- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-10-24 02:28 AM
Version of SA 11.1
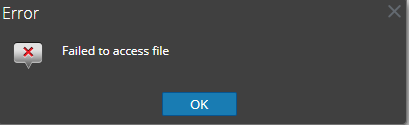
We have problem in creating custom feed using the stored csv file which we have pull from one of our indicators source and store it in SA Head under /var/netwitness/srv/www/rsa/feeds.
Below is the error I see in SA logs
jetty.sh: 2018-10-24 06:13:40,554 [qtp575593575-21225] ERROR com.rsa.smc.sa.core.service.DefaultHttpClientService - http://localhost/feeds/test.csv
jetty.sh: javax.net.ssl.SSLHandshakeException: sun.security.validator.ValidatorException: PKIX path building failed: sun.security.provider.certpath.SunCertPathBuilderException: unable to find valid certification path to requested target
Tried below options as well
- setting permission to the file location and folder as well
- Tried both Authenticated and unauthenticated
- Moving the file to /var/netwitness/srv/www directly as well
- Given the Hostname, IP instead of localhost
We use custom certificate for the SA Console which works fine but the above error indicates something related to certificate
- Labels:
-
RSA NetWitness Endpoint
Accepted Solutions
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-10-24 12:49 PM
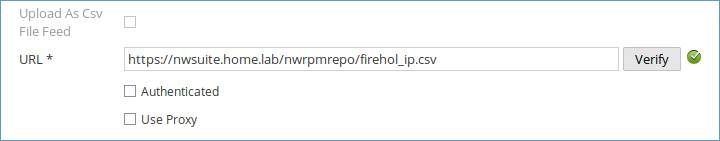
Since you say you're using a custom certificate, and not the self-signed, OOTB "netwitness” certificate, your connection URL will need to use the CN of your custom cert, in addition to the directory Miha Mesojedec mentions:
The CSV in the directory:
The CN of my custom cert:
And putting those together for the connection URL in the feed wizard:
You can also refer to Eric Partington's blog post that describes how to set this up.
HTH
Mr. Mongo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-10-24 03:01 AM
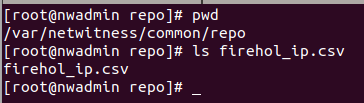
nginx is redirecting everything over https and that to get to the repos it is presenting /nwrpmrepos which is /var/netwitness/common/repo/ . Created a directory called feeds then placed the files there. Keep in mind these directories are browseable.
The CN on the certificate presented is "netwitness" so you will need to modify the host file and add the alias netwitness to the entry in order for the ui to be able to access the file.
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-10-24 12:49 PM
Since you say you're using a custom certificate, and not the self-signed, OOTB "netwitness” certificate, your connection URL will need to use the CN of your custom cert, in addition to the directory Miha Mesojedec mentions:
The CSV in the directory:
The CN of my custom cert:
And putting those together for the connection URL in the feed wizard:
You can also refer to Eric Partington's blog post that describes how to set this up.
HTH
Mr. Mongo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-11-01 04:59 AM
Thankyou for taking time to revert back on my query, I have tried all the mentioned option but still having the same issue.
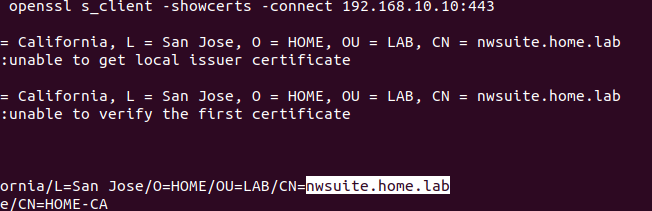
But getting below error which is strange when I checked my server certificate with the given openssl command
verify error:num=19:self signed certificate in certificate chain
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-11-01 05:04 AM
One more observation if i run the same command with -CAfile followed by path where my custom certificate is stored then I dont see any error and it returns - Verify return code: 0 (ok)
openssl s_client -connect <mysanode cn name>:443 -CAfile /etc/pki/nw/web/web-server-cert.pem
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-11-01 12:56 PM
Have you imported your custom server certificate into the java keystore on the Admin server?
You can use the instructions here as a good guide: https://community.rsa.com/docs/DOC-80984 (start at bullet #6 in the "Export the NetWitness Endpoint SSL Certificate”).
Just make sure to give your cert a different alias than what's in those instructions.
Mr. Mongo
- Mark as New
- Bookmark
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
2018-11-02 03:52 AM
Bingo! that resolved the issue... Thank You Joshua and others for helping me out