- NetWitness Community
- Blog
- Kargen Botnet Teams With Chameleon Encoding
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
I previously wrote about Kargen here. It's main characteristics are a set beacon filename length put to a /b/req/ or /b//opt/ directory on a compromised webserver.
I previously wrote about Chameleon encoding here, which primary characteristics were domains that were actually hexadecimal color codes, registered, I think, to frustrate researchers looking to search the internet for these domain names involved in an incident. Instead of information about the incident, results from web searches only include any embedded matching hex color code in thousands of web pages crawled by the search engines.
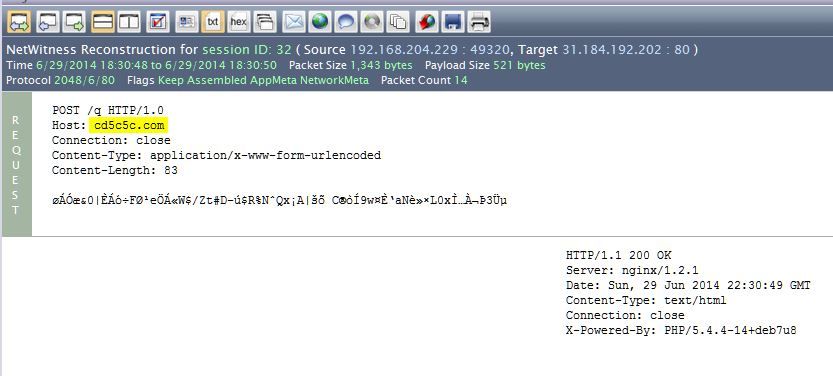
In the sample below, we can see similar Kargen activity, coupled with beaconing to a Chameleon encoded domain. The Kargen beacon has changed length strings a bit, and the Chameleon Encoding put commands are now url-encoded beacons rather than search engine strings. Here is a screenshot of that beacon.
This PCAP, attached below, is available for everyone to evaluate for new rules to detect this threat. It came from MalwareTrafficAnalysis here, dated 6/29. The infection is a result of the Magnitude Exploit Kit, but the post-infection network traffic should be familiar as Kargen. This threat is new, but it builds on older techniques and methods of botnet masters that we have previously discussed in this space. As always, the domains here will be added to the Live C2 domains list.
Please discuss among yourselves how best to detect this new combined variant.
Good Luck and Happy Hunting!
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Using NetWitness to Detect Phishing reCAPTCHA Campaign
- Netwitness Platform Integration with Amazon Elastic Kubernetes Service
- Netwitness Platform Integration with MS Azure Sentinel Incidents
- Netwitness Platform Integration with AWS Application Load Balancer Access logs
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- New HotFix: Addresses Kernel Panic After Upgrading to 12.4.1
- Automation with NetWitness: Core and NetWitness APIs
- HYDRA Brute Force
- DDoS using BotNet Use Case
-
Announcements
64 -
Events
12 -
Features
12 -
Integrations
15 -
Resources
68 -
Tutorials
32 -
Use Cases
31 -
Videos
119