- NetWitness Community
- Discussions
- Alert based on unique meta key value count
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Alert based on unique meta key value count
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2017-03-16 04:34 PM
Is there a way to alert on the number of unique meta key values associated with a session for a particular meta key (without using ESA or reports)? This is for Netwitness packets 10.6.2.
A simple use case would be:
mass spam alert = emailfrom ends 'ourdomain.com' && uniq-count of emailto > 500
This is simplistic, but we're looking for a way to detect mass outbound smtp messages. I haven't seen a way with app rules to count the number of unique meta values for a particular key and assume we can do this with an advanced esper query, but wanted to see if there was a way to perform this on the packet decoders themselves.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2017-03-16 06:06 PM
Hi Michael,
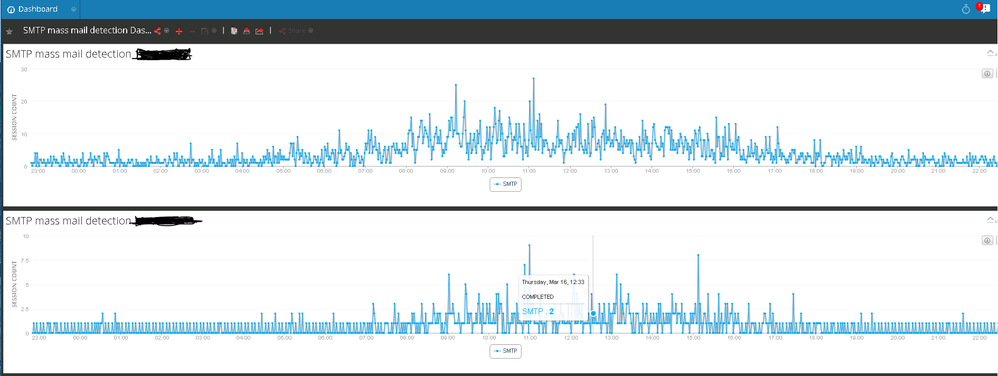
I'm using Reporting Engine for this, we generate dashboards ( charts ) with information about smtp sessions for our mx servers :
But You can use RE to generate alerts too.
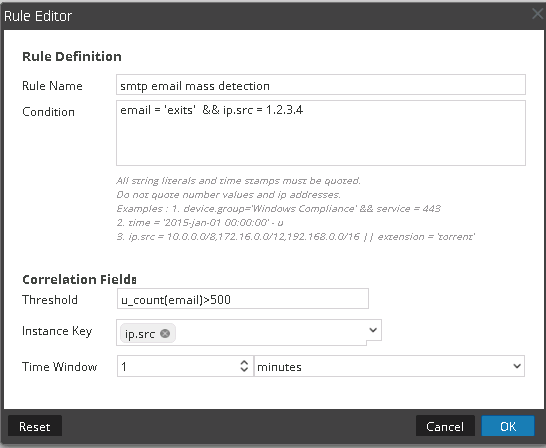
Other option is to use correlation rules on packed decoder, IMO it should work, for example :
But you have to test it.
Maybe other more experienced NW users could tweak this rule ![]()
Regards
Marcin
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2017-03-24 07:49 AM
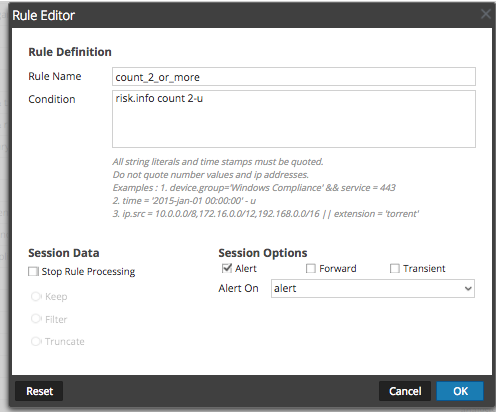
While there isn't a "uniq-count" verb in application rules, there is "count". Please note this only works in creating application rules and is not a verb used during queries in Investigator.
For example, an app rule for counting at least 3 risk.info meta in the same session would be:
risk.info count 3-u
A count of 4 or less HTTP Request headers would be:
http.request exists && http.request count l-4 && service = 80
Therefore, one way your app rule could look would be:
mass spam alert = emailfrom ends 'ourdomain.com' && emailto count 500-u
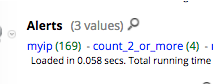
Another quick example from the lab:
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2020-08-12 01:03 PM
Can you do a count in profiles inside of investigate navigate?