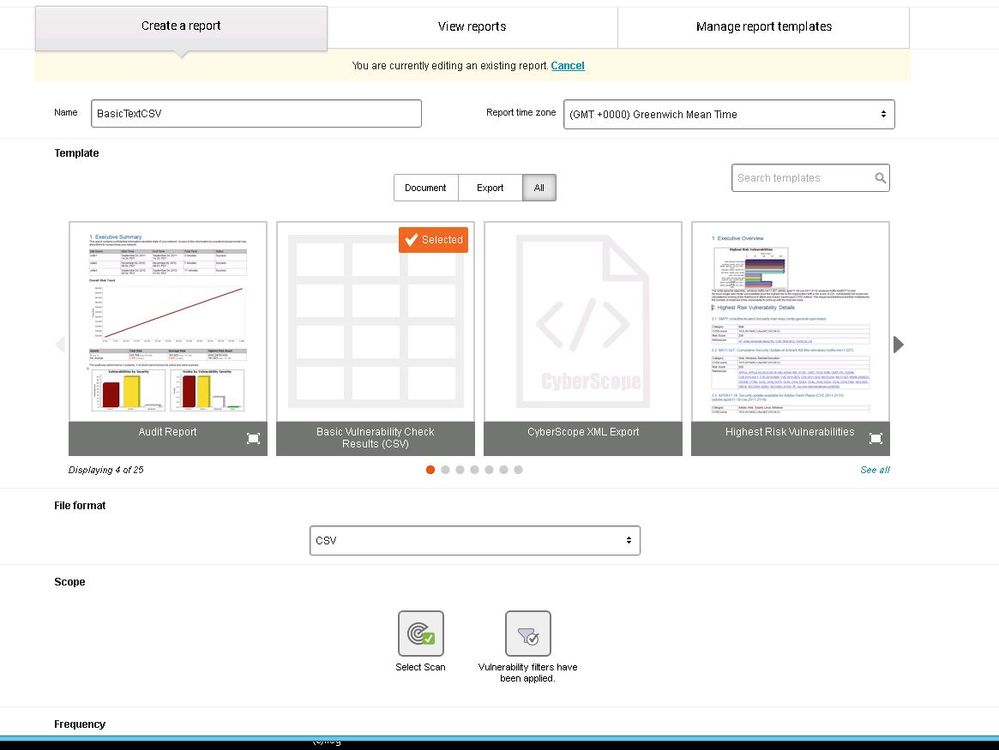
- On your Nexpose Server ,create a CSV Report in Nexpose using the "Basic Vulnerability Check Results (CSV) Template)
- This will output a CSV Report of the scan. However, the problem is that the file will be gz compressed and this is not compatible when sending it to the Log Collector. As a result we will uncompress it using 7-zip. Install 7-Zip on your server (http://www.7-zip.org/download.html )
- Still on your Nexpose Server create a directory called NexposeScripts and populate it with the contents of NexposeScripts.zip that is attached to this document. Run a scheduled task in Windows to run the batch file Nexpose.bat every 5 minutes.
- On the Nexpose Server install the RSA SFTP Agent and use the attached sftagent.conf to process the nexpose log messages.
- On the LogCollector copy the file rapid7.xml to /etc/netwitness/ng/logcollection/content/collection/file and restart the logcollector service.
- On the log decoder make a directory called /etc/netwitness/ng/envision/etc/devices/rapid7 and copy the files /v20_rapid7msg.xml and rapid7.ini into this directory.
- Restart the logdcoder
The parser makes use of the vuln_ref reference key so make sure that in your table-map-custom.xml file you have the line
<mapping envisionName="vuln_ref" nwName="vuln.ref" flags="None" format="Text"/>
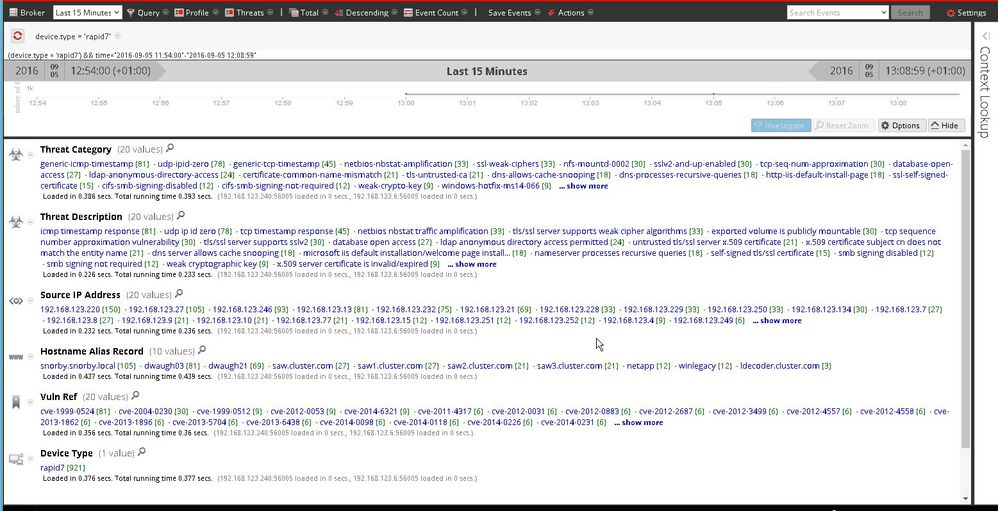
If everything is correctly setup then you should see a new rapid7 device type, with Threat Category, Threat Description and also the Vuln Ref key populated with CVE numbers.
Note by default, the Script Nexpose.bat will leave the reports reports.csv.gz in the original directory. If you want them to be deleted after processing then add the line highlighted in bold below to the c:\nexposescripts\nexpose.bat
cscript nexpose-audits.vbs
cscript nexpose-authevents.vbs
cscript nexpose-nscevents.vbs
cd "C:\Program Files\rapid7\nexpose\nsc\htroot\reports"
for /R %%f in (report.csv.gz) do "c:\program files\7-Zip\7z.exe" e -y "%%f"
for /R %%f in (report.csv.gz) do del /q "%%f"
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Using NetWitness to Detect Phishing reCAPTCHA Campaign
- Netwitness Platform Integration with Amazon Elastic Kubernetes Service
- Netwitness Platform Integration with MS Azure Sentinel Incidents
- Netwitness Platform Integration with AWS Application Load Balancer Access logs
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- New HotFix: Addresses Kernel Panic After Upgrading to 12.4.1
- Automation with NetWitness: Core and NetWitness APIs
- HYDRA Brute Force
- DDoS using BotNet Use Case
-
Announcements
64 -
Events
12 -
Features
12 -
Integrations
15 -
Resources
68 -
Tutorials
32 -
Use Cases
31 -
Videos
119