- NetWitness Community
- Blog
- New Kazy Variant: Kazy Forces
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
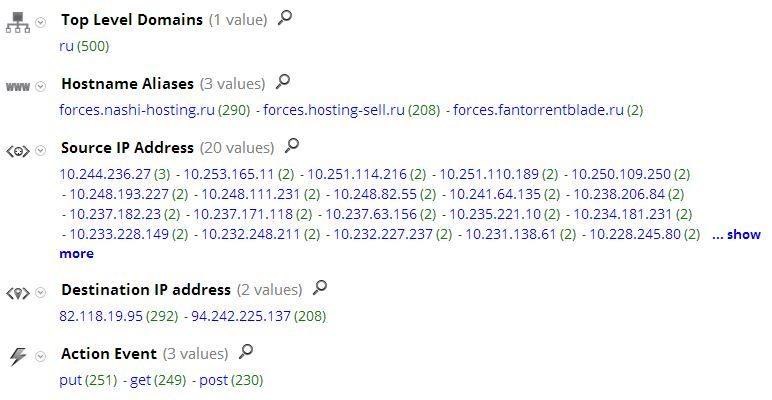
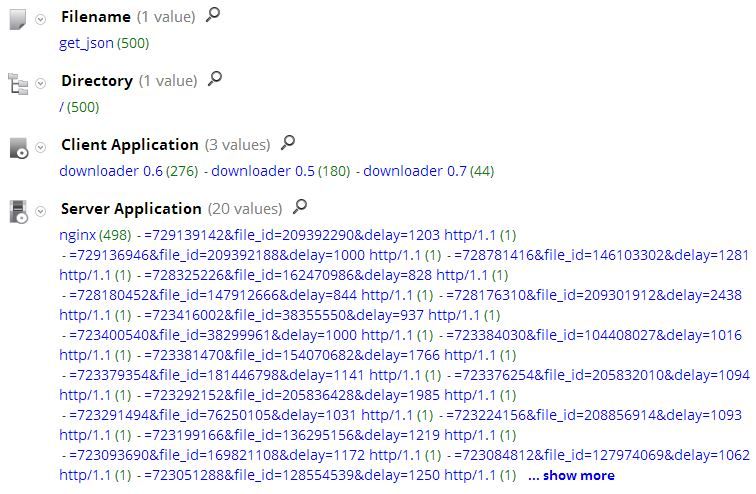
RSA FirstWatch has detected a new variant of Kazy that uses a wrapped JSON file for its command and control. We are dubbing this variant "Kazy Forces" since its known C2 domains are Russian Hosted servers that begin "Forces." VirusTotal has a summary of the infecting malware located here. Here is what this variant looks like in RSA's Security Analytics.
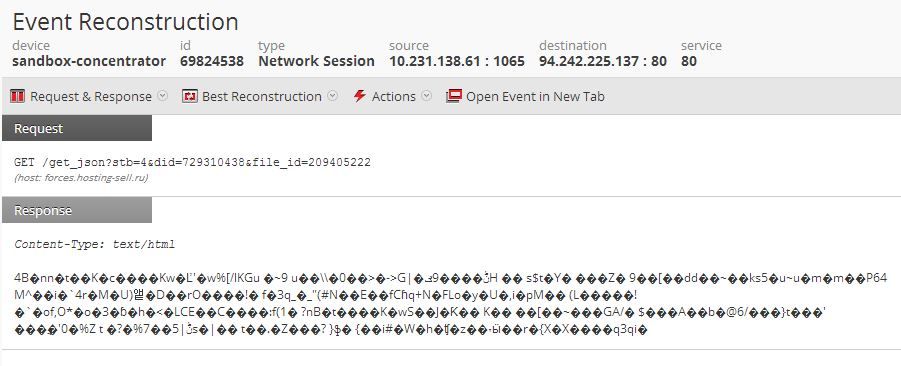
Here is what the session looks like:
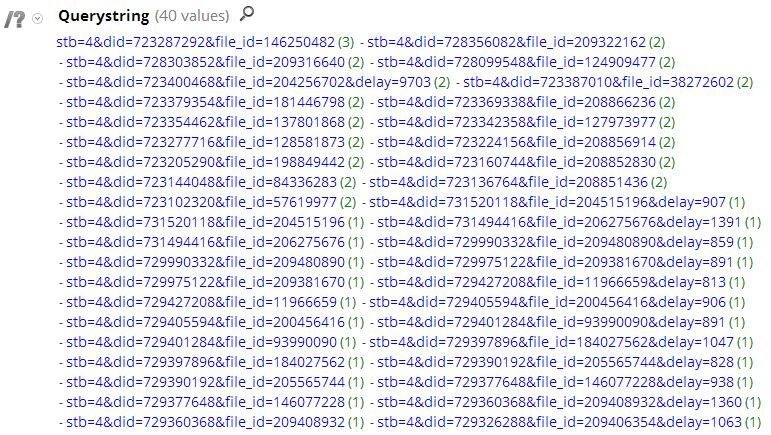
A simple application rule can be implemented to detect this variant on your network, regardless of any changing domain names. That rule is:
filename='get_json' && query exists
The user-agent strings presented above are also strong indicators of compromise. Each of the Command and Control domains have been added to the RSA Live Feeds, so customers will be capable of detecting these malicious hosts. A PCAP sample of this malware in action is attached for review and testing purposes.
Good Luck and Happy Hunting!
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Using NetWitness to Detect Phishing reCAPTCHA Campaign
- Netwitness Platform Integration with Amazon Elastic Kubernetes Service
- Netwitness Platform Integration with MS Azure Sentinel Incidents
- Netwitness Platform Integration with AWS Application Load Balancer Access logs
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- New HotFix: Addresses Kernel Panic After Upgrading to 12.4.1
- Automation with NetWitness: Core and NetWitness APIs
- HYDRA Brute Force
- DDoS using BotNet Use Case
-
Announcements
64 -
Events
12 -
Features
12 -
Integrations
15 -
Resources
68 -
Tutorials
32 -
Use Cases
31 -
Videos
119