- NetWitness Community
- Blog
- Monitoring Netwitness with Zabbix
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
This post is completely unsupported by RSA Support and indeed RSA, but it might be interesting if you want to try it.
In Netwitness 10.X the current weakness in the topology is that the SA Server is a single point of failure and it monitors the other components in your environment. If the monitoring on your SA Server has a problem would you actually be aware of it?
I've posted in the past about monitoring your Netwitness Infrastructure with Nagios, but what about Zabbix? This is a more modern monitoring system and I gave it a go on my Netwitness environment. More information on Zabbix can be found at Zabbix :: The Enterprise-Class Open Source Network Monitoring Solution
Monitoring involves installing the Zabbix Agent onto each server. This can be done by copying the Centos 6 rpm into
/var/netwitness/srv/www/rsa/updates/10.6.3 and then running the following.
cd /var/netwitness/srv/www/rsa/updates/10.6.3
createrepo .
Instructions for obtaining the Zabbix agent for Centos 6 can be found at: How to Install Zabbix Agent on CentOS/RHEL 7/6/5
In the file
/etc/puppet/modules/base/manifest/init.pp add the following lines:
package { 'zabbix-agent' :
ensure => installed,
}# Configure Zabbix Agent for PreShared Key Encrypted Connections
file {'zabbix_agentd.conf' :
path => "/etc/zabbix/zabbix_agentd.conf",
mode => 0644,
ensure => present,
owner => "root",
group => "root",
source => "puppet:///modules/base/zabbix_agentd.conf",
notify => Service['zabbix-agent'],
}
file {'zabbix_agentd.psk' :
path => "/etc/zabbix/zabbix_agentd.psk",
mode => 0644,
ensure => present,
owner => "root",
group => "root",
source => "puppet:///modules/base/zabbix_agentd.psk",
notify => Service['zabbix-agent'],
}
firewall {'1 Allow Zabbix Agent':
port => [10050],
proto => tcp,
action => accept,
source => '192.168.123.177',
}
This will copy a standard agent configuration file and pre-shared key to encrypt the Zabbix Server and Zabbix Agent communication. It will also open a firewall port to allow communication from the Zabbix Server in this case 192.168.123.177 to each Security Analytics appliance on tcp port 10050
The following files should be copied to /etc/puppet/modules/base/files
zabbix_agentd.conf
zabbix_agentd.psk
The advantages of monitoring are:
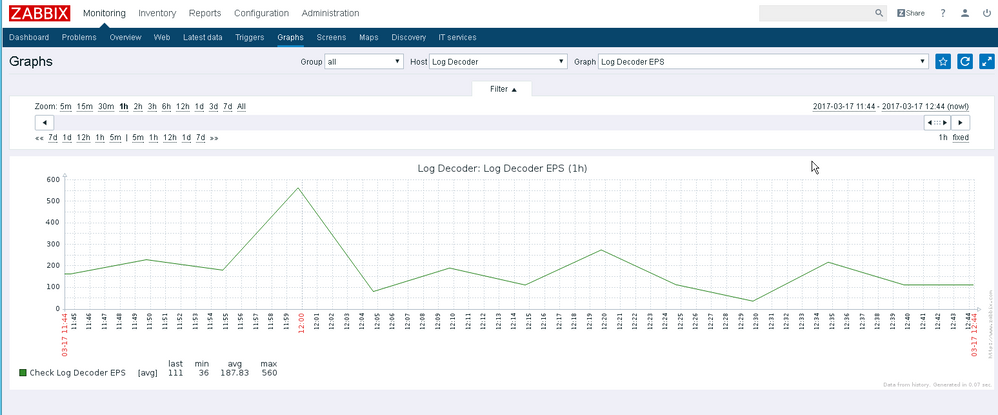
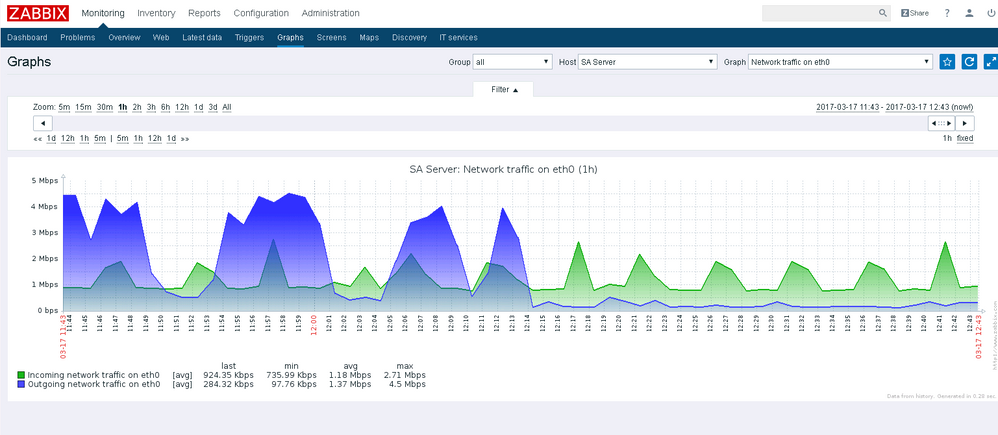
- Ability to make nice graphs
- Ability to have a Map of your infrastructure to see any problems easily.
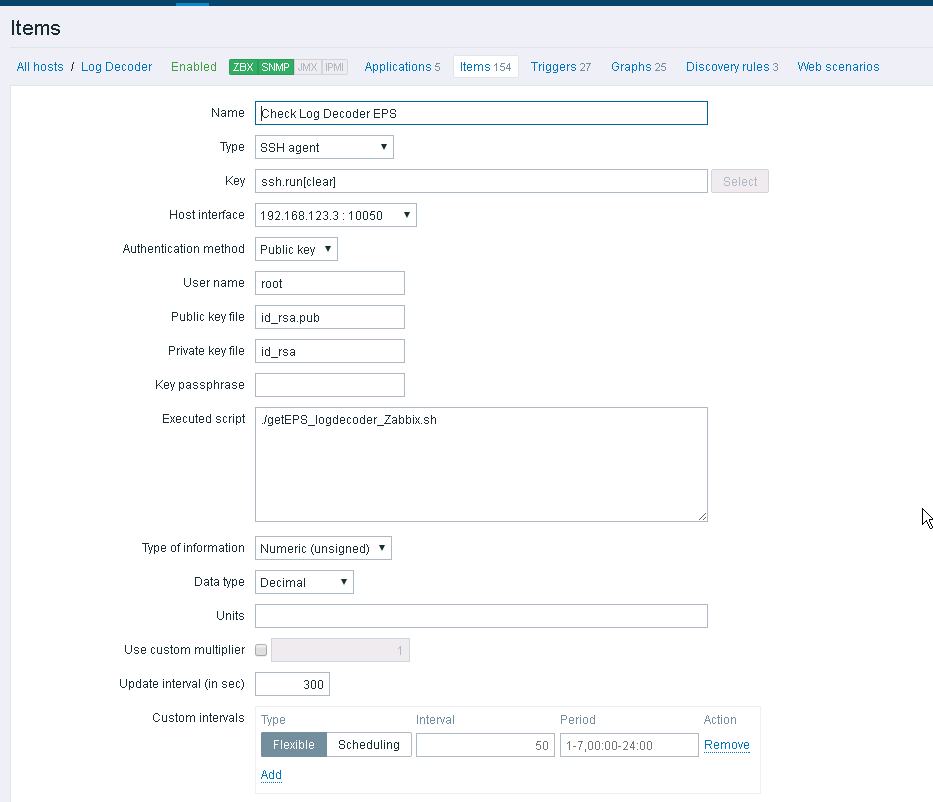
I've also copied a few Zabbix Checks that can be run by using the check type "SSH Agent". Note in this example I used the root account, but best practise would be to create a specific Zabbix account on each system. Again this could be done using puppet.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Using NetWitness to Detect Phishing reCAPTCHA Campaign
- Netwitness Platform Integration with Amazon Elastic Kubernetes Service
- Netwitness Platform Integration with MS Azure Sentinel Incidents
- Netwitness Platform Integration with AWS Application Load Balancer Access logs
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- New HotFix: Addresses Kernel Panic After Upgrading to 12.4.1
- Automation with NetWitness: Core and NetWitness APIs
- HYDRA Brute Force
- DDoS using BotNet Use Case
-
Announcements
64 -
Events
12 -
Features
12 -
Integrations
15 -
Resources
68 -
Tutorials
32 -
Use Cases
31 -
Videos
119