- NetWitness Community
- Discussions
- Can you please help me out regarding the ESA rule for those devices which are not sending logs to SI...
-
Options
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Bookmark
- Subscribe
- Mute
- Printer Friendly Page
Can you please help me out regarding the ESA rule for those devices which are not sending logs to SIEM (NW)
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2020-08-30 11:57 PM
Can you please help me out regarding the ESA rule for those devices which are not sending logs to SIEM (NW) as we are already enabled the policies but we required ESA rule logic for triggering the alert, so we will create incident for that.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2020-08-31 09:11 AM
PCL SOC,
I've moved your question to the RSA NetWitness Platform" data-type="space space where it will be seen by the product's support engineers, other customers and partners. Please bookmark this page and use it when you have product-specific questions.
Alternatively, from the RSA Customer Support page, click on Ask A Question on the blue navigation bar and choose Ask A Product Related Question. From there, scroll to RSA NetWitness Platform" data-type="space and click Ask A Question. That way your question will appear in the correct space.
Regards,
Erica
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2020-09-01 11:12 AM
Hi PCL SOC,
Do you want to create a rule if no log traffic is received from a device in a given timeframe? If it is the case, please refer to : Example #5 - EPL #9 in Alerting: Sample Advanced EPL Rules
SELECT * FROM pattern [every a = Event(device_ip IN ('10.0.0.0','10.0.0.1') AND medium = 32) -> (timer:interval (3600 seconds) AND NOT Event(device_ip = a.device_ip AND device_type = a.device_type AND medium = 32))];
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2020-09-01 02:46 PM
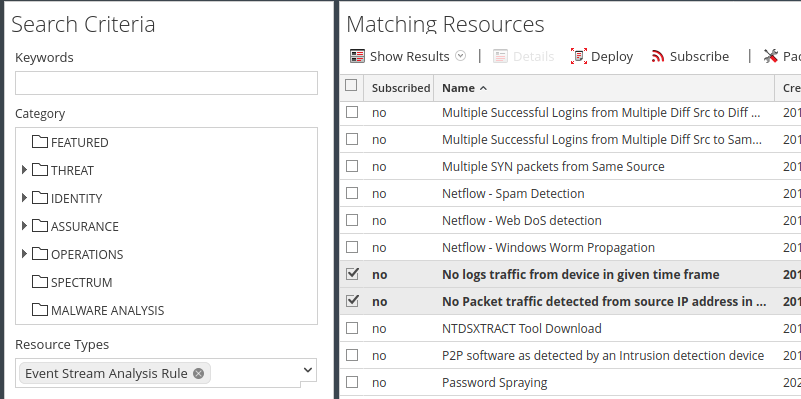
This is also available as OOTB RSA Live ESA rules, one for network traffic and another for log devices:
Mr. Mongo