- NetWitness Community
- Blog
- The Kargen Zbot and How to Detect It
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Bookmark
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
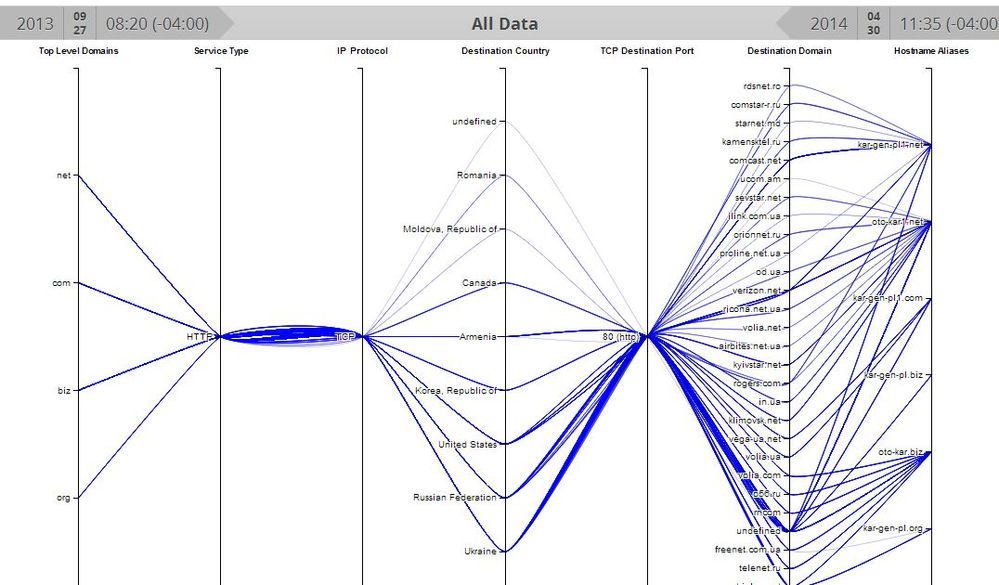
The Kargen Zbot variant has been around for a few months, but it has recently added new Command and Control domains to its traditional stable of high-availability hosts. A host infected with the Kargen Zbot has been observed to engage in Search Engine abuse, bitcoin mining, pay-per-click advertising abuse, and pay-per-install software referral abuse. But what makes this variant unique is its tell-tale beaconing pattern as shown below.
First, Security Analytics' new Coordinates Visualization Tool in Investigator makes it easy to see how these Command and Control domains are spread among several providers to provide maximum uptime. They don't use Dynamic DNS, nor fast flux- just standard round-robin name resolution. (click image to see larger version)
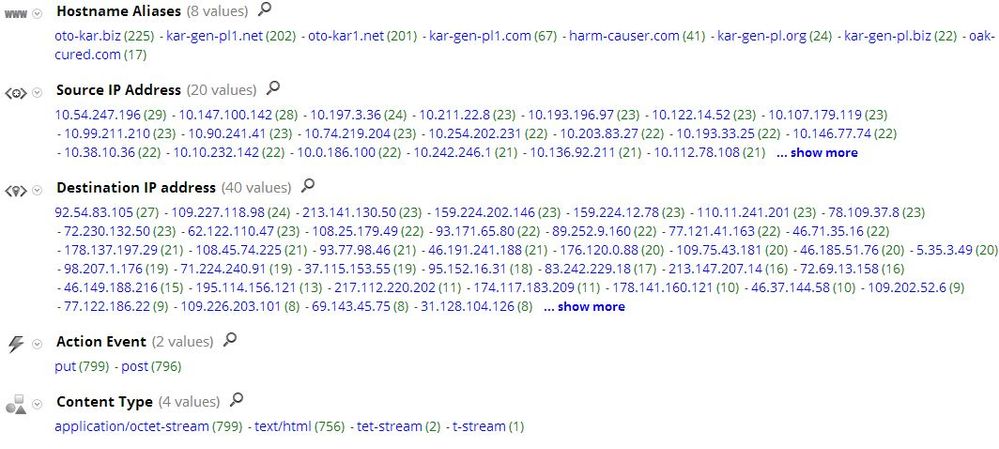
Next, you can see the hostnames involved, along with the multiple destination IP addresses used by the botnet to maintain it's uptime.
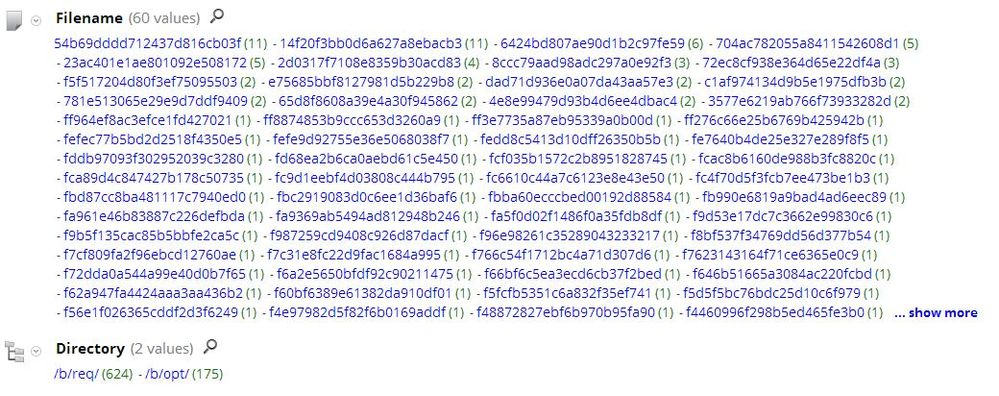
Now you will also see the unique beaconing pattern. 24character filenames are posted to two distinct directories.
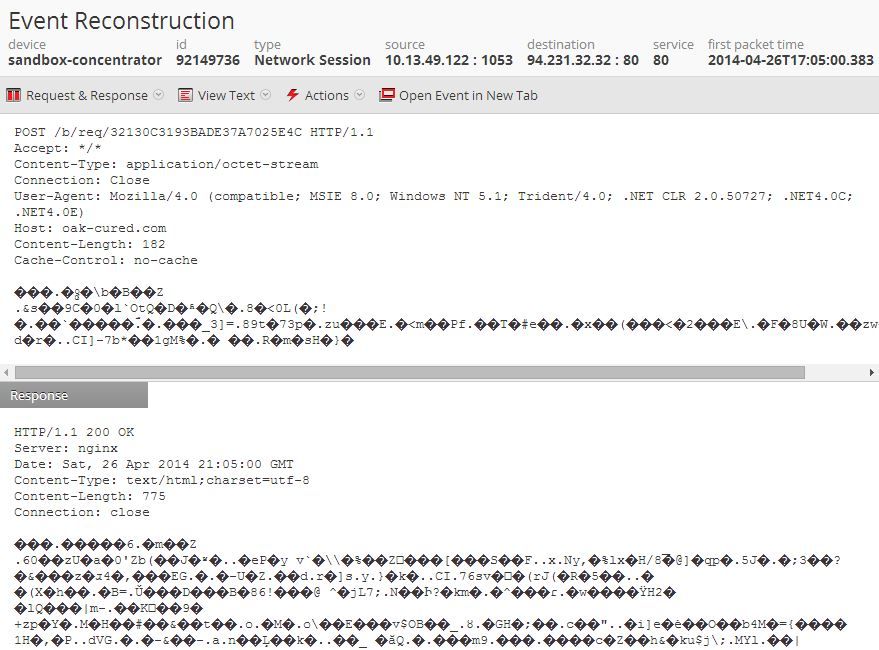
And finally, the beacon session is encoded and looks like this:
The simple rule to detect this beaconing pattern is:
action=put && directory='/b/req/', '/b/opt/'
Name the Rule Kargen Zbot Variant Beacon and alert it into risk.warning or your preferred alert key.
Finally, each of the domains listed above have been added to the FirstWatch C2 Domain feed so customers will better detect this threat.
Good Luck and Happy Hunting!
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Using NetWitness to Detect Phishing reCAPTCHA Campaign
- Netwitness Platform Integration with Amazon Elastic Kubernetes Service
- Netwitness Platform Integration with MS Azure Sentinel Incidents
- Netwitness Platform Integration with AWS Application Load Balancer Access logs
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- The Sky Is Crying: The Wake of the 19 JUL 2024 CrowdStrike Content Update for Microsoft Windows and ...
- New HotFix: Addresses Kernel Panic After Upgrading to 12.4.1
- Automation with NetWitness: Core and NetWitness APIs
- HYDRA Brute Force
- DDoS using BotNet Use Case
-
Announcements
64 -
Events
12 -
Features
12 -
Integrations
15 -
Resources
68 -
Tutorials
32 -
Use Cases
31 -
Videos
119